TL-SG108E VLAN Configuration problem
TL-SG108E VLAN Configuration problem
Hello!
While trying to set up 802.1Q VLAN in my system which has TL-SG108E and two TL-SG105E I ran into a problem where no matter what PVID I give to a port, if it's different from 1, there's NO connectivity.
I nailed it down to the simplest configuration with just a SINGLE TL-SG108E.
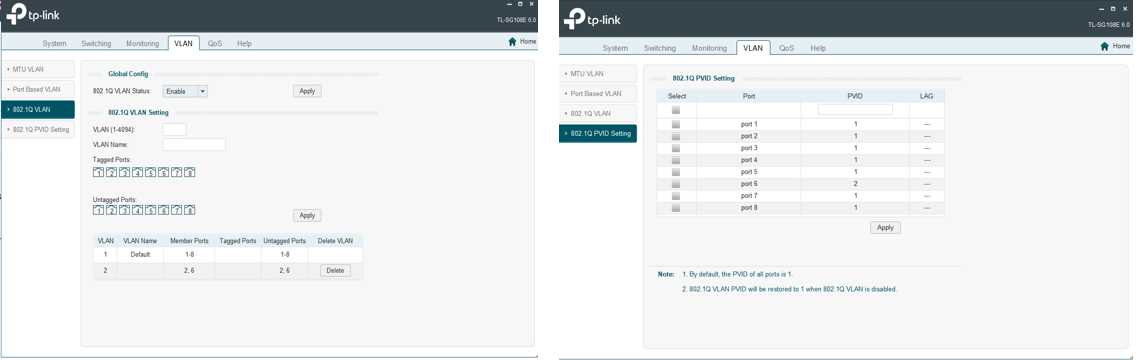
Configuration:
1. Single TL-SG108E, 192.168.1.230
2. PC connected to Port 6, 192.168.1.77
3. Router connected to Port 2, 192.168.1.1
 I can access TL-SG108E (192.168.1.230).
I can access TL-SG108E (192.168.1.230).
If I change PVID of port 6 to 1 - everything works. If it's 2 - no connectivity to any node beyond TL-SG108E.
If PVID of Port 6 = 2, arp of 192.168.1.1 and ping to 192.168.1.1 don't work.
What's wrong and how to fix this?
Thx,
D
1 Accepted Solution
