SAML Users/Roles
I have recently installed the BETA copy of the software controller and I am mostly happy with it so far. We previously had numerous OC200 controllers - one per site.
Under "Accounts" I see there is provision for SAML User and SAML Role.
Am I correct to think that by using these functions I should be able to configure login to the controller to be needing an approved Microsoft EntraID account ?
Would there be any documentation/guidance available for how to configure on the Omada Controller and within Entra ?
Thanks,
Andy
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
Hi @ekrizon
I agree.
I would recommend you starting a new thread under Request & suggestion block.
If there are others with similar requirements, we aim to gather detailed descriptions of these needs to ensure that the relevant departments fully understand and can conduct thorough assessments for functional support.
- Copy Link
- Report Inappropriate Content
Hi @ekrizon ,
Wondering how you configure the SSL part of it and redirected to the custom URL "https://omada.mycompany.com"
I have done this similarly via cloudflare however as you mentioned redirecting to the IP is what I am having issues with. How did you fix that and where on the host controller setting?
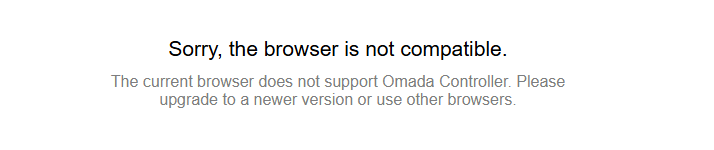
Additionally even though I did get through to the IP I end up getting this screen
"Sorry, the browser is not compatible.
The current browser does not support Omada Controller. Please upgrade to a newer version or use other browsers." Just wondering if this was the case for you?
I am using a hardware controller OC400
- Copy Link
- Report Inappropriate Content
Outside of the SAML settings, under System Settings do you have your box configured as IP or hostname? Thats where I had to change it to using our hostname. Then the SAML attributes (that get automatically populated) were instantly updated to using our proper hostname. As for your screenshot that I believe is what is shown if you visit the saml sign-in URL directly which should not be the case if everything is properly configured.
- Copy Link
- Report Inappropriate Content
I got SSO with SAML working but then it suddenly stopped working with this error:
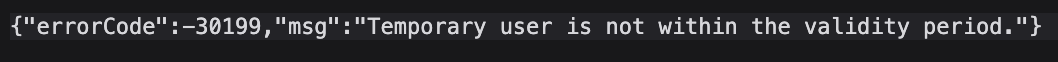
I configured an permament user and no temporary.
- Copy Link
- Report Inappropriate Content
@relvy Same here using authentik as the idP.
I do notice that if I set the URL to https://<ip>:8043/sso/saml/login/ (with the trailing '/'), I get the 'Unsupported browser for omada controller' window and if I remove the trailing slash, I get the {"errorCode":-30199,"msg":"Temporary user is not within the validity period."} error instead.
I have my SAML Role set to the same as the group name in authentik and it is set to Super Admin (permanent), so the temporary user message doesnt make sense. I tried adding a few more SAML roles that didnt have any hyphens or capitalization, with the same result.
- Copy Link
- Report Inappropriate Content
@baudneo I found the root problem in the authentik intregration guide.
If the user is a member of multiple groups then the python code for usergroup_name does not (necessarily) return the group name configured in the omada controller.
When the wrong group is used for login then the "Temporary user is not within validity period" error occurs.
Solutions that work for me:
1. Make sure the user is a member of the only one group configured in the omada controller.
2. For userGroupName always use the one group configured in the omada controller, e.g. python code: return 'omada-admins'
- Copy Link
- Report Inappropriate Content
@relvy Awesome, thank you. I had seen somewhere along the way that it did say that only 1 user group was supported. I wasnt sure what they were meaning by that though. I wonder if there is a way to instead use a user/group attribute to send the desired omada group name?
Edit: The authentik docs 'username_group' property mapping python code can be modified to only send the group name if its the omada provider and some other checks. You'll want to uncomment the logging line and try and login using SAML to trigger the log line (in the 'docker compose logs -f' output). My omada provider is named: ''Provider for Omada" so I filter using "Omada".
The default logic will still trigger if this isnt the omada provider, its not my username or the 'omada-saml' user attribute isnt set on my username.
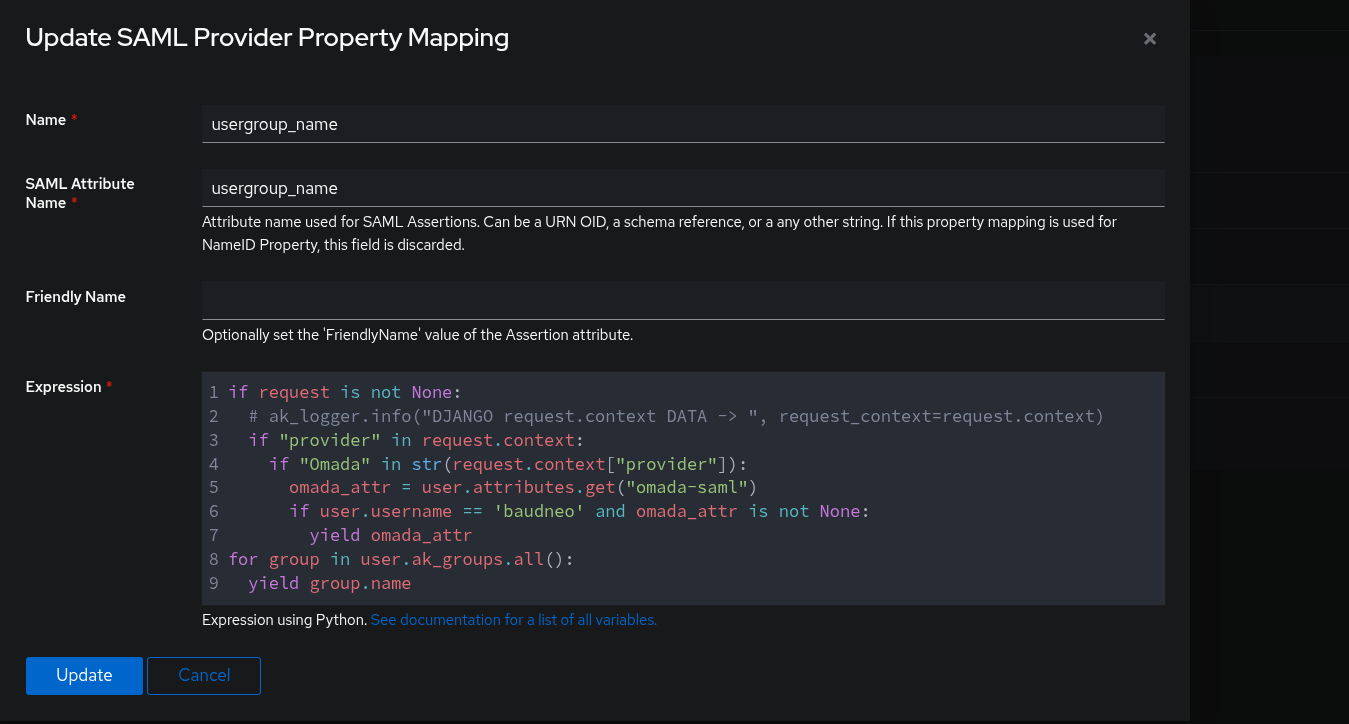
- Copy Link
- Report Inappropriate Content
Another solution that came up to me is using OAuth2 because it works regardless of the group membership.
However, this requires the Omada Controller to (also) support OAuth2 which is not the case as of this writing.
Edit: I filed a feature request for OAuth2/OIDC. See https://community.tp-link.com/en/business/forum/topic/841554
- Copy Link
- Report Inappropriate Content
@baudneo Thank you.
> I had seen somewhere along the way that it did say that only 1 user group was supported. I wasnt sure what they were meaning by that though. I wonder if there is a way to instead use a user/group attribute to send the desired omada group name?
There is a 1:1 relation of authentik roles to authentik groups. This limitation comes from the postgresql django extension.
Here is a group based solution that requires the 'omada-saml' attribute for the right group.
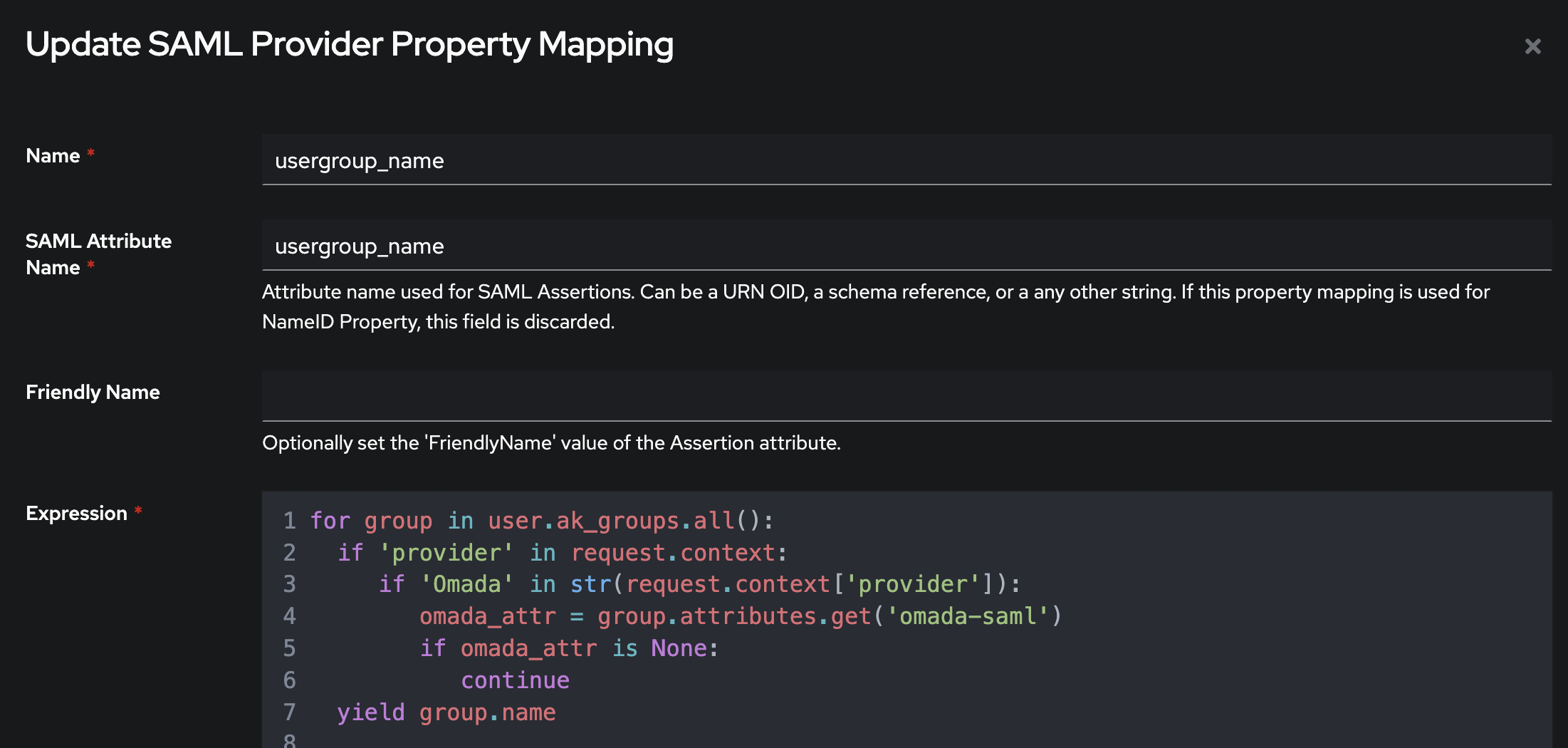
- Copy Link
- Report Inappropriate Content
@baudneo Authentik updated their integration guide. The update addresses the issue with multiple groups.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 2834
Replies: 22
Voters 0
No one has voted for it yet.
