SMB Share across VLANS
Hello,
I am trying to enable SMB share across VLANS.
Inter VLAN communication is blocked with Switch ACL rules Network to Network deny on all VLANS except itself, for each VLAN.
I want to enable a specific device smb share (desktop) to my android tv kodi.
Would something like this work:
IP Port Group for desktop
Subnet 192.168.50.10/32
port 137-139
port 445
IP Port Group for Tv
Subnet 192.168.30.10/32
port 137-139
port 445
Two allow rules on top of the deny rules, one for each device to the mac address of the other device:
IP Port Group for desktop > Mac Group (Tv)
IP Port Group for TV > Mac Group (Desktop)
Tried before with IP Group, tcp and udp protocols and failed:
IP Group (desktop), udp, tcp > IP group (tv)
IP port group (tv, port 137-139, 445 - as above) to Ip group TV and couldn't even ping the devices across lan.
Can anyone post an example that is working with only specific devices? I do not want to unblock the network to network rules, I want the blocking rules in place, but only allow specific ports to specific devices, in this instance for inter VLAN SMB share. Would ping work if SMB share ports are unblocked, or do I need to ping the specific device and specific port via telnet command?
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
Anything short of permit all ip group(subnet/32) source to ip group (subnet/32) destination will not work.\
If I use mac group instead of ip group, I will get destination host unreachable from the device subnet's gateway. ping 192.168.30.5 will respond with 192.168.10.1.
If I let the two permit ip group rules on the top and will not touch anything else, I will get something like below, completely random.

Until now, nothing is intuitive and ACL rules are outright broken when trying to set rules for inter vlan communication. I don't like that I have to give the device access to my desktop and not being able to at least restrict ports.
Did someone at least tried to enable inter vlan rules from a device, to device and specific port basis? I would have liked only SMB Share port to be open in this case.
- Copy Link
- Report Inappropriate Content
ACL on switch is not easy. but you have to create a IP PortGroup like this. and add rule opposite off what logic.
I have hour and hour with trying, but only way is to give access is via ip portgroup as i see.
Hope there wil come an option for access control on router. they have this on standalone now so I expect that on SDN soon.
And ping will not work unless you create a ip group and assign ipgroup to acl witch ICMP protocol only. remember all allow rule must be over deny rule in the rule list.

ICMP roule somthing like this.

- Copy Link
- Report Inappropriate Content
I had the exact rule as IP Port Group and made one rule for each device.
IP port group (desktop) to TV (ipgroup)
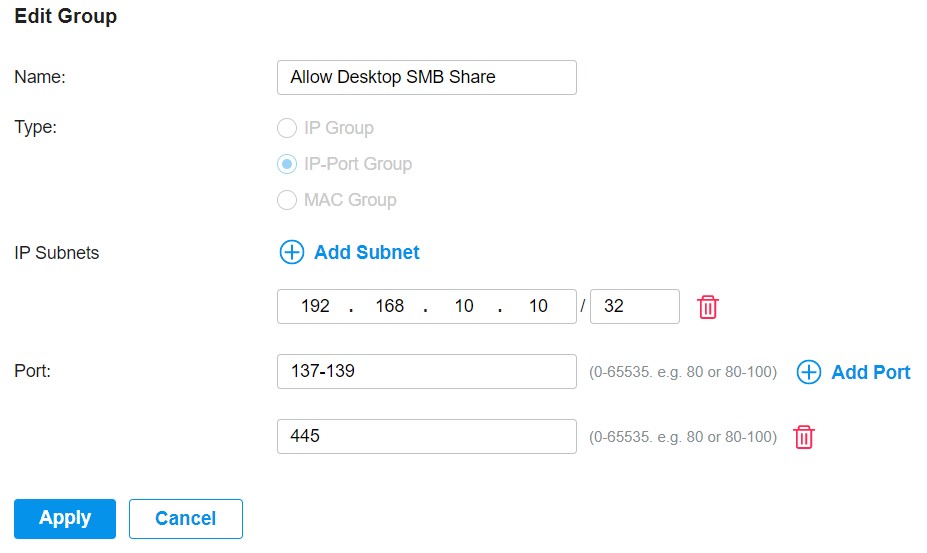
IP port group (tv) to desktop (ipgroup)

ACL:
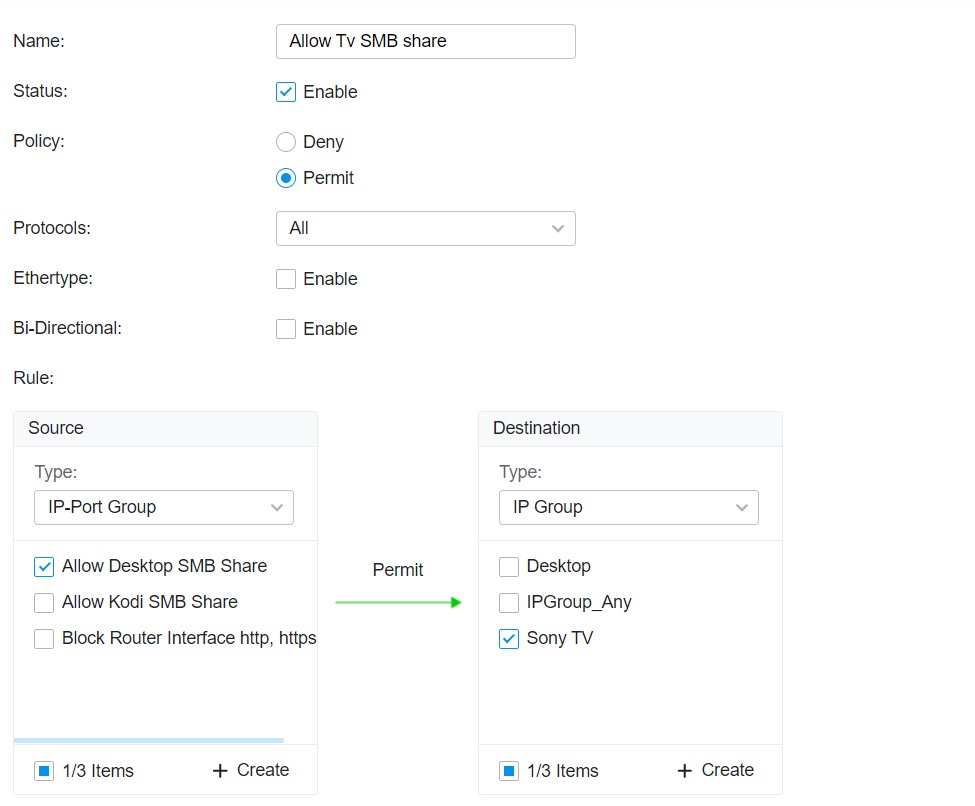
I will try one more time with this setup:
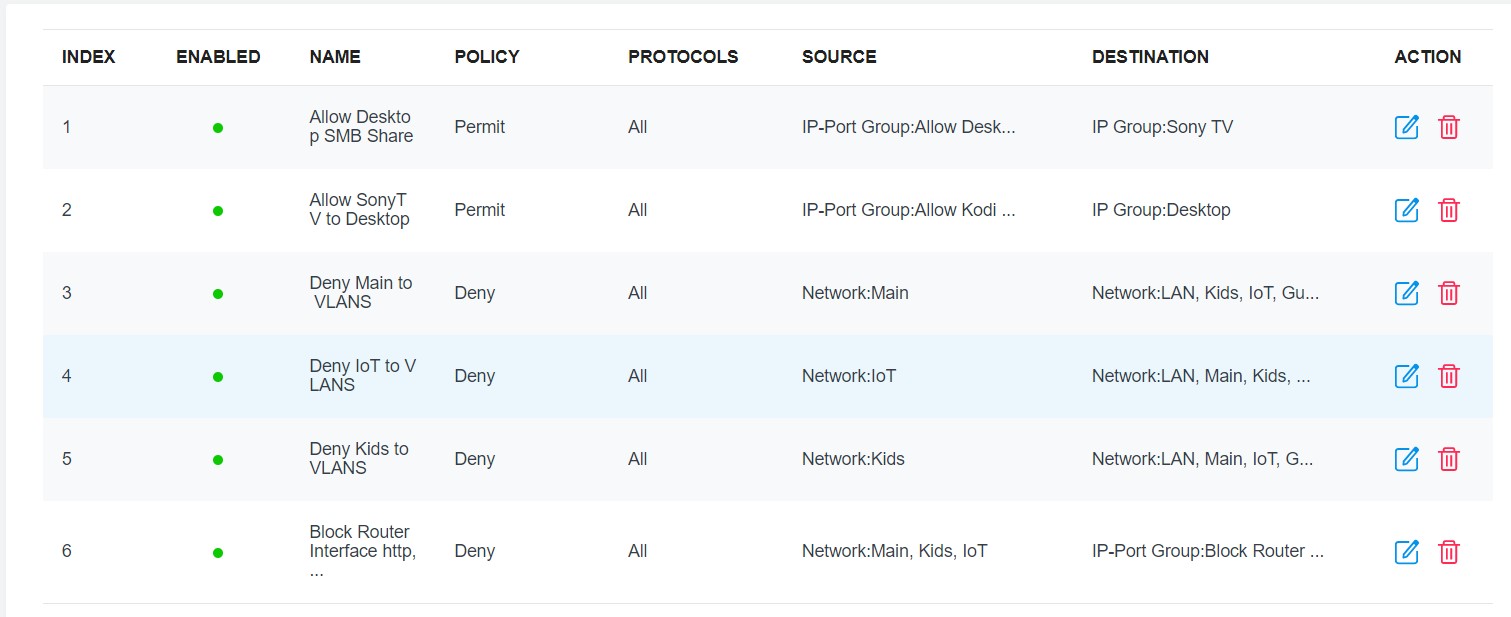
I would have only let TCP and UDP protocols but I am really tired, because it should have supposed to be pretty simple, since I knew the ports required for the protocols and I have fixed Ip for each device.
I could try to let a permit all both ways ip group to ip group on all ports and protocols but that is not something I would want for a tv that hasn't received a firmware update since 2017.
- Copy Link
- Report Inappropriate Content
Maybe you should try to add gateway in SONY TV group to, Gateway is probably blocked by ACL
- Copy Link
- Report Inappropriate Content
@shberge How do I add the gateway to the ip port group?
Something like this? I think you are on to something since both the desktop and the tv are connected to different switches so they communicate trough the router. Since there are two switches involved should I add the gateway to the Ip port group of desktop, too?
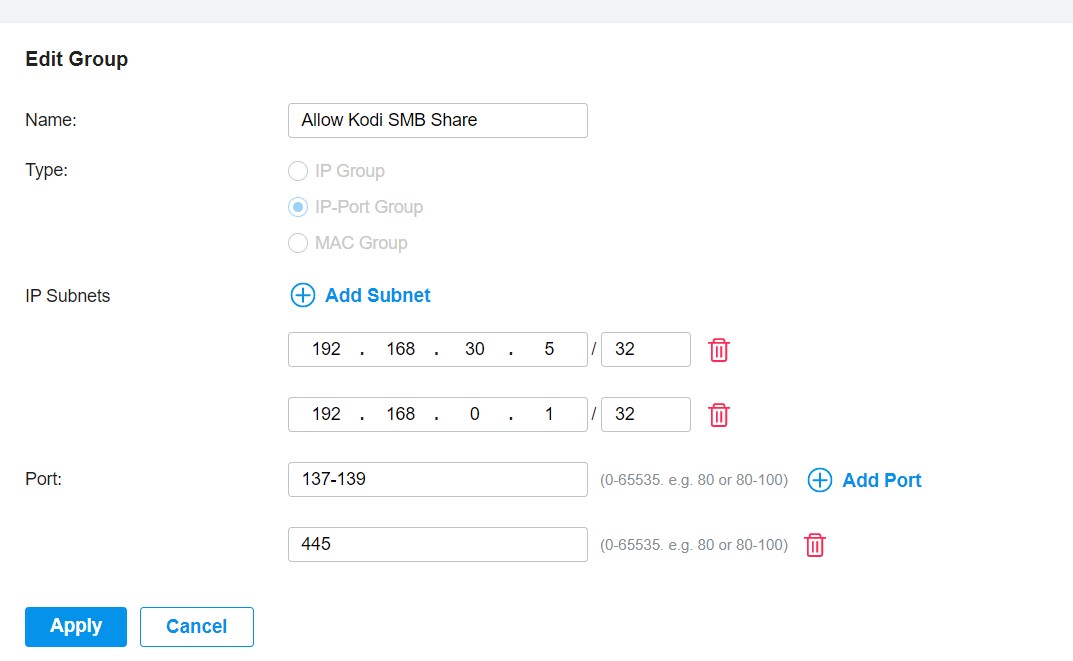
Is this correct?
Image with the topology:

Gateway ACL Rules of Gateway ACL take effect only on the traffic which is sourced from LAN ports and forwarded to the WAN ports. I thought about adding the permit rules to the gateway acl, but from description the rules Gateway ACL I really shouldn't, since the traffic that I need does not go to the internet, is only local.
- Copy Link
- Report Inappropriate Content
You ned to add gateway that belong to the device network, e.g 192.168.30.1 for device 192.168.30.5 and so on
there is no point to add gateway in ip port group only in ip group i think.. but this is complicated and not easy to instruct without having the whole picture.
Maybe @Fae have more information about how to do this. there is not much documentation to find on this. I hope we don't need ACL on switch in the future, much easier to do this on firewall, switch acl is great if you want to acl som device on same lan but not on vlan and remote lan.
- Copy Link
- Report Inappropriate Content
"You ned to add gateway that belong to the device network, e.g 192.168.30.1 for device 192.168.30.5 and so on"
Is this the correct way?
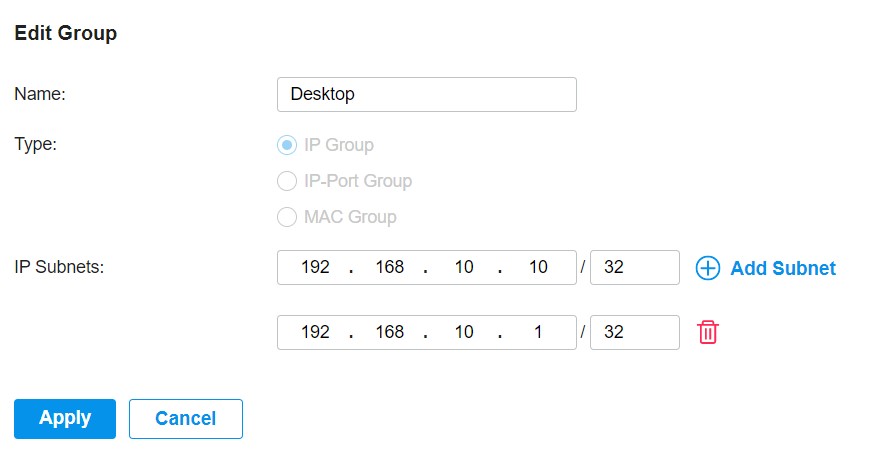
Forgive me if I am idiotical about this, but the Omada is not a very documented business product and most of the documentation is already out of date. ex: I wanted to make a manual back-up of the controller, looked up the sdn manual posted for 4.3.5 version and the pictures from the manual were very different what I had available on the controller page in maintenance and there was no manual backup button.
You are the only user that has consistently replied to my queries, the super users from TP-Link do not bother with these little questions and I am very gratefull for your feedback. Hope they give you money for your help, because my local country support cannot handle the inquiries (I couldn't modify the default pvid for the router ports, so I basically bought another switch to make vlan happen for the rest of my network).
- Copy Link
- Report Inappropriate Content
@userNAC Yes with this port group you also give access to gateway that is needed to communicate from vlan to vlan since all traffics go thru the router.
now you have to apply the rule in top of rule list, with apposite of what you think :-)
If you need access to 192.168.50.10 from LAN try to add this rule, start with something easy and choice LAN as destination and when this work try to change to what you want.
I don't know what IP you have as LAN or VLAN, this is just an example.

- Copy Link
- Report Inappropriate Content
@shberge In this case, your IP Port Group 192.168.50.10/32 has two subnets: 192.168.50.10/32 and 192.168.50.1/32?
LE: absolutely gave up on this. Inter VLAN communication is totally broken. Tried all the permit rules in the setup below, with ip port that includes the gateway and combinations of them. IP group and Mac Group are not working as intended and IP port Group to network permission does not work either.
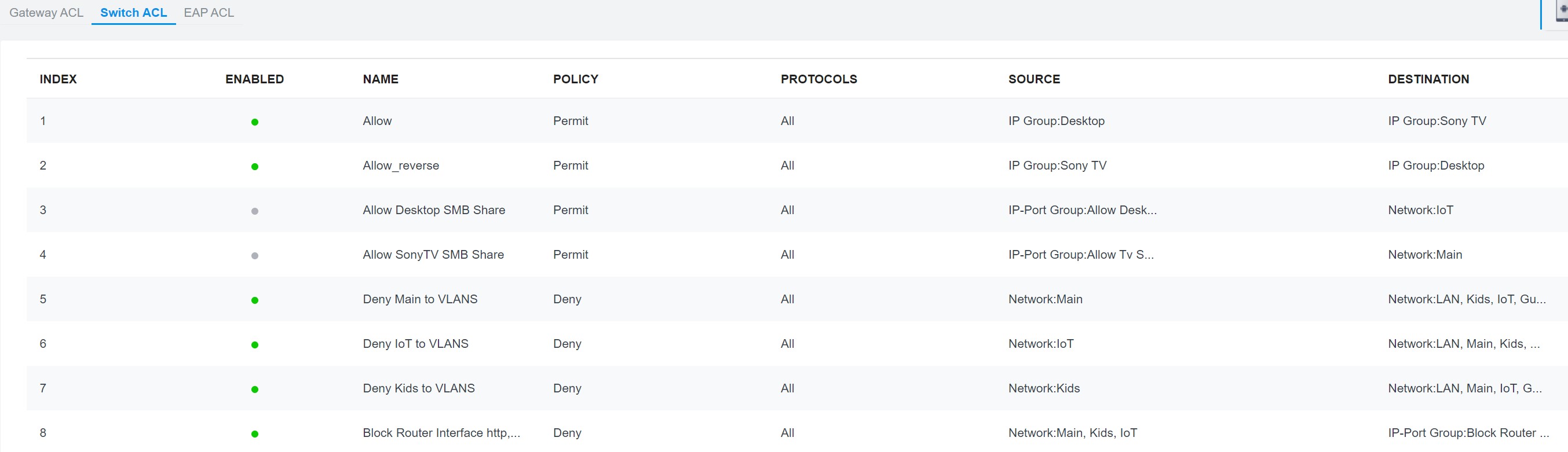
Tp Link please solve your problems, because inter vlan communications is not a possibility if you isolate VLAN by ACL. It wont simply work and your admins refuse to give working examples in both SDN 4.3.5 manual and in the forum. Is that like you wont care, although you want to be a competition to Ubiquity.
I am sorry to say, but I think I made the wrong choice I am very angry with your lack of support.
- Copy Link
- Report Inappropriate Content
Yes I agree with you, we can probably say that there are no firewall options but acl on switch is a temporary work around to block intervlan.
I work with unifi and cisco daily and I must say that I am not very impressed with USG for unifi either, so I prefer to use cisco firewalls, they are so much better and they can stand and run for several years without a single reboot. I have some Ciscos that I forgot I had that have been going on for 4-5 years without restart .. I have 70-80 Cisco ASA and it happend i forgot some.. but they work so good thet its easy to forget some ![]()
But I am also interested in the Omada SDN platform, currently this is a hobby but when stability and function come up to a level that I am happy with, I will use this as a unifi replacement. I hope this happend pretty fast,
If I have to guess, the firewall function comes to tp-link's router in the ver5.0 software but it's just guessing on my part.
We will see if tp-link comes with a documentation on ACL on swithes then :-)
Good luck with your ACL. it seems you just have to try and fail and it will work out in the end ..
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 5465
Replies: 10
Voters 0
No one has voted for it yet.
