Controller v6 new feature - Isolated VLANs - goes a bit too far in isolating them
Just a bit of feedback, posting here in gateways since its gateway specific
Omada v6 allows us to set an isolated vlan - great, saves making gateway and switch rules to prevent inter-vlan for those networks.......BUT
In my opinion it goes a bit too far in isolating them. It also prevents them reaching out to anything that isnt the gateway / internet - i test isolated a vlan on my public networks gateway, and it no longer allowed the use of that gateways static route i have set to a printer on my main network. As soon as i un-isolated the network i was testing, the static route was able to be used by that vlan again.
I think there are plenty of scenarios where users would want a vlan isolated from other vlans, but i dont think that should extend to isolating it from other things like routes.
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
WRT the static route issue, this may be related. I asked about the priority of the VLAN isolation option over ACLs in this post. The response was that ACLs take priority. I just tested this with the V6 controller update and it seems to be working OK. What I am getting at is that an ACL may be a workaround for a static route problem (until the problem is fixed).
In my case, I have a VoIP phone on a separate VLAN. I liked the idea of isolating the VLAN so I wouldn't have to include it in my various ACLs that deny inter-vlan routing. After isolation, I could no longer reach the phone's GUI. That was solved with a single ACL that allows my PC's private network to access the VoIP network. The rule does, in fact, override the isolation option.
- Copy Link
- Report Inappropriate Content
Interesting, but since the networks on my public vlan gateway are gateway interface only, i cant use a LAN<>LAN ACL to point to an IP_Group :-(
- Copy Link
- Report Inappropriate Content
I don't use IP groups here as I am only using gateway ACLs. For example, to get around a printer access problem, I simply put the printer (I only have 1 printer) on it's own VLAN with a /30 subnet. The only 2 useable IP addresses are assigned to the gateway and to the printer. As inter-VLAN routing is enabled by default on the gateway, all the VLANs that need access to the printer have it.
- Copy Link
- Report Inappropriate Content
In my case, the printer exists on a network on a different gateway that doesnt have a corresponding vlan on the public gateway, hence the static route. I would have to be able to add that IP as a LAN<>LAN IP group destination for the exception to work, which we cant do on gateway rules
I have just left it un-isolated and have its acces controlled in myprior way which works fine.
I have taken advantage of isolation & removal of old rules for the other networks on that gateway though!
- Copy Link
- Report Inappropriate Content
Hi @GRL
Static Route should have higher priority than isolated VLAN.
Would you please share with us some screenshots of your config, and some screenshots of the test result? This helps us fully understand the situation. Thanks.
- Copy Link
- Report Inappropriate Content
Sure
I seperated out my main physical building network into two sites - Main and Public. Main uses ER8411 as gateway on 1.3.2 and hosts all the switches, EAPs and has all the inter-vlan routing for the internal networks as hybrid gateway & switch routing. Public is an ER7206 v2 running 2.2.3 that has gateway hosted vlans for all the public access networks with matching vlan tags on a trunked port to my main switch
All the public access networks are switch only vlans on the main site so i can pipe those vlans around the switches and EAPs, and they are gateway only vlans on the public site.
hopefully that makes sense!
Public Gateway Site :
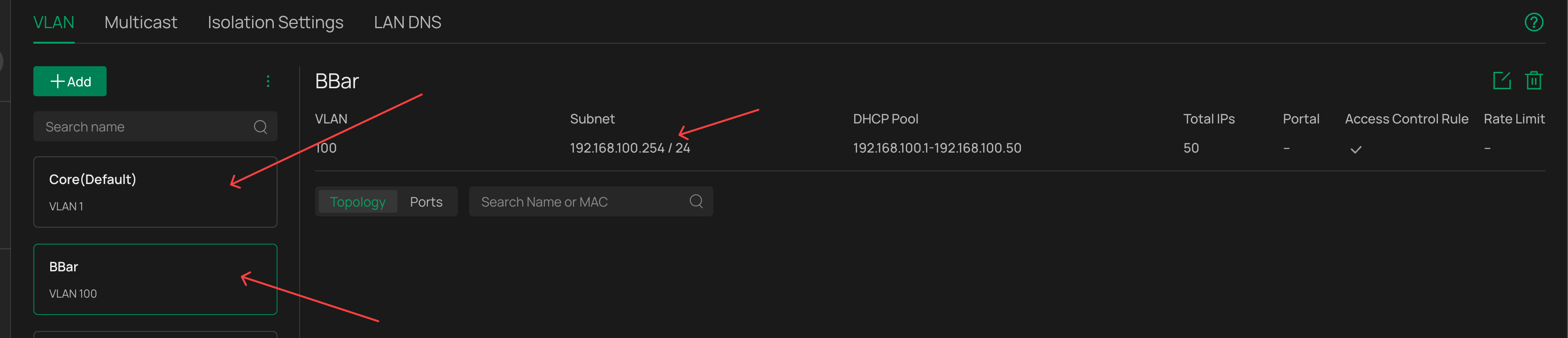
Networks - The one i was intending to isolate was "BBar" - note it IP range of 192.168.100.X
The Core network is my wider management vlan that connects it to the main network for omada control and the static route to and from the switch
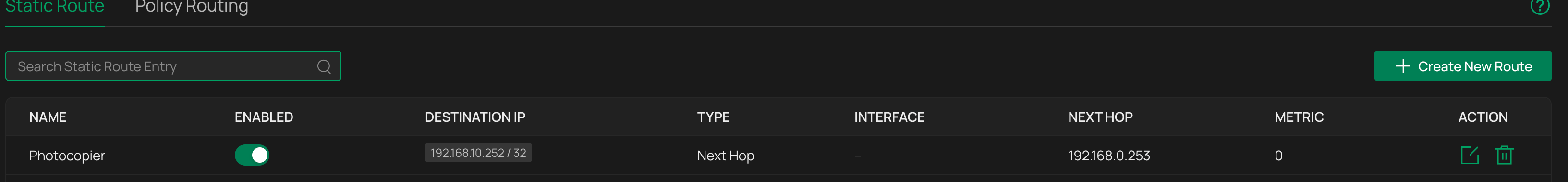
Public gateway static route for the printer on the main network - hops the single IP address to the main routing switch hosting the SVI for that vlan on the main site
On the main switch (the main site) - static route hops traffic destined back to the BBar network to the public gateway IP on the management vlan
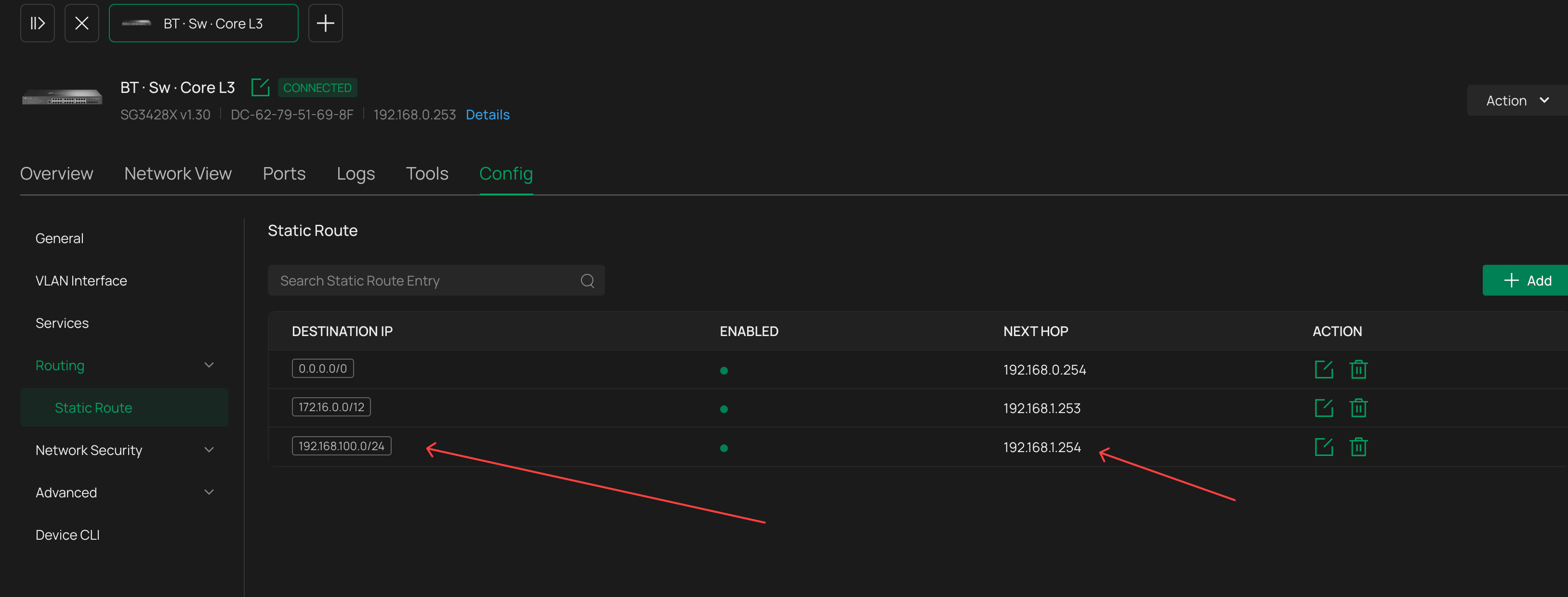
This all works perfectly, until i enabled VLAN Isolation on the BBar network on the public gateway site. Then, it just stops - no pinging the printer from the bbar network and the main site cant ping the bbar network from the printer IP
- Copy Link
- Report Inappropriate Content
Aside from the above i was playing around on a test network this evening and have a bit more feedback for anyone interested
VLAN isolation only happens at the gateway interface - L3 switch interfaces and L3 switch based routing are not effected. I can isolate one of my switch routed networks and it can still follow the switch ACLs and communicate with what i allow it to on other vlans.
I am kinda curious to see what happens if i isolate the management network (all my switch routing hops traffic to and from the gateway<>switch on this vlan) but it feels like thats the tempting big red button with a "NO" sticker on it haha
- Copy Link
- Report Inappropriate Content
Information
Helpful: 1
Views: 492
Replies: 7
