SG2008P - How to getting the switch into Management VLAN
Hi, I want to separate my network into different VLANs and now I am humbling over how I get the switch in my Management VLAN without loosing access temporarily.
My setup: My router is a FritzBox 5690 pro (no management). Currently the switch is available under https://192.168.178.171 which is gathered from the FritzBox via DHCP.
I configured in the switch's menu under L3 Features -> Interface an addidtional one:
| Interface ID | IP Address Mode | IP Address | Subnet Mask | Interface Name | Status | Operation |
|---|
| VLAN10 |
Static |
192.168.10.14 |
255.255.255.0 |
Mgmt Interface Switch |
Up |
|
The uplink Port 8 to the Fritzbox is configured to be in the VLAN10 (tagged) and VLAN1 (untagged). The Port 7 to my homeserver where my vlanrouter resides in a Proxmox Container is also tagged with VLAN10.
The vlanrouter contains Forwarding iptables from 192.168.178.0/24 to the VLAN 10 network.
A route from my PC to the gateway of VLAN 10 exists.
I can successful ping from my management PC the 192.168.10.14. But if I want to reach 192.168.10.14 via the browser (http and https), I can't access the Management IF.
I also have setup omada LXC on my proxmox and can successful perform a configuration. Anyway, the omada controller which is also in the management VLAN IF is not finding the switch although I have set an addiational interface (see above).
Questions:
What is best practice to protect the Management switch IF?
Do you have any ideas why a ping is coming through but the webserver isnt reachable via 10.14?
Any ideas why omada controller can't find my switch?
Thanks for your help.
PS: I will deliver the iptables as soon as I have access to my home network again.
Bernd
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
In standalone mode Omada switches do not have a default gateway setting. For the Switch SVI on the management vlan 10 to be able to route its response back to you, you will need to add a static route on the switch 0.0.0.0 / 0.0.0.0 > Fritzbox vlan 10 gateway IP (or wherever you want to route it to)
- Copy Link
- Report Inappropriate Content
I applied exactly this route, but still the same, no access from 192.168.10.14 to the management if. The AI says: "Only the primary Management IP supports web access. Additional VLAN interfaces can be used for routing and ping, but not management access." https://community.tp-link.com/en/business/forum/topic/595460 and https://www.tp-link.com/de/support/faq/3534/
If this would be true, I am wondering why the management offers this and how I can securly operate the switch. The route I applied look like this:
| Protocol | Destination Network | Next Hop | Distance | Metric | Interface Name |
|---|
|
Static
|
0.0.0.0/0
|
192.168.10.1
|
1
|
0
|
VLAN10
|
|
Connected
|
192.168.10.0/24
|
192.168.10.14
|
0
|
1
|
VLAN10
|
|
Connected
|
192.168.178.0/24
|
192.168.178.171
|
0
|
1
|
VLAN1
|
This is from my admin PC:
PS C:\Users\bernd> curl -v https://192.168.10.14
* Trying 192.168.10.14:443...
* schannel: disabled automatic use of client certificate
* schannel: using IP address, SNI is not supported by OS.
* ALPN: curl offers http/1.1
* Recv failure: Connection was reset
* schannel: failed to receive handshake, SSL/TLS connection failed
* closing connection #0
curl: (35) Recv failure: Connection was reset
PS C:\Users\bernd> ping 192.168.10.14
Ping wird ausgeführt für 192.168.10.14 mit 32 Bytes Daten:
Antwort von 192.168.10.14: Bytes=32 Zeit=2ms TTL=64
Antwort von 192.168.10.14: Bytes=32 Zeit=1ms TTL=64
Antwort von 192.168.10.14: Bytes=32 Zeit=2ms TTL=64
Antwort von 192.168.10.14: Bytes=32 Zeit=1ms TTL=64
Ping-Statistik für 192.168.10.14:
Pakete: Gesendet = 4, Empfangen = 4, Verloren = 0
(0% Verlust),
Ca. Zeitangaben in Millisek.:
Minimum = 1ms, Maximum = 2ms, Mittelwert = 1ms
PS C:\Users\bernd>
As you can see, ping is workin, the curl command not. These are my relevant forwarding rules:
vlanadmin@vlanrouter:~$ sudo iptables -L FORWARD -v -n --line-numbers
[sudo] password for vlanadmin:
Chain FORWARD (policy ACCEPT 550 packets, 123K bytes)
num pkts bytes target prot opt in out source destination
1 2666K 2138M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED /* Allow return traffic for established connections */
4 28 2223 ACCEPT tcp -- * * 192.168.178.0/24 192.168.10.13 tcp dpt:22 /* TEMPORARY SSH Admin→omada (FB-Netz) */
6 0 0 ACCEPT udp -- * * 192.168.10.0/24 192.168.178.101 udp dpt:53 /* TEMPORARY DNS VLAN10→Pi-hole (FB-Netz) */
7 0 0 ACCEPT udp -- * * 192.168.30.0/24 192.168.178.101 udp dpt:53 /* TEMPORARY DNS VLAN30→Pi-hole (FB-Netz) */
12 40 2400 ACCEPT tcp -- * * 192.168.10.0/24 0.0.0.0/0 tcp dpt:80 /* HTTP VLAN10→Internet */
13 63 4452 ACCEPT tcp -- * * 192.168.10.0/24 0.0.0.0/0 tcp dpt:443 /* HTTPS VLAN10→Internet */
22 24 1440 ACCEPT icmp -- * * 192.168.178.0/24 192.168.10.14 /* TEMPORARY Switch ICMP WebUI (FB-Netz) */
23 150 7800 ACCEPT tcp -- * * 192.168.178.0/24 192.168.10.14 tcp dpt:443 /* TEMPORARY Switch HTTPS WebUI (FB-Netz) */
24 41 2132 ACCEPT tcp -- * * 192.168.178.0/24 192.168.10.14 tcp dpt:80 /* TEMPORARY Switch HTTP WebUI (FB-Netz) */
25 12502 2786K DROP all -- * * 192.168.10.0/24 0.0.0.0/0 /* Default deny from VLAN10 */
26 58 3040 DROP all -- * * 0.0.0.0/0 192.168.10.0/24 /* Default deny to VLAN10 */
And here is my VLAN Setup:
| VLAN ID | VLAN Name | Members | Operation |
|---|
|
|
1
|
System-VLAN
|
1/0/1-8
|
|
|
|
10
|
Management
|
1/0/7-8
|
|
|
|
|
|||
|
|
|
|||
|
|
The PVIDs of each port are in VLAN 1, My port 7 is the downlink to the homeserver, port 8 the uplink to the fritzbox which isn't able to understand VLANs.
- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
@GRL Yes, I did. I just double checked and can confirm:
Interface ID: 10
IP Address mode: Static
IP Address: .10.14
Admin Status: Enabled
Interface STatus Up
Line Protocol Status Up
- Copy Link
- Report Inappropriate Content
I dont have a 2008P in standalone mode to play about with, but you definitely can and should be able to reach the switch management page on all "Admin" set interfaces.
This is a non-management interface on one of my switches
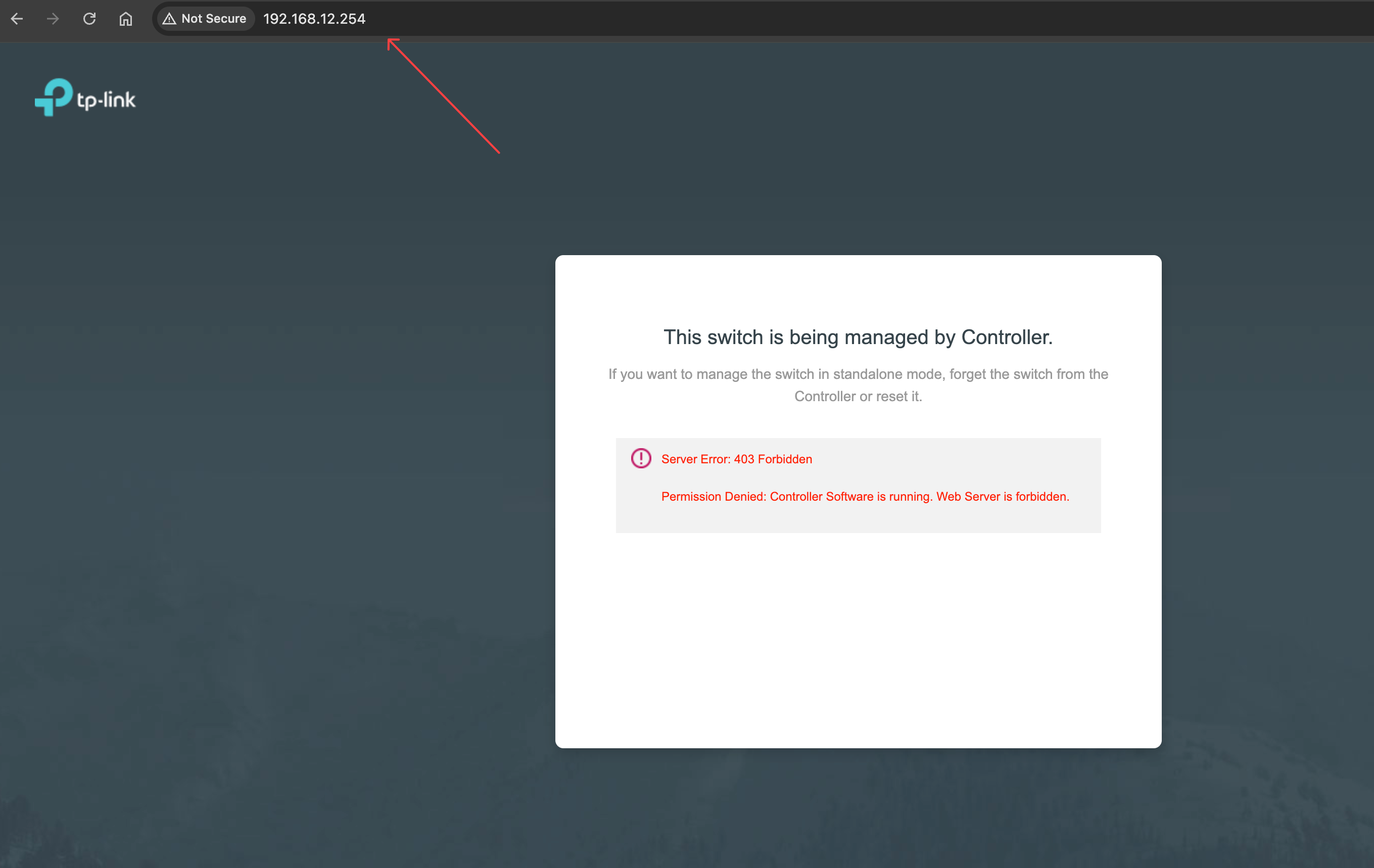
- Copy Link
- Report Inappropriate Content
@GRL I also enabled temporarily access via port 80 to exclude certificate problems, but it also don't work. You are absolutely sure that I should reach with my setup the admin page on both (in parallel), the
1. https://192.168.178.171 -> my Fritzbox net, which I want to disable as soon the admin interface is in the Management zone
2. https://192.168.10.14 -> my static ip in the admin zone.
If this is true, something blocks. What do you recommend? Remove temporarily the drop rules? Any hints to debug the situation?
- Copy Link
- Report Inappropriate Content
I can't believe it. Two NAT MASQERADE rules did the trick:
0 0 MASQUERADE tcp -- * * 192.168.178.0/24 192.168.10.14 tcp dpt:443
0 0 MASQUERADE tcp -- * * 192.168.178.0/24 192.168.10.14 tcp dpt:80
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 919
Replies: 8
Voters 0
No one has voted for it yet.
