Connection between T2500G and T2600G with new GUI
Hello everybody,
I have a minor problem with my current TP links.
Exist the following VLANs
VLAN; 1 (System VLAN); 10; 90; 100; 110 Intern (XXX.XXX.122.XXX); 120; 200; 210
All T2500 switches are connected with type "trunk" and the system VLAN "1" via SFP module and fiber optic cable, communication with each other works. All VLANs were set to tagged on the ports of the fiber optic cables and untagged to the respective ports destined for the VLAN
There are a total of three T2500G 8MPS and one T2600G 28MPS.
On the T2600G 28MPS the LWL arrives on the SFP1 (port 25).
Since here the new GUI of TP Link is implemented on the device, I am a bit helpless.
Where the basic configuration should fit so far, I pulled the switch into the network of other switches.
The PVID is also the "1" (VLAN ID: 1 = System VLAN, tagged on port 25) - Ingress Checking is Enabled - Frame Types is set to "Admit All".
I've already tried something back and forth there but unfortunately without success, I can neither ping from my above switch with the IP "XXX.XXX.122.247" to the IP "XXX.XXX.122.248" and backward.
Have I somewhere a thinking error or so?
Has anyone here any advice or could help me there?
Here i have some pics from the Config:
Switch-1 (XXX.XXX.122.247)
 and..
and..
 And Switch-2 (XXX.XXX.122.248)
And Switch-2 (XXX.XXX.122.248)
 and..
and..
 Of course, even the cable or the SFP module was once exchanged with another to rule out a defect of this.
Many thanks
greeting
Dominik
Of course, even the cable or the SFP module was once exchanged with another to rule out a defect of this.
Many thanks
greeting
Dominik- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
@Dominik-R, in my opinion the setup is a bit »chaotic«. On the T2500G-10MPS your untagged ports (e.g. 1/0/1 to 1/0/6) are members of more than one VLAN (110, 1) making them trunk ports with PVID 110. On the T2600G-28TS ports 1/0/18 to 1/0/24 are access ports (member of only one VLAN, namely the Default VLAN 1) with PVID 1.
Ingress traffic on T2600G-28TS, say on port 1/0/18, gets tagged wit VID 1, is forwarded to T2500G-10MPS which wil remove the tag on trunk ports 1/0/1 to 1/0/6 on egress (due to the »GENERAL« setting), but tags the reply with VID 110, forwards it to the T2600G-28TS where it is dropped because neither 1/0/18 nor any other access port is a member of VLAN 110 according to your screenshot.
This is an (incomplete) asymmetric VLAN setup using the Default VLAN, so all VLANs share a common broadcast domain which leads to VLAN leakage of layer 2 Ethernet frames for non-IP protocols. Is this by intention? If yes, access ports such as 1/0/18 need at least be members of VLANs 1 and 110, too.
Or in other words: Do you use isolated networks (separate broadcast domains) on each VLAN or do you want to share a single network over all VLANs (common broadcast domain)? Depending on the answer of this question more tips for a clean VLAN setup can be given. A network diagram would also be of much help here.
Regarding pings between the switches: the old web UI (at least on my T1600G) requires to set the switch's IP as a virtual interface assigned to the mgmt VLAN (10). The new web UI allows to set the switch's IP and the mgmt VLAN under »System → System Info → System IP«.
Check whether you have set the correct mgmt VLAN on both switches, but beware that if changing the mgmt VLAN to 10 you will lose connection to the web UI unless you have an access port which is member of VLAN 10, too. I can't see such a port on your screenshots.
- Copy Link
- Report Inappropriate Content
@R1D2 Thank you very much for the quick answer.
Sorry it was even a 10MPS from the T2500G.
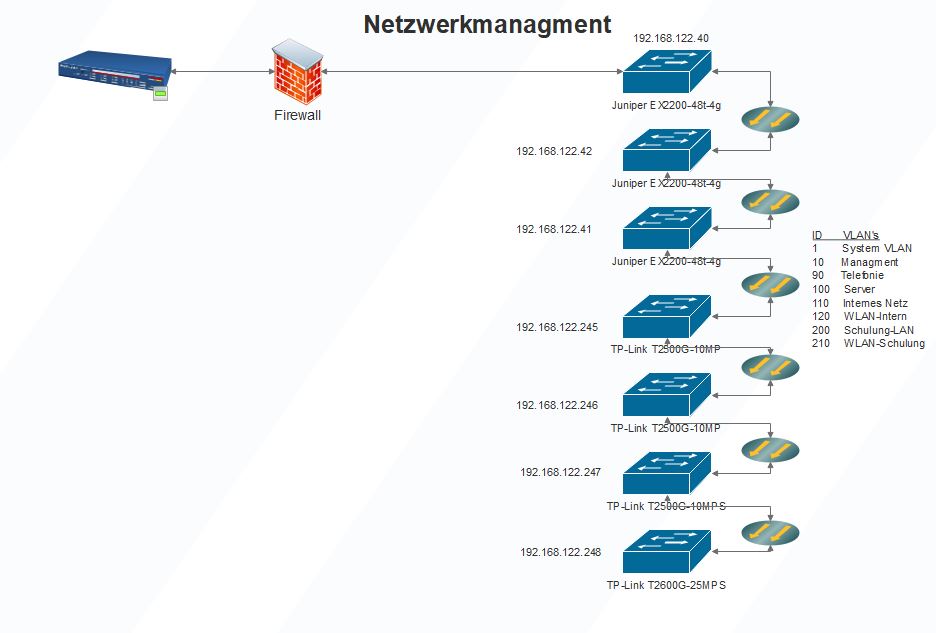
I once made a small plan with all the switches that are available.
The switches are all connected via fiber optic cables.
The internal network is the 192.168.122.XXX, which should be transported through all switches.
On the new switch T2600G the access points EAP225 are to be operated (PVID: 110).
My problem is really setting the ports to tagged or untagged. At the switches T2500G to the T2600G.
As far as I understand, I have to tag ports 9 and 10 of the T2500G for the VLAN 110 (internal)?
In port config, ports 9 and 10 would be trunk and with PVID 110, right?
At the T2600G I only have the VLAN1 Static with the IP address 192.168.122.248 under the "L3 Features" at Interface.
Under "L2 Features" -> VLAN I created all VLANS as shown in the topology.
Under port config with port 1/0/25 (SFP module fiber cable) I set the PVID to 110, Ingress Checking Enabled - Acceptable Frame Types "Admit All", right?
The VLAN's should be transported over all switches to the last switch.
Then the respective ports are assigned to the switches in the same way as the devices are connected there. For example, the AP's are connected to the switch 192.168.122.246 there. There I set ports 2 - 7 to untagged (PVID: 110 internal network) and ports 9 and 10 to tagged again.
This is what I have done with all TP-Link switches so far.
So that I can understand this once again, if I only want to set a VLAN to a certain port then I set it to Access?
If I want to transport several VLAN's over one port then I have to set this to trunk?
Thank you for your help, it's a bit stupid at the moment because some of our devices are standing still.
Greetings
Dominik
- Copy Link
- Report Inappropriate Content
Dominik-R wrote
So that I can understand this once again, if I only want to set a VLAN to a certain port then I set it to Access?
If I want to transport several VLAN's over one port then I have to set this to trunk?
Yes. Forget the »ACCESS«, »GENERAL«, »TRUNK« settings in the old web UI for a moment, I'll come back to them later.
First, terminology isn't standardized in 802.1Q for terms like »Default VLAN« or »access port« or »trunk port«.
According to the standard, a port can be a member of at least one or more VLANs. The Port VLAN ID (PVID) assigns a port's membership to one VLAN, I call this the Primary VLAN (do not confound with QinQ which also uses this term, but for different things). The port can still be a member of more VLANs, such as 1 and 110 in your example. I call this Secondary VLANs just to have a term for them.
Now, what makes a port a so-called access port is the membership of the port in exactly one VLAN. In this case the PVID must be the same VLAN ID as the primary VLAN.
As soon as a port is a member of more than only one VLAN, it becomes what usually is called a trunk port. It doesn't matter at this point whether the port is tagged or untagged, but to keep the VLAN ID intact on egress on a trunk link (to send traffic from a switch to another switch for example) the Ethernet frames must be tagged.
Now, if you want to connect a laptop/PC or other non-VLAN-aware device to the switch, you would use an access port (member of only one VLAN) or a trunk port (member of a primary and secondary VLANs). In the latter case, the device needs untagged frames on egress and sends untagged frames on ingress.
In old firmware this was controlled by »GENERAL« and »TRUNK«. A »GENERAL« port allowed for the port's membership in more than one VLAN – still a trunk – while stripping VLAN ID tags on egress, while a »TRUNK« port allowed the for the port to be a member in more VLANs – obviously a trunk –, too, but it did not strip the VLAN ID tags, thus keeping it intact.
I modern firmwares you can assign the port as tagged or untagged in the VLAN membership settings to control stripping tags on egress even on trunk ports.
On switches from other vendors, trunk ports might strip the VLAN ID on egress for (only) the VLAN defined in the PVID of the trunk port in question while keeping the VLAN tags intact if they differ from the PVID (check this behavior on your Juniper switch). On TP-Link switches you control tagging/untagging as described above.
Rules of thumb for setting up VLANs:
- Inside the switch there is no untagged traffic. Every frame either is already tagged (trunk) or gets tagged by the switch on ingress (PVID).
- The Default (or System or Native) VLAN is often used for so-called untagged traffic. Due to 1) a frame must be tagged. Likewise, any port must belong to at least one VLAN, so in factory settings all ports are members of the VLAN 1, which is the System VLAN in TP-Link's terminology. That's just a convention, you don't need to use it this way. You can define your own Default VLAN to be different from what TP-Link calls System VLAN, for example you can set it to VLAN ID 2 or 100 or whatever.
- Assign access ports always to only one VLAN. The PVID must be set to this VLAN ID, since it instructs the switch to tag untagged traffic from the end-user device with this ID.
- Assign trunk ports to any VLAN membership it should be part of. Set the PVID to the ID you want to have untagged traffic tagged with. Usually, on trunks only tagged traffic appears (there might be exceptions as mentioned above for trunk ports).
- VLANs must be terminated to communicate with end-user devices (switch untaggs traffic on untagged ports) or to forward frames to the network associated with the VLAN (router untaggs traffic for further processing inside the network). Form the outside perspective VLANs don't exist at all, just different networks. VLANs only exist inside VLAN-aware devices (routers, switches, servers etc.) and on the cables connecting those devices, so you can deploy different logical networks using the same physical devices/cables.
For example, my policy is to use the Default VLAN for network 192.168.0.0/24 and assign it only unused ports for new devices I have not (yet) configured. Thus, my Default VLAN allows me to connect TP-Link devices with factory IP 192.168.0.x to any free port of any switch for initial configuration. My management VLAN is 100, my internal backbone VLAN is 2 and there are still more VLANs for different use cases which are present only on the switches where I need them.
Now for your config:
What still confuses me is your mgmt VLAN 10, while you are managing the switches through VLAN 1. But I assume VLAN 1 for mgmt.
I recommend to set a trunk port's membership always to all VLANs you want to forward to other switches. The ports used to inter-connect switches are always tagged. PVID doesn't matter if there are no untagged frames on trunk links, but it must be a VLAN ID of one of the VLANs the port is a member of. Set it to ID 1 if you want.
Access ports should be member of only one VLAN, the PVID is the same as the VLAN ID the port is a member of.
Reserve an access port on one of the switches to be member of VLAN 1 / PVID 1 for access to the mgmt VLAN from a laptop/PC (or use Inter-VLAN routing) so you can access the switch's web UI. Until you have deployed Inter-VLAN routing use a static IP from the 192.168.122.0 network on your laptop/PC for access to the switch.
Enable »Ingress Checking« to have the switch check VLAN tags and to forward only frames tagged with a VLAN ID the port is a member of it. Frames on trunk links are always tagged usually. Frames on access ports get tagged with PVID.
Set »Acceptable Frame Types« to »Admit All« on access ports (admit untagged frames) and to »Tagged Only« on trunk ports (if you're sure there are no untagged frames on trunk links). In my uderstanding, this setting defines whether to either drop untagged frames on trunks or to tag them with the PVID.
BTW: It's not recommended to daisy-chain more than two or three switches, a star topology would be better.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 2289
Replies: 3
Voters 0
No one has voted for it yet.