Switching 101 - DHCP, VLAN/tagging, NAT
Yay, I got my first switch ever! (And I'm not talking about the Nintendo one, that one was easy to figure out!)
So Cable Modem > ISP Cheap Router > Switch
For the sake of being clear, here's how I filled my ports:
1/0/1: ISP router (I need to change that, it's slow as hell)
1/0/2: (RESERVED) LAG w/ port 1 with future router
1/0/3: NAS
1/0/4: (RESERVED) NAS LAG
1/0/5: EAP245
1/0/6: (RESERVED) Future AP
1/0/7: Home-Assistant
1/0/8: (RESERVED) Testing OpenWRT on Pi
----
1/0/9: VoIP Box
1/0/11: PC 1
1/0/12: PC 2
I change the VLAN 1 interface IP to 192.168.0.2 to avoid conflict with the router and access the switch without a static IP.
At first I thought I could use the built-in DHCP server to assign IPs to my devices and just use the router for NATing, but someone on Reddit told me that it doesn't work like that.
Note that I spent 6 hours and 15 resets, trying stuff out, the manual on one screen and my cellphone in my hand. I played a lot with tagging and DHCP, but didn't get anything good (read: working)
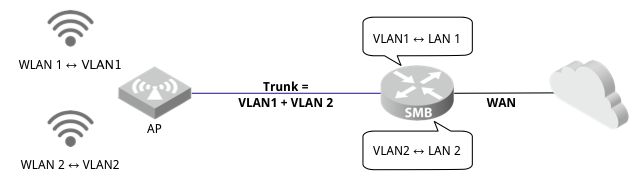
I created VLAN 49 with 1/0/1,1/0/9 for my VoIP. (both untagged). I'm not sure I understand the tagging thing even after some research.
The mian things I'd like to accomplish is:
- I'd like to create a VLAN with a public access point from the EAP245, isolated from the rest of the network;
- Another that can only access my Home-Assistant server for IoT devices (No internet for IoT but the HA server needs internet).
- Make things secure: I'd like the VoIP to be isolated, everything IoT to have no internet, guest wifi to only have WAN access, etc
- Eventually I'll get a "cheap" ~450 CAD Qotom router, but right now the router I have range between 20% and 100% CPU usage. Is there any way I can lighten it's workload?
Sidenote, my "older" router, a Netgear, died two weeks ago. After nearly 2 weeks of research, I love the TP-Link interface (thanks because openwrt is not compatible with the AP). the range of the EAP245 is awesome (I compared a lot of AP)
Best wishes