SG2218 using SHA-1 for SSH key signatures
I just discovered that my brand new TP-Link SG2218, running firmware released earlier this year, will only use SHA-1 signatures for SSH key-based authentication. SHA-1 was deprecated in 2011, because it is known to be insecure. Sometime in the last few years, Fedora completely disabled SHA-1 in its default system-wide crypto policy. It is literally impossible to SSH to one of these things (if one has any SSH keys set up) without reducing the system-wide crypto level.
I don't expect network equipment vendors to move fast, nor do I expect them to keep updating EOL equipment, but that is not what is happening here. This is a brand new managed switch, running its most recent firmware that was released in 2025. There is absolutely no excuse for this level of pure laziness.
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
Hi @ipilcher , after analysis, we have identified the cause and will fix it as soon as possible in the next software version. Thank you!
- Copy Link
- Report Inappropriate Content
To help assist and streamline the identification of the behavior, we recommend sending an email to forumsupport.usa@tp-link.com with the following information:
Subject: [Forum Escalation][ID]
Forum Nickname:
Thread URL:
Model&Version:
Description:
Any Other Relevant Information (Logs, Config Files, Images, etc.): [
Once sent, a ticket will be created in our support system, and a member of the team will follow up to gather more information or troubleshoot a cause.
- Copy Link
- Report Inappropriate Content
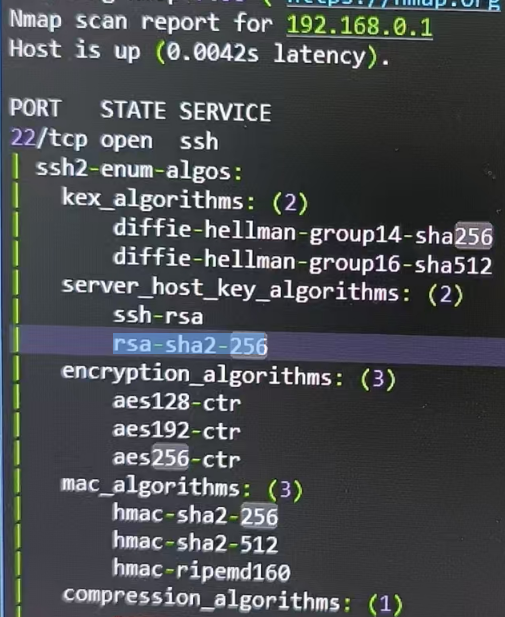
Hi @ipilcher , I checked, and it seem already support SHA2, and it supports RSA-SHA2-256 by default, which uses SHA2 as the key signature algorithm. Could you please share us where do you get the information about SHA1 at TL-SG2218 V1 / FW 1.20.9 ? And could you please help to upgrade to the lasted FW and check?

- Copy Link
- Report Inappropriate Content
You are correct that the switch supports SHA-2 signatures for host keys. That's not the issue here.
The algorithm in question is the signature algorithm used for user keys (when using key-based, rather than password-based) authentication.
For example, when I connect to the switch with ssh -vvv ..., the output includes the following:
debug1: kex: host key algorithm: rsa-sha2-256
This confirms that the switch does support SHA-256 (SHA-2) for host key signatures.
Later in the output, the following appears:
debug3: sign_and_send_pubkey: signing using ssh-rsa SHA256:EOg4nSUl05t08gAElH+wvzM1zDHHa0rI6KjL3mS5iDY
This can be a misleading, because of the fact that "SHA256" appears in the output. However, that refers to the algorithm used to create the key fingerprint, not the signature hash algorithm. The latter algorithm is identified by signing using ssh-rsa, which identifies the signature algorithm (RSA with SHA-1).
A connection to a different system, using SHA-256 as the signature algorithm, shows this:
debug3: sign_and_send_pubkey: signing using rsa-sha2-256 SHA256:EOg4nSUl05t08gAElH+wvzM1zDHHa0rI6KjL3mS5iDY
Hopefully this explains the issue.
- Copy Link
- Report Inappropriate Content
Hi @ipilcher , we will check.
- Copy Link
- Report Inappropriate Content
Hi @ipilcher , after analysis, we have identified the cause and will fix it as soon as possible in the next software version. Thank you!
- Copy Link
- Report Inappropriate Content
Information
Helpful: 2
Views: 527
Replies: 5
Voters 0
No one has voted for it yet.
