TP-LINK TL-SG108E VLAN configuration issue
Model : TL-SL2210WEB
Hardware Version : V1
Firmware Version : 1.0.0 Build 20140210 Rel. 55137
ISP : www.telenet.be
I'm trying to configure 2 "easy smart" SG108E switches so that I have 2 VLAN's and 1 MTU uplink that pushes both VLAN's between both switches like this:
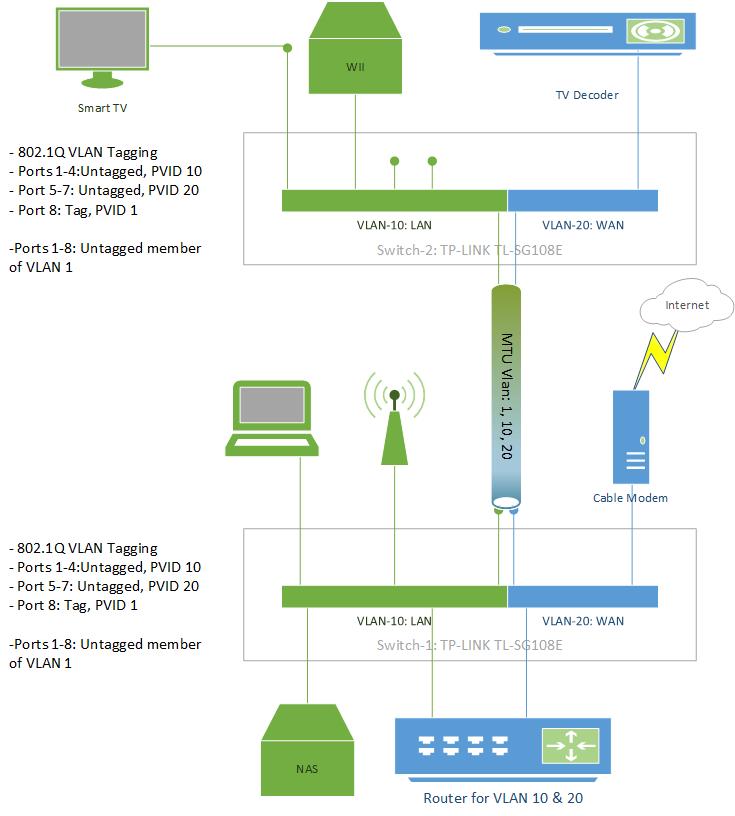
Based on some configuration tips (related to the "real" smart switches) I created the config below and used backup/restore to make sure both switches are set up identically (I did change their local IP address):
MTU VLAN enabled, Uplink Port 8
[*]Port Based VLAN disabled
[*]802.1Q VLAN Enabled: VLAN's 1, 10 and 20 created
[*]802.1Q PVID: Ports 1-4 in PVID 10, Ports 5-7 in PVID 20, Port 8 in PVID 1
[*]
The 802.1Q config has ports 1-8 untagged in VLAN 1, ports 1-4 untagged in VLAN 10, ports 5-7 untagged in VLAN 20 and port 8 Tagged in both VLAN 10 & 20.
To test the setup, I've connected a LAN port of my router to SW1 Port1:
SW1 Ports 2-4: no DHCP and so no internet (WHY ???)
[*]SW2 Ports 1-4: DHCP and internet !
[*]SW1 & SW2 Ports 5-7: no DHCP and no internet (as expected)
[*]
When I connect the LAN cable to SW2 Port 1 the above list reverses (SW1 works, SW2 port 2-4 don't)...
What am I missing ?
Can my setup be build without any security risk of direct communication between the VLAN 10 (LAN) and VLAN 20 (WAN) ?
My ISP requires that their set top box (TV Decoder in the drawing) is connected directly to the cable modem and not behind a router so I have to get the WAN network connected to the TV area and I only have a single CAT5 cable going up there and rather than adding something like powerlan I was hoping to solve my issue with 2 managed switches.
Thanks for any feedback,
Eric
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
1) I would disable MTU VLAN. I have never heard of a MTU VLAN and it does not appear in the Smart Switch line which I use. I had to download the manual for your switch to see what it does. It appears that the MTU VLAN setting is a way for you to build VLANs if you want all ports on their own VLAN. This is not what you need.
2) In your scenario you really only need 2 VLANs but best practice would have you do 3 so we will do 3.
VLAN1:
Include port 8 PVID 1
Port 8 should be Untagged
VLAN10:
Include ports 1-4 and 8
Ports 1-4 should be untagged PVID 10
Port 8 should be Tagged (Leave PVID 1)
Vlan20:
Include ports 5-7 and 8
Ports 5-7 should be untagged PVID 20
Port 8 should be Tagged (Leave PVID 1)
Now this will keep the traffic separate but ports 5-7 will be able to get to the internet by going directly to the modem. Personally I would make VLAN20 only include the port for the decoder (untagged) and port 8 (Tagged). I would put the other 2 ports (the two from the 5-7 that are not connected to the decoder) in VLAN10, but that is up to you.
- Copy Link
- Report Inappropriate Content
This was my first encounter with these "easy smart" switches and I had found a forum thread somewhere indicating that MTU should be used for this setup. The manual is a bit confusing:
" MTU VLAN (Multi-Tenant Unit VLAN) defines an uplink port which will build up several VLANs with each of the other ports." could be viewed as describing how to uplink two switches, even though " Each VLAN contains two ports, the uplink port and one of the other ports in the switch, so the uplink port can communicate with any other port but other ports cannot communicate with each other." does explain what I was seeing.
I guess that I would call MTU "Private VLAN's" which you could use to connect multiple pc's to a server (NAS?) while at the same time preventing them to communicate with each other. That might be useful in a classroom environment but it's not really relevant for my setup.
And yes I am indeed planning to use VLAN 20 only for ports that have a device connected to them and put everything else in VLAN10. But to do the original configuration of the switches it was easier to put enough ports in each VLAN to do some tests (and to just backup the Switch 1 config and restore it to Switch 2).
Thanks for a very fast response :)
- Copy Link
- Report Inappropriate Content
I have similar config, a shared "WAN" feed that provides internet and IPtv to my residence (equivalent to the cable modem in the diagram).
A bit differently, I have two TV decoders/set top boxes in two separate rooms that I need to feed as well as provide internet over the single Ethernet drop to each room.
I have a few questions:
1. Which port should the WAN/cable modem be connected to?
2. Which port does the connection between the two (or three) rooms (in my case) get connected to?
3. As the IPTV feed uses multicast traffic, should IGMP snooping be enabled on the switches... Or does the VLAN partitioning take care of that?
Thanks for your advice ... brad
- Copy Link
- Report Inappropriate Content
Hi, just wanted to add my own two cents for this. Maybe it will help somebody.
How to make a pfSense router from an old laptop and this switch.
I searched for long hours on the web and finaly have managed to build a pfsense Router from and old laptop and this switch with VLANs with some thinkering and many many fails and tries, basicaly I fuzzed with it until it worked like I wanted :-)
Things you need:
1. One older Laptop possibly with a gigabit lan port for speed. I used an old hp 2x2Ghz Core 2 Duo and 4GB RAM and 1Gbit nic (This will be the WAN and also the LAN management port for this setup separeted with VLAN)
2. TP-Link TL-SG108E Switch (this will be the physical WAN and LAN where the cables go)
3. Rufus USB burner program
4. pfSense ISO
5. Pendrive at least 1GB or bigger
6. 7zip or similar program if the ISO is zipped with .gz
TP-Link TL-SG108E SWITCH
------------------------------------------
Port 1. (WAN) - Internet (////IMPORTANT DONT INSERT THIS PORT JUST AFTER THE LAST STEP IS DONE////)
Port 2. (LAN)
Port 3. (LAN)
Port 4. (LAN)
Port 5. (LAN)
Port 6. (LAN)
Port 7. (LAN) - To PC where we make the settings (AFTER THE pfSense is set up ON the laptop)
Port 8. (to pfSense LAPTOP)
------------------------------------------
Laptop Setup
First you need to install the pfsense to the laptop. There are plenty of tutorials on the net, but basically you download the pfsense image and use Rufus to write it to a pendrive.
I think they also have a wariant which is an USB pendrive installer by it self but I dint try that one I choose the CD Image ISO-one (if the downloaded file is .gz you need t unzipp it use 7zip or similar program for it) and burn it to a pendrive with a program like Rufus
After that you boot the laptop from the pendrive and choose to install pfsense on the laptop (all data will be formated on the hdd or ssd so use one for this purpose only)
When installing just choose the defaults when asked except when the part comes (Do you want to set up VLANS?) Choose yes.
And use the only nic or the gigabit nic (em0 or similar name will be showed)
It will ask you for a VLAN number choose between 2-4096
If you choose like the number 20 it will create the VLAN20 with a name like "em0.20" I will choose 20 for this guide
It will ask for a name for your VLAN you can leave it blank or write one
It will ask for second VLAN dont choose another one.
After that it will ask you to choose a WAN adapter and list adapters like this (em0, em0.20) choose "em0.20" for WAN (em0.20 is the VLAN that we created earlier)
and choose "em0" for LAN
When finished you will have a status on the pfSense laptop screen like.
WAN (wan) -> em.20 ->
LAN (lan) -> em0 -> 192.168.1.1
Note if your home router is also on 192.168.1.1 you need to change that or the pfSense one to a different one so they dont get in a DHCP fight
If your main router dint use the 192.168.1.1 address you can skip this and go to set up the Switch part
You can change the pfSense one to 192.168.10.1 or 10.10.10.1 what ever you want with the (2, Set interfaces IP address option on pfSense)
If setting it up it will also ask for a subnte bit you can use 24 that is the default for a home network usually
It will ask also for IPV6 but you can leave it blank
When asking for DHCP enabled choose Yes
Enter the Sart address of the IPV4 client address range: you can leave it blank it will use the best option
Now we need to set up the SWITCH (this will be easy)
you can look up the switch IP with a port scanner like Advanced IP scanner or, you can have this info from pfSense webinterface usually on 192.168.1.1
and in the Status DHCP Leases. But I'm sure everybody will manage this one way or another.
Enter the menu of the switch and
choose menu "VLAN"
choose menu "802.1Q VLAN"
Enable it first at the top
Enter the VLAN ID number that you choosed on the laptop for the WAN VLAN I choosed 20
Set: VLAN ID 20 / VLAN Name you can leave it blank or add one
Set: Port 1 Untagged
Port 2
Port 3
Port 4
Port 5
Port 6
Port 7
Set: Port 8 Tagged
(So SET PORT 1 to Untagged with 20 and Port 8 Tagged with 20) (This will ensure that everything entering port 8 from the switch to the pfSense laptop will be tagged with 20, and everything leaving the switch from port 1 to the Internet will be untagged from VLAN 20)
push the Add/Modify button
!!!NOW IMPORTANT We need to set up that data from the Internet entering into the swich will be tagged with 20 (VLAN20)
We do that on the Menu item below "802.1Q VLAN" it is called "802.1Q PVID Setting"
Enter that
input the number that you choosed for the WAN VLAN on pfSense in my case 20 into PVID
And choose Port 1
And Apply
(basically what this does is everything entering the switch on Port 1 will be tagged with 20 so VLAN20 and the only port that can read VLAN20 is Port 8)
So the pfSense Router on Port8 will read the traffic with VLAN20 and relase it back after processing it (Qos Firewall rules, and all the good stuff from pfSense) back at port8 to the switch without the 20 tag so the information back from port 8 wont be taged with VLAN20 anymore. So it will be readeble to Port2, Port3, Port4, Port5, Port6, Port7 (Those will be our LAN ports) and also to Port1 (our WAN port) if something is sending data to the Internet
And the LANs wont see the internet from Port1 because it is tagged with VLAN20 when it is incoming and they can only see the internet after the pfSense router processed the traffic and relesed back at Port8 to the switch without the 20 tags so it can be outgoing also.
You can test this from a laptop that is conected to one of the lan prots from win10 use "CMD" and in CMD "tracert" like the command "tracert google.com"
This will show you the steps to the internet like.
192.168.1.1 (pfSense Router)
192.168.0.1 (or similar that will be your home router)
145.236.238.246 (or anything in the internet)
and so on and so on
But it Shows that the Laptop is going out to the internet behind the pfSense router
And We are Done.
Easy
ps: one downside of this setup will be that the one gigabit port on the laptop needs to process the incoming and outgoing VLNA20 data so 1000Mbit will be approx 500Mbit Up/Down but if you dont have a Gigabit Internet connection this wont be a problem. And you have a full fledged pfSense Firewall on the budget from an old laptop and from this nice little Tp-Link Router.
Enjoy
And have a Great day
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 15865
Replies: 4
Voters 0
No one has voted for it yet.
