“tplinkwifi.net” be recognized as “insecure” after enabled the https access in the web-based UI?

Before explaining the reason why our browser acts like this, here is the background of this issue:
As we all know, when we are trying to access an https server, such as youtube.com, facebook.com, etc. The https server would offer us a Certificate, we have to identify this Certificate before we begin to communicate with the server.
How could our browser know the Certificate is true or fake?
Our browser needs a CA(Certificate Authority) to verify the server’s Certificate.
What is CA? What is the purpose of CA?
CAs’ purpose is to provide a Certificate for servers, servers’ Certificates are all coming from CAs.
Our browsers trust some authoritative CAs, these authoritative CAs’ Certificate is pre-stored in our operating system and browser. If a server could prove that its Certificate is issued by an authoritative CA, then our browser would trust the server’s Certificate.
You may understand how CA works after seeing them like this:
Alice trusts Bob, and Bob trust Chris, therefore, Alice could trust Chris. In this analogy, Bob is the CA.
Let's get back to the https issue.
Firstly, take a look at the Certificate of tplinkwifi.net
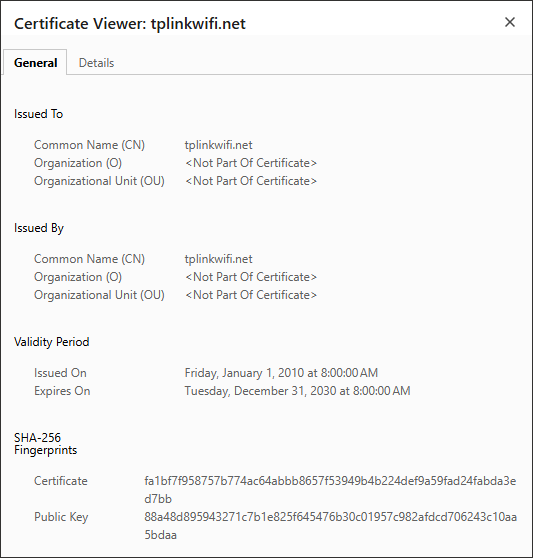
Issued by: tplinkwifi.net, Issued to: tplinkwifi.net
There is the reason why browsers recognize tplinkwifi.net as “insecure”, tplinkwifi.net's Certificate is issued by itself, and our browsers don't trust tplinkwifi.net's Certificate because it is not an authoritative CA.
However, even if our self-signed Certificate is not trusted, the connection between your browser and the tplinkwifi.net server is secure.
A Certificate's purpose is only to allow a client to verify an unknown server. It has nothing to do with the encrypted connection.
The data transmitted between the browser(client) and tplinkwifi.net(server) remains safe and encrypted. No one else could decrypt these data except the client and the server, because tplinkwifi.net uses TLS v1.2 as a secure connection builder.
TLS v1.2 is a widely recognized secure connection protocol.
Take Chrome as an example, in our browser, access tplinkwifi.net and press "F12" on the keyboard, switch to the "Security" tab.
you will see these following information:

From Chrome's security report, it is obvious that tplinkwifi.net is using TLS v1.2 and the connection is secure. We don’t have to worry about the safety of our computers and the router.
