Configuration Guide How to Shut Down the Switch Port Connected to an EAP to Prevent Intrusion via 802.1X Authentication?
Background:
This post provides a configuration guide on how to configure 802.1X to allow only specific EAPs to get a network, thus blocking any other device from getting a connection from the same network cable/port. At the same time, the wireless network is not affected.
This Article applies to:
Smart, L3/L2+ Managed Switches.
Easy Managed switches are excluded.
Application Scenario:
With the EAP connected to the outdoors, someone may unplug the EAP's cable and connect it to their own device, thus hacking into your internal or even abusing your network bandwidth. Or other similar scenarios.
Configuration Steps:
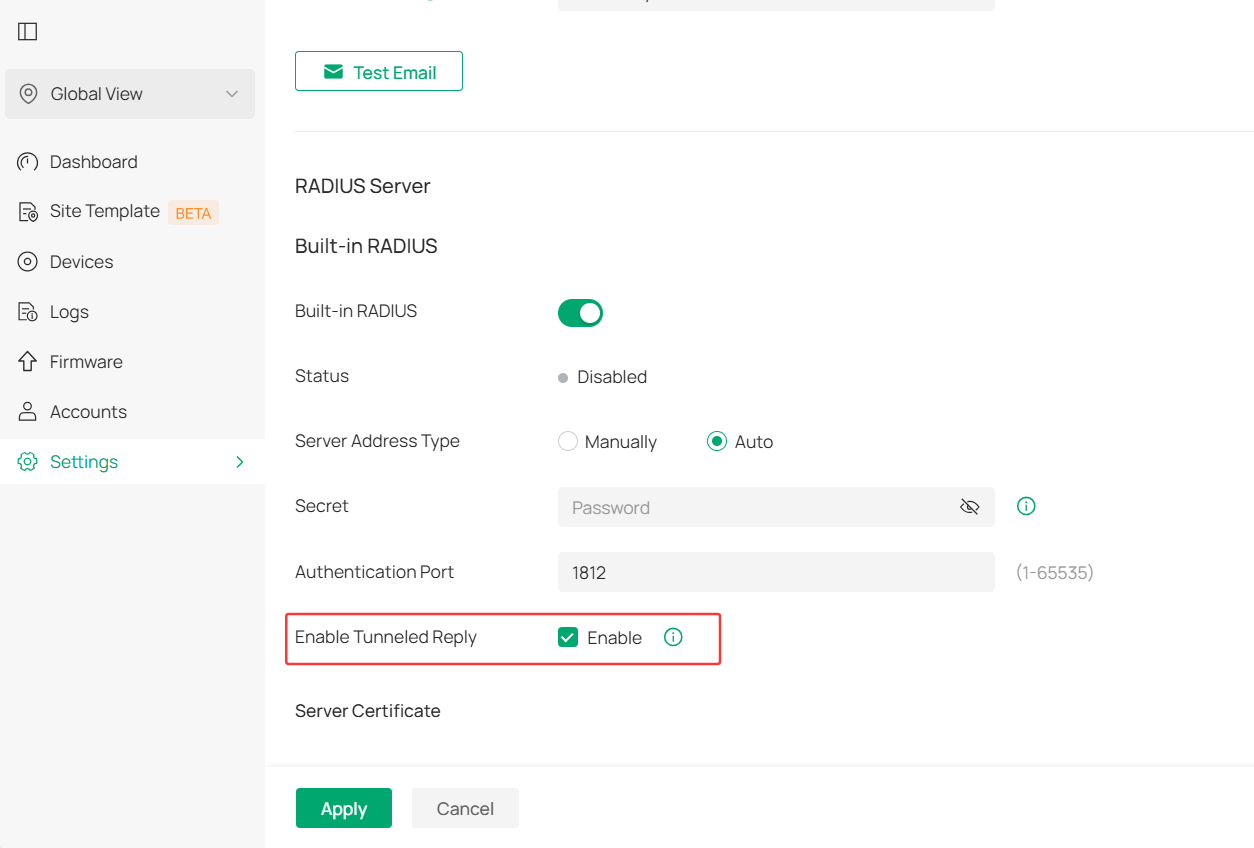
Step 1. Enable and Configure Built-in RADIUS
1. Launch Omada SDN controller, go to Global View > Settings > Server Settings, enable Built-in RADIUS, and click Apply.

2. Go to Site View, choose Settings > Network Profile > RADIUS Profile, click Edit

3. Click Add New RADIUS User:

4. Choose the Authentication Type as MAC Authentication, input EAP's MAC address, and click Apply.

Step 2. Configure 802.1X Authentication
1. Choose Site View, Go to Settings > Authentication > 802.1X, enable 802.1X

2. Choose the RADIUS Profile as Built-in Radius Profile, Authentication authentication protocol as EAP, the type as Port Based, and enable MAB. Choose the correct MAC address Format you input in Step 1, and double click the port which EAP is connecting. Click Save. See as below:

Note:
Please make sure you have double click the port, and the correct status is as above picture (there is a square frame enclosing this port).
If only click the port once, it will be like the below, which is wrong:

Verification:
Clients can connect to the EAP's SSID via its password, and access to the Internet:

Unplug the EAP with MAC address above from port 4 of the switch, and plug a PC in, the PC has no Internet access.

Recommended Threads:
Omada (Pro) Switch Naming Format
Feedback:
- If this was helpful, welcome to give us Kudos by clicking the upward triangle below.
- If there is anything unclear in this solution post, please feel free to comment below.
Thank you in advance for your valuable feedback!
------------------------------------------------------------------------------------------------
Have other off-topic issues to report?
Welcome to > Start a New Thread < and elaborate on the issue for assistance.


 ?
?