Gateway ACL, LAN->LAN, IP-Port Needed.
Gateway ACL, LAN->LAN, IP-Port Needed.
At the moment, Gateway ACL rules don’t support defining groups based on IP and port combinations or similar criteria.
I believe this is important for enabling communication between isolated VLANs, especially for scenarios like accessing an internal DNS server.
At the moment, it seems only full networks can be defined, which limits flexibility.
Could someone advise on how to allow devices in an isolated IoT VLAN to reach a DNS server located in the main VLAN? Is there an alternative approach to achieve this?
By “isolated,” I mean there’s a gateway ACL blocking traffic from the IoT VLAN to any other VLAN, which currently prevents access to the DNS server in the main network.
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
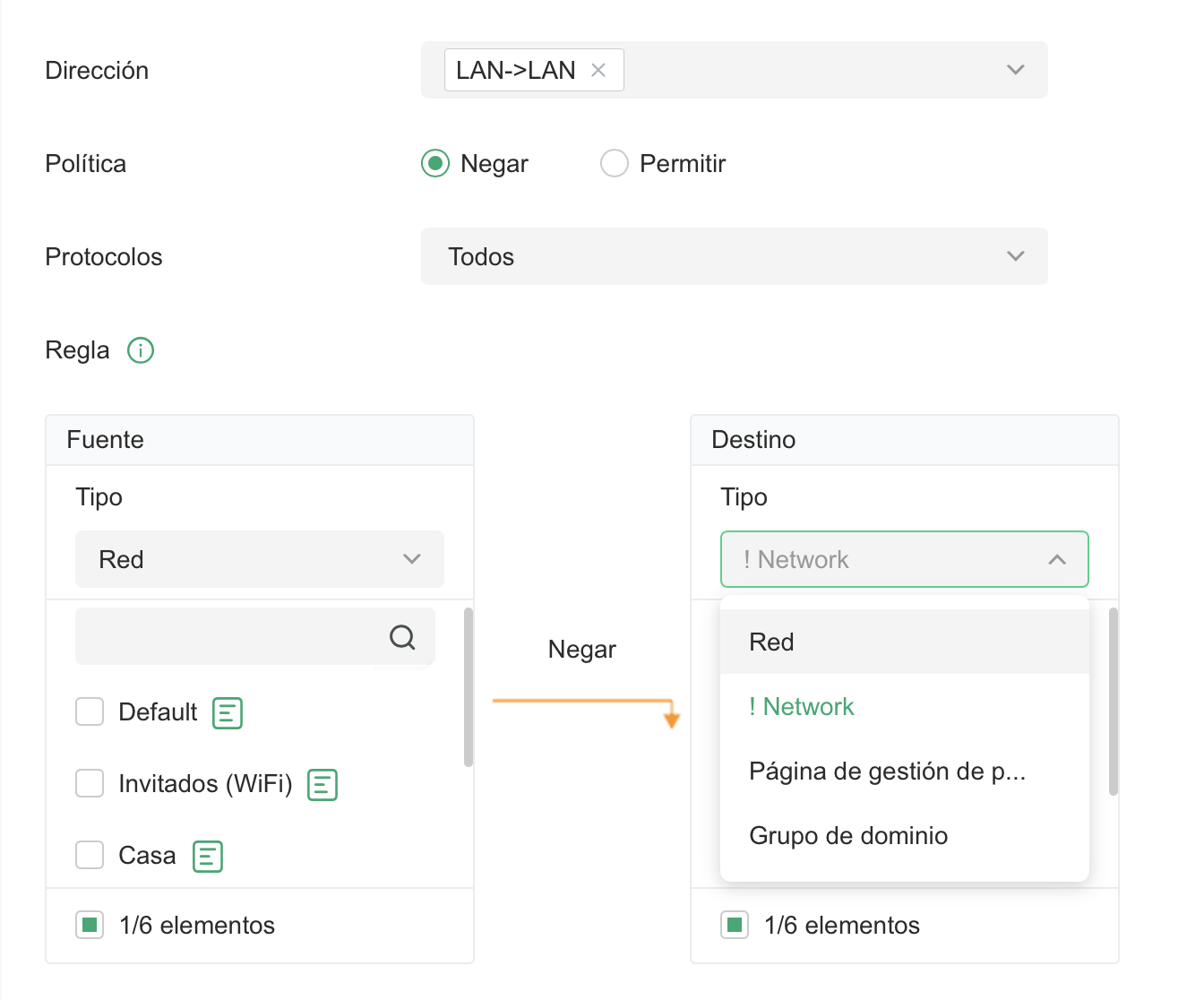
How would I do that? Because in the Omada controller I don’t see that option — I only get the options shown in this screenshot. Thanks!
- Copy Link
- Report Inappropriate Content
I don't have an answer for your question. I am new to this as I just replaced my Synology router with the Omada ER706W. When trying to set up ACLs to match my firewall rules in the old router, I discovered what you found out.
There is a new post here on the subject but I haven't investigated it yet. Let's hope this issue gets fixed soon in a firmware update.
- Copy Link
- Report Inappropriate Content
@jra11500 I just tried the tutorial of the post but not work.
VLAN 1 can reach VLAN 20
VLAN 20 cant reach VLAN 1
This is OK.
But vlan20 cant reach a specific IP (or ip group) of VLAN 1 that I allowed...
Thanks.
- Copy Link
- Report Inappropriate Content
I have a similar situation in which I have two isolated VLANs in the Network settings, more specifically one named "IoT" and the other "Cameras". My problem is not with DNS but with an Emby server that resides on my NAS. The NAS has two LAN interfaces, one on my primary network for the PCs, iPhones, etc., and the other on the Cameras VLAN. There are 5 smart TVs here on the IoT VLAN that need to access the Emby server.
I found a solution that is working and should work for your DNS as well. First, I needed to create a new Service Type under Preferences. As DNS is already predefined, you should not have to do this step. In my case, I named the new service type as EMBY with the source ports 0-65535 and the destination port 8096. I then created a new entry in the ACL list with the service type EMBY instead of ALL. The LAN -> LAN source network is set to IoT and the destination network is set to Cameras. It works! In the TVs, I specify the server address that is on the Cameras network along with the port 8096. As the port is unique, there is no problem. I do not use a local DNS server so I am unable to test this with DNS. It should work however if you speciify the service type as DNS instead of ALL.
- Copy Link
- Report Inappropriate Content
@jra11500 Hi, thanks for the help.
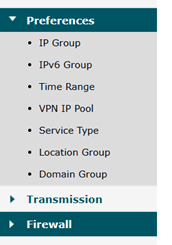
I've checked and don't see anything about "Service Type" under Preferences.
Also, what type of ACL are you creating in the ACLs?
Thank you very much.
- Copy Link
- Report Inappropriate Content
Here's what I have in the router's menu for Preferences:
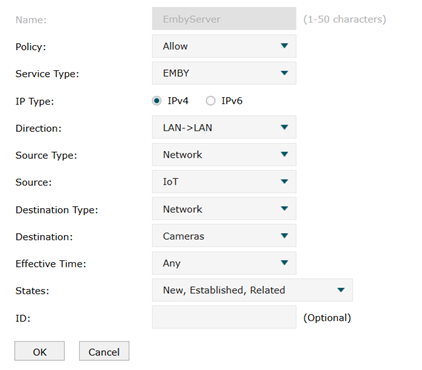
Here's my ACL rule in the router:
I do not have a controller and the router is in standalone mode.
- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
Two days ago my new controller arrived and I am migrating everything that operated in standalone mode. You are right! There is no Preferences section in the controller menus and no Service Type settings. This forced me to find another solution for my Emby server which resides on a different VLAN from the TVs. After reading the ACL post mentioned earlier, I finally managed to get things configured. Here is what I did:
1. I created a gateway ACL rule that allows the IoT network to access my Cams network (where Emby resides).
2. I created an IP-Port group for the Emby server with its IP address xx.xx.xx.xx/32 and its port number
3. I created two switch ACL rules (one for each direction) that allow the IoT network to access the IP-Port group. I did not use the "trick" used in the ACL post where the IP-Port group is both the source and destination. My rules are:
IoT network --> IP-Port group
IP-Port group --> IoT network
For me, it is easier to understand things this way
4. Finally, I created a switch ACL rule that denys the IoT network any access to the Cams network as the networks are to be isolated for everything else.
You should be able to configure your DNS server in the same way that I configured my Emby server and everything should work.
- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
Information
Helpful: 7
Views: 1119
Replies: 11
