Block All Incoming Except my Website Access
Block All Incoming Except my Website Access
Hi
I want to disable and block all incoming traffic to my network and NAS behind my firewall. But I have a web server running on NAS so I onyl want that to be accessible via my external IP.
Is there any way to achieve this?
If I create a BlockAll rule in access control and create a port forwarding rule to NAS then the BlockAll takes precedence. If I also create a Allow HTTP firewall rule still the Block rule takes precedence and does not allow HTTP access to NAs.
What to do?
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
Hi @Colonic
Thanks for posting in our business forum.
Colonic wrote
Hi
I want to disable and block all incoming traffic to my network and NAS behind my firewall. But I have a web server running on NAS so I onyl want that to be accessible via my external IP.
You sure all incoming?
Or simply the NAS?
https://community.tp-link.com/en/business/forum/topic/696340
In standalone mode, you have the option to use the IP-port ACL. In controller mode, you don't have it. You gotta use the switch ACL to support that.
- Copy Link
- Report Inappropriate Content
@Clive_A thanks for your reply. My firewall is at my home network and so a standalone. Wired internet is connected from firewall to the deco mesh and deco acts as access point for wifi at home. My NAS is connected to the VLAN port of firewall via ethernet.
what I need is block all incoming traffic to my home network (on all VLANs) but only exception is my website hosted on my NAS so people should still be able to access my website from WAN while every other type of incoming from WAN to my LAN should be blocked.
Is it possible using th Firewall Access Control and a combination of port forwarding or however else is it possible? For security I want to keep all incoming blocked but allow website traffic only.
- Copy Link
- Report Inappropriate Content
the firewall blocks everything from the internet and into your LAN default, if you want to have access to something from WAN to LAN you have to port forward. The exception is if you have removed NAT on the router but then you don't need to port forward either.
- Copy Link
- Report Inappropriate Content
controller mode does support IP-group and IP-Port Group on gateway ACLs in both WAN IN and LAN>WAN directions, which i think is applicable here
- Copy Link
- Report Inappropriate Content
Hi @GRL
GRL wrote
controller mode does support IP-group and IP-Port Group on gateway ACLs in both WAN IN and LAN>WAN directions, which i think is applicable here
Thanks for the notice. That's true.
Not sure when that was added. Not sure if it is the controller update that included that or the router. As I recall, this batch of firmware did not mention any of this feature.
Yeah, it's there now.
- Copy Link
- Report Inappropriate Content
@Clive_A IP group based routing is no good as IP addresses are never fixed from internet and I want my website to be accessible from anyone
- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
You can still achieve this with IP group ACLs
rule 1:
allow > wan in > ip_any > internal_ip_address
rule 2
deny > wan in > ip_any > ip_any
This will block everything getting to your lan except the specified internal_ip_address
BUT- what I dont know, and Clive may be able to answer, is if these are applied before any port forwarding rules or not. I do not know if port forwarding will just overide any gateway rules. I dont think they do, but not 100% sure.
- Copy Link
- Report Inappropriate Content
Hi @GRL
Thanks for posting in our business forum.
GRL wrote
You can still achieve this with IP group ACLs
rule 1:
allow > wan in > ip_any > internal_ip_address
rule 2
deny > wan in > ip_any > ip_any
This will block everything getting to your lan except the specified internal_ip_address
BUT- what I dont know, and Clive may be able to answer, is if these are applied before any port forwarding rules or not. I do not know if port forwarding will just overide any gateway rules. I dont think they do, but not 100% sure.
I recall that WAN IN is separate from the LAN.
To me, the first rule is not necessary. Port forwarding exposes the local service. And it is by default accessible to anyone.
Simply creating the second rule would not make a difference for the LAN. They should be accessible inside the LAN.
(I did not try this but based on my past experience, they don't interfere. When I port forward and test the block rule.)
- Copy Link
- Report Inappropriate Content
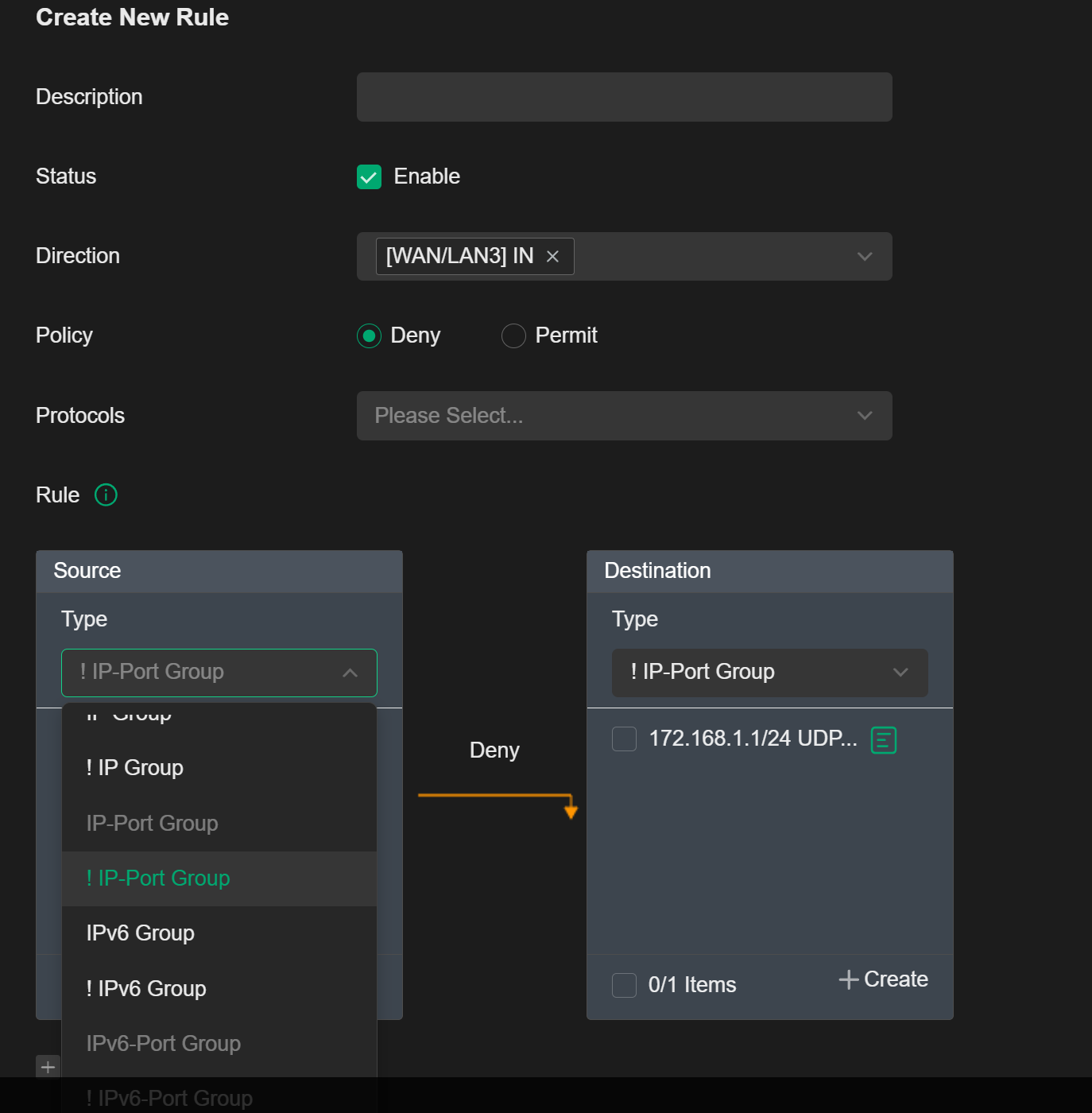
I just tested this
Opened up NAT port forwarding TCP 80 + 443 to controller
With a wan-in deny ip_any > ip_any rule, was still able to access controller from WAN.
Looks like the port forward does take precedence and is processed before this gateway rule
Interestingly, however
with a wan-in deny ip_any > ip_port_group (controller IP, ports 80,443) rule, could not access controller from WAN
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 760
Replies: 13
Voters 0
No one has voted for it yet.
