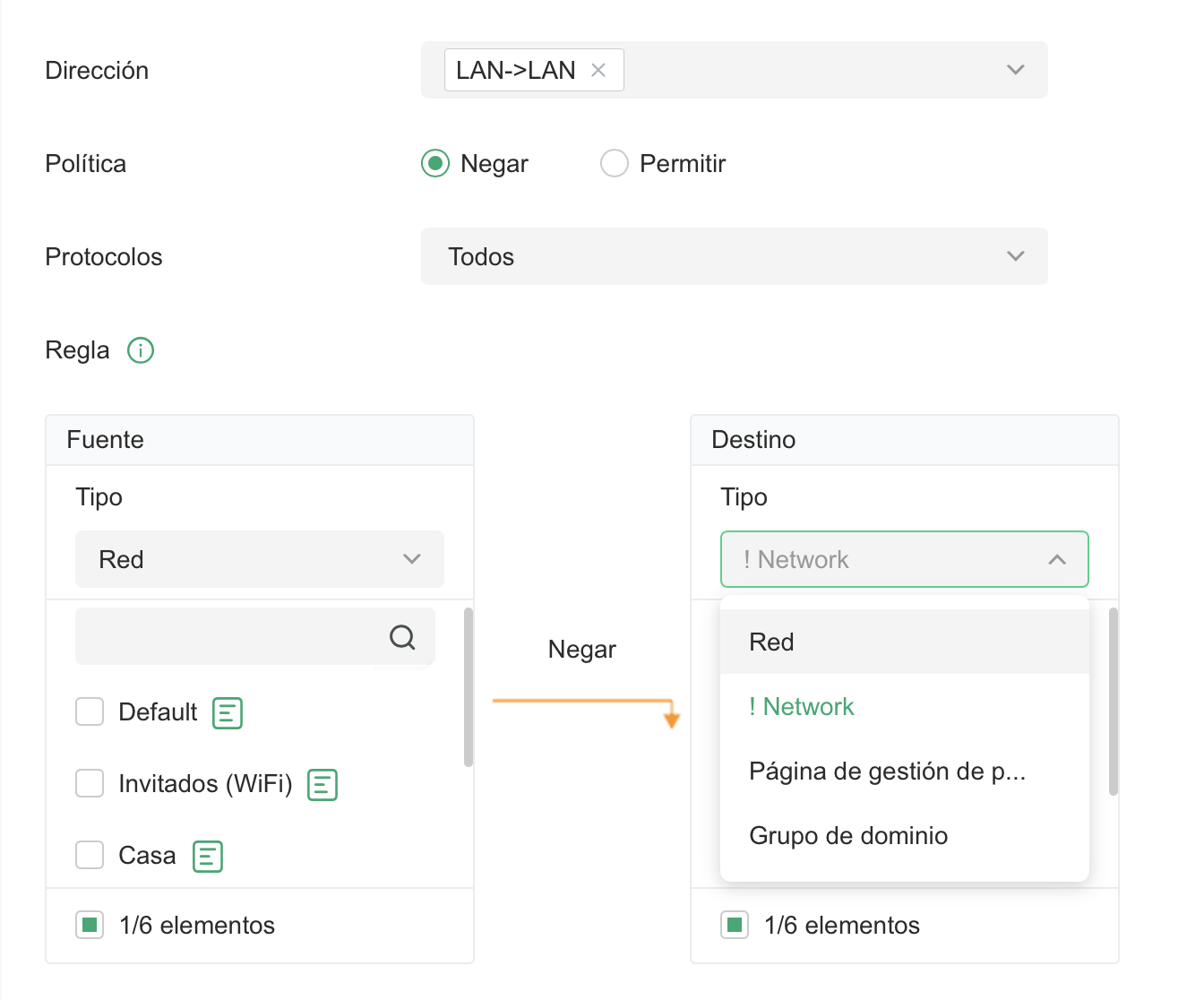
Gateway ACL, LAN->LAN, IP-Port Needed.
Gateway ACL, LAN->LAN, IP-Port Needed.
At the moment, Gateway ACL rules don’t support defining groups based on IP and port combinations or similar criteria.
I believe this is important for enabling communication between isolated VLANs, especially for scenarios like accessing an internal DNS server.
At the moment, it seems only full networks can be defined, which limits flexibility.
Could someone advise on how to allow devices in an isolated IoT VLAN to reach a DNS server located in the main VLAN? Is there an alternative approach to achieve this?
By “isolated,” I mean there’s a gateway ACL blocking traffic from the IoT VLAN to any other VLAN, which currently prevents access to the DNS server in the main network.
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
Did you finally solve the issue with the DNS server? I just tested something that might be a solution for some users. A local DNS server has been set up on a Synology NAS. The NAS has two LAN ports and the second port was configured on a /30 network. Being a /30 network, there are only two usable IP addresses, one for the gateway (192.168.x.1) and one for the NAS (192.168.x.2). By default, the Omada gateways allow inter-VLAN access so any device on any VLAN can reach the DNS server via its IP address.
The NAS has its own firewall rules so a firewall rule was created to allow incoming traffic on port 53 and denying everything else. No additional ACL rules in the Omada devices are needed.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 7
Views: 1137
Replies: 11
