Dynamic VLAN with EAP 783
Hello,
I have configured dynamic VLAN as explained in https://www.tp-link.com/us/support/faq/3152/ .
VLAN assignment does work with wired network and I get an IP Address.
VLAN assignment does *not* work on wireless network with EAP 783.
In tcpdump I see the AP does receive the Access-Accept packet with all attributes for dynamic VLAN assignment
but the mobile device times out and says "Cannot connect to WiFi".
Firmware Upgrade vom 1.0.7 to 1.0.14 did not have any effect.
Any hints what I can do?
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
@relvy Hello,
With help from the TP-Link Support the root problem has been found:
I use freeradius to do EAP-TTLS+PAP and offload PAP to a radius proxy belonging to my IdP (authentik).
As described in https://www.freeradius.org/documentation/freeradius-server/3.2.8/tutorials/eap-ttls.html the Access-Accept packet shall contain MPPE keys and the EAP-Message but that was not the case for me.
Why?
Because the radius proxy did not return any attributes.
Solution: I reconfigured freeradius to use ldap authentication belonging to my IdP (authentik).
Then I got the MPPE keys and the EAP-Message in the Access-Accept packet.
Then dynamic VLAN assignment works. Mobile Phone, Macbook's etc. can connect the SSID and access the network and internet.
- Copy Link
- Report Inappropriate Content
To understand the issue better, please give us the following info:
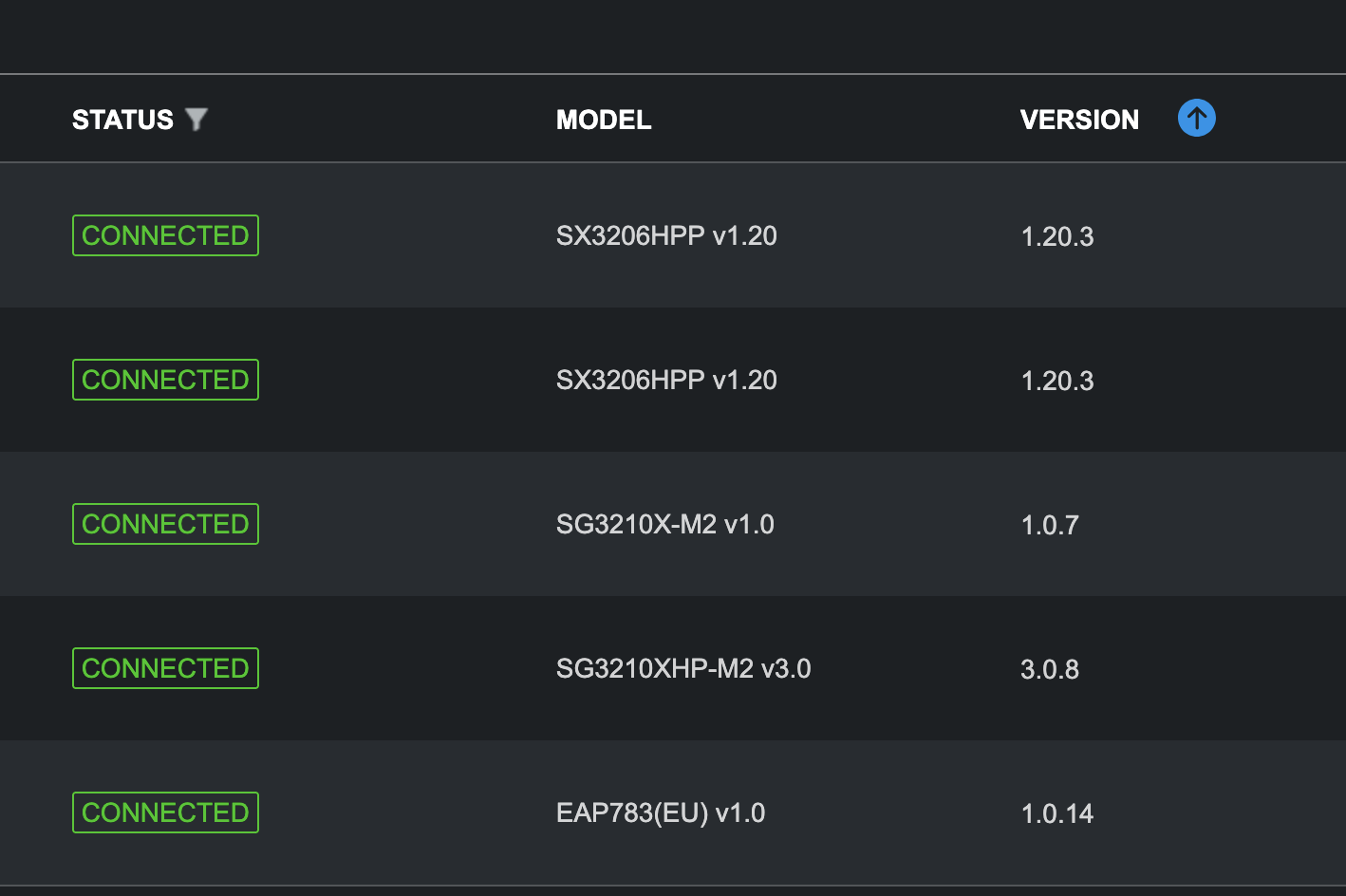
1. A screenshot of the Device page of your controller so we would know the models, versions of the Omada devices you are using;
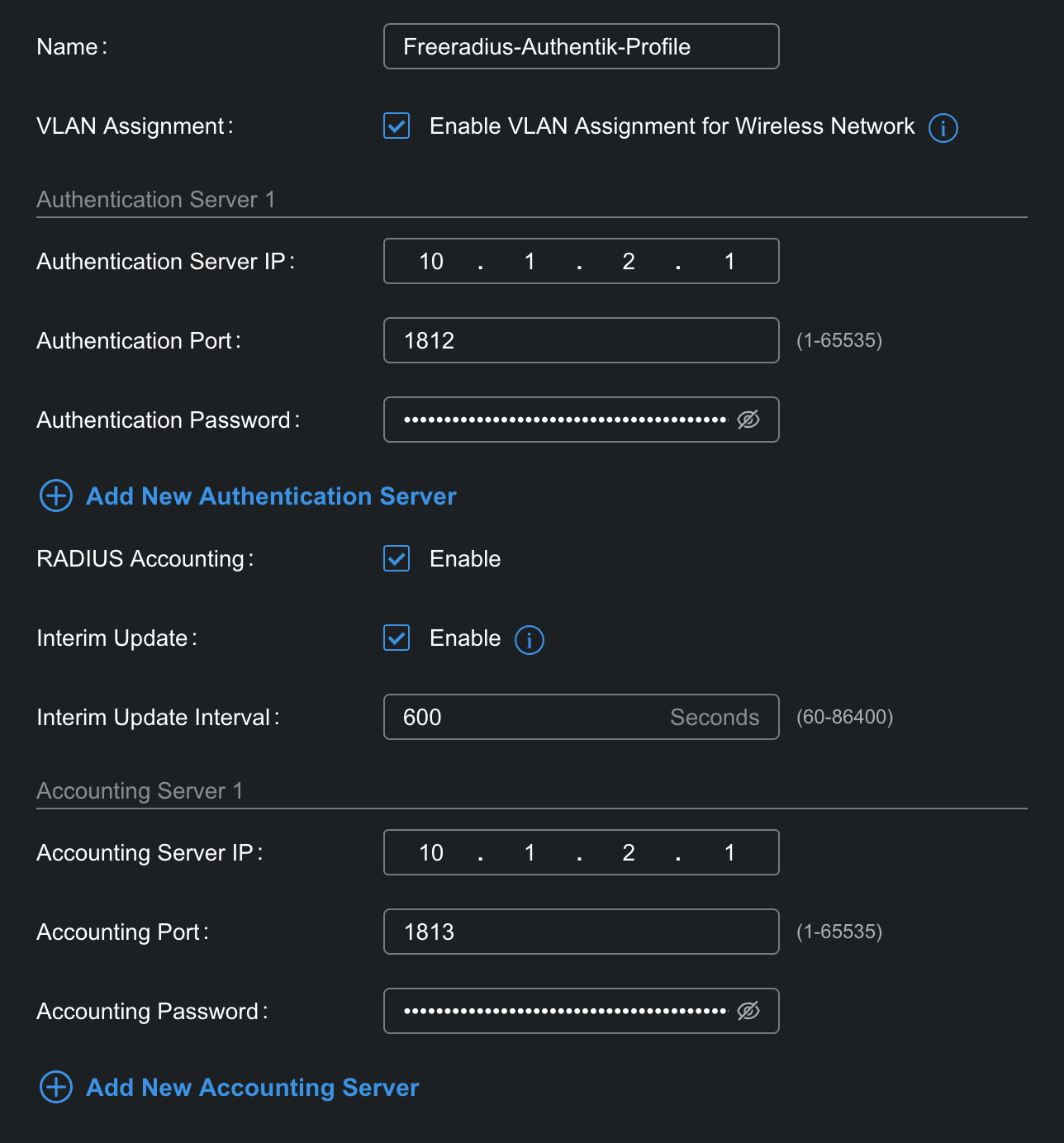
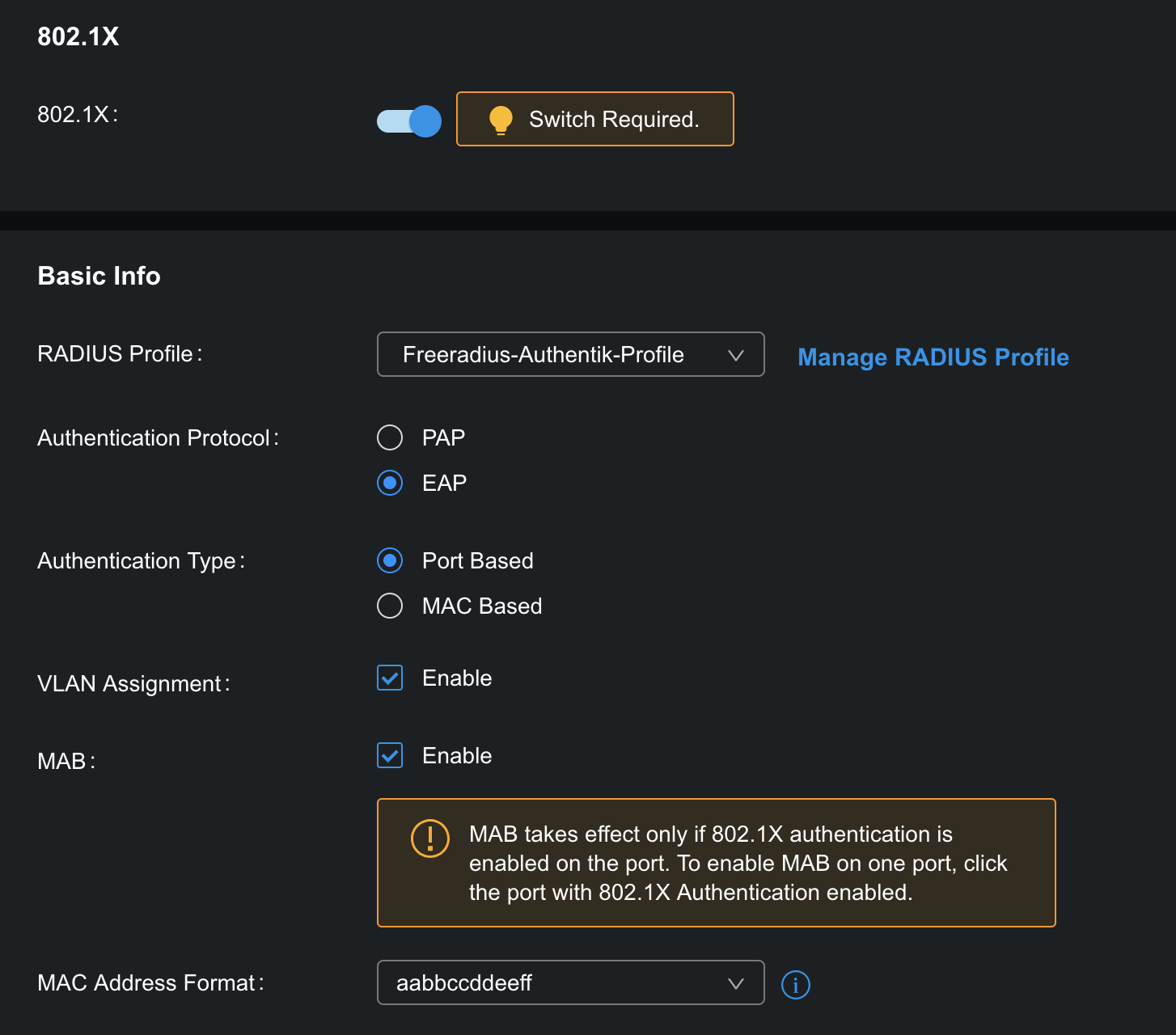
2. the screenshots of the config page mentioned in the FAQ;
3. What IP address will the wireless clients get?
4. Are you using an external Radius server?
5. the topology of the network.
You may have a look on the following guide to configure it with the controller built-in Radius server:
How to Configure Dynamic VLAN with the Built-in RADIUS Server of Omada SDN Controller via User Auth?
- Copy Link
- Report Inappropriate Content
Vincent-TP wrote
To understand the issue better, please give us the following info:
1. A screenshot of the Device page of your controller so we would know the models, versions of the Omada devices you are using;
2. the screenshots of the config page mentioned in the FAQ;
3. What IP address will the wireless clients get?
4. Are you using an external Radius server?
5. the topology of the network.
You may have a look on the following guide to configure it with the controller built-in Radius server:
How to Configure Dynamic VLAN with the Built-in RADIUS Server of Omada SDN Controller via User Auth?
Screenshot of my devices:
2. Screenshot of radius config page:
3. DHCP Address depending on the VLAN assigned to them.
4. Yes, Freeradius configured to do EAP-TTLS+PAP.
5. Topology
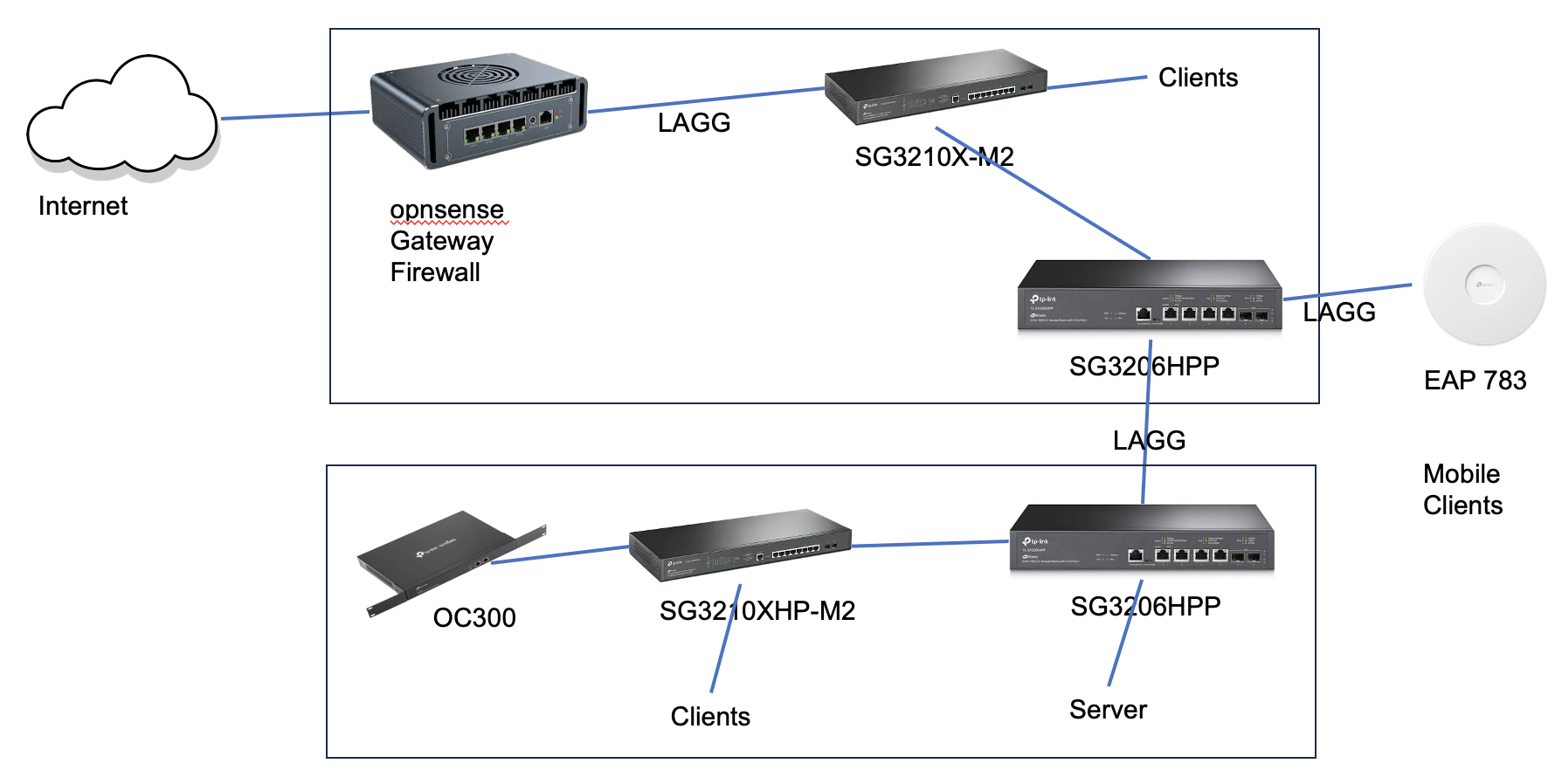
- Copy Link
- Report Inappropriate Content
Hi @relvy
Thanks for the reply.
3. DHCP Address depending on the VLAN assigned to them.
>>> Since the devices are receiving IP addresses from the correct VLAN, when you mention the wireless clients "aren’t working," do you specifically mean: They cannot access the internet?
Please have a look on the note for Enable VLAN Assignment for Wireless Network:
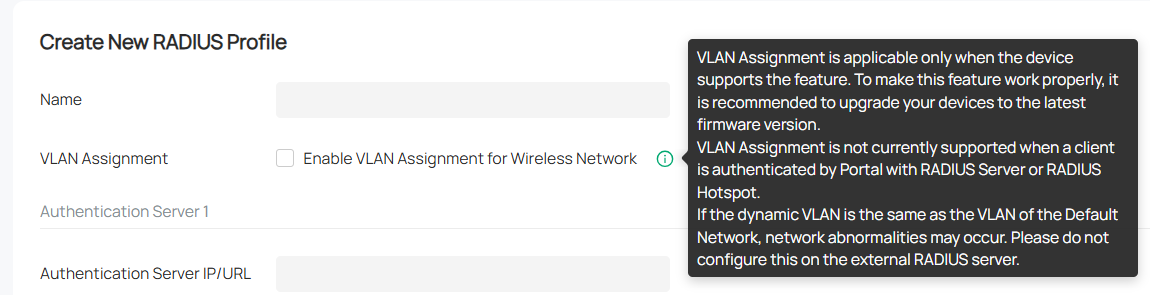
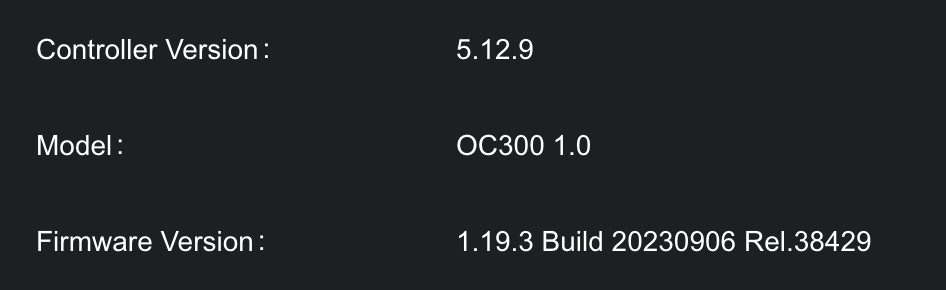
1. Your controller OC300 is working with a firmware from 2023, which is really old. Please update the controller to the latest one;
2. Do you configure Portal with RADIUS for the wireless network?
- Copy Link
- Report Inappropriate Content
Vincent-TP wrote
Hi @relvy
Thanks for the reply.
3. DHCP Address depending on the VLAN assigned to them.
>>> Since the devices are receiving IP addresses from the correct VLAN, when you mention the wireless clients "aren’t working," do you specifically mean: They cannot access the internet?
Please have a look on the note for Enable VLAN Assignment for Wireless Network:
1. Your controller OC300 is working with a firmware from 2023, which is really old. Please update the controller to the latest one;
2. Do you configure Portal with RADIUS for the wireless network?
3. DHCP Address depending on the VLAN assigned to them.
>>> Since the devices are receiving IP addresses from the correct VLAN, when you mention the wireless clients "aren’t working," do you specifically mean: They cannot access the internet?
The wired clients do get DHCP address from the correct VLAN after successful dot1x authentication.
The wireless clients do not get assigned to a VLAN. I see no DHCP traffic.
I see the EAP does receive the Access-Accept packet with all attributes for dynamic VLAN assignment.
1. Your controller OC300 is working with a firmware from 2023, which is really old. Please update the controller to the latest one;
The button "Check for Upgrade" gives

So I will do manual update.
For EU latest english firmware
https://static.tp-link.com/upload/firmware/2025/202504/20250401/OC300(UN)_v1_1.29.5%20Build%2020250325.zip
should be good?
2. Do you configure Portal with RADIUS for the wireless network?
No, I don't.
- Copy Link
- Report Inappropriate Content
Hi @relvy
Thanks for the info.
https://static.tp-link.com/upload/firmware/2025/202504/20250401/OC300(UN)_v1_1.29.5%20Build%2020250325.zip
Yes, this is the latest version.
- Copy Link
- Report Inappropriate Content
OC300 manual update successful:
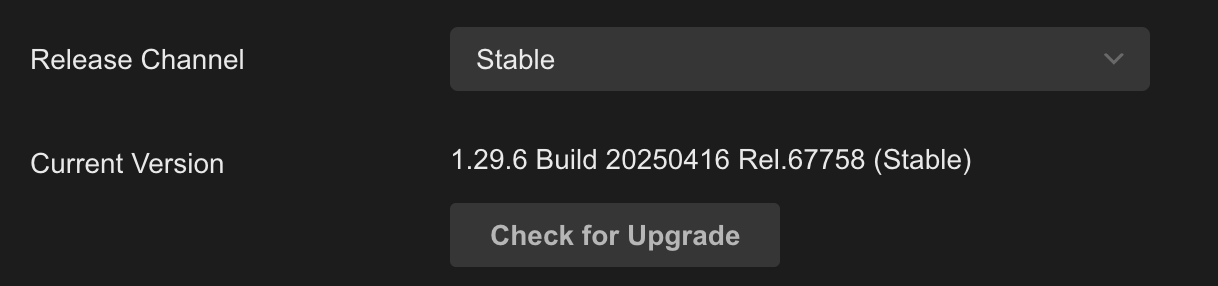
Now the "Check for Upgrade" works, too.
Unfortunately, the OC300 update does not have any effect on the dynamic VLAN settings on EAP.
The problem remains.
- Copy Link
- Report Inappropriate Content
Hi @relvy
Sorry to hear that.
What's the profile of the LAG port on the switch configured, is it the default profile ALL?
Did you create corresponding VLAN SSIDs for the EAP??
Did the config work correctly before? or never worked?
- Copy Link
- Report Inappropriate Content
@Vincent-TP
> What's the profile of the LAG port on the switch configured, is it the default profile ALL?
That LAG is on port 3 and port 4. It has the default profile ALL.
The ALL profile has the system vlan 1 as native untagged network.
All other VLAN networks are tagged.
> Did you create corresponding VLAN SSIDs for the EAP??
I created one SSID with WPA-Enterprise and radius for all VLANs.
The mobile client is supposed to land in the corresponding VLAN as told by radius access-accept packet.
From mobile client perspective the EAP behaves as it would get an access-reject and never tells the client.
In reality the EAP receives an access-accept packet and it appears to throw the packet away.
> Did the config work correctly before? or never worked?
It never worked before. It is a complete new setup.
For the wired clients I also use the default ALL profile with 802.1x enabled ports.
After successful authentication the switch assigns the correct VLAN as native untagged network on that port.
For wired clients I increased the radius timeout value from 5 to 9 and retransmit value from 2 to 3 via device CLI.
With this I get this behaviour:
switch -> radius: access-request id 53
switch -> radius: access-request id 53
radius -> switch: access-accept id 53
The switch puts the port into state authorized with correct VLAN.
Without this I had this behaviour:
switch -> radius: access-request id 53
switch -> radius: access-request id 54
radius -> switch: access-reject id 53
radius -> switch: access-accept id 54
The switch rejected the client and ignored the access-accept.
I had to do that with device CLI because I could not do that elsewhere. It would be nice to be able to do that in the radius profile settings.
I cannot do this for the EAP directly (no CLI support) but it appears the EAP works together with the switch to get the same result with EAP.
- Copy Link
- Report Inappropriate Content
I believe this is incorrect
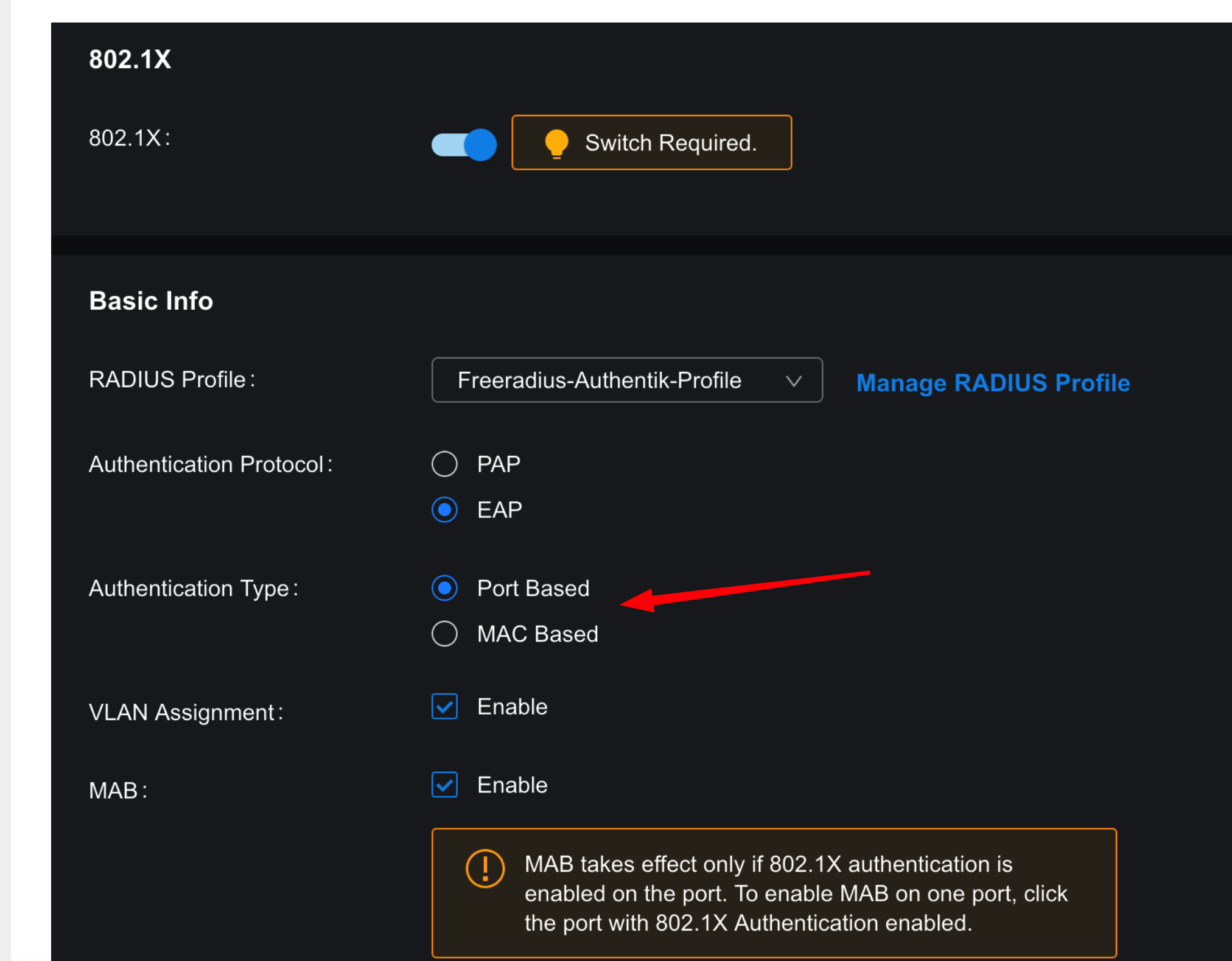
Port Based will lock a switch port to the vlan of the first authenticated client and set the vlan as untagged on that port, regardless of what else is downstream of that port. I think you need MAC based
- Copy Link
- Report Inappropriate Content
@GRL
> Port Based will lock a switch port to the vlan of the first authenticated client and set the vlan as untagged on that port, regardless of what else is downstream of that port. I think you need MAC based.
The ports where the wired clients get connected to have 802.1x enabled.
The ports where the EAP and Servers are connected to do not have 802.1x enabled.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 1879
Replies: 21
Voters 0
No one has voted for it yet.
