RDP ACL
Hi, I have a case related to ACLs.
In my organization, I have configured multiple VLANs with different network addresses. For now, I’m focusing on two of them:
-
Default VLAN:
192.168.10.0/24 -
LocalLabComputer VLAN:
192.168.23.0/24
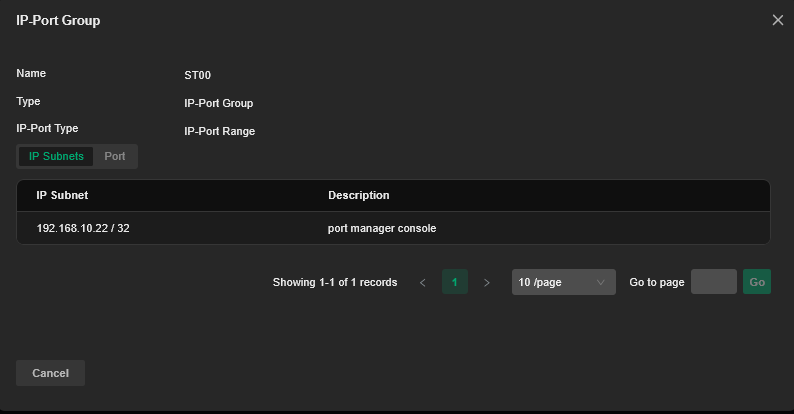
In the Default VLAN, there is a server managing antivirus software, with the IP address 192.168.10.22 (for example).
Objective:
I want to block all traffic from the LocalLabComputer network to the Default network,
but still allow two-way communication between the antivirus server and the hosts in the LocalLabComputer network.
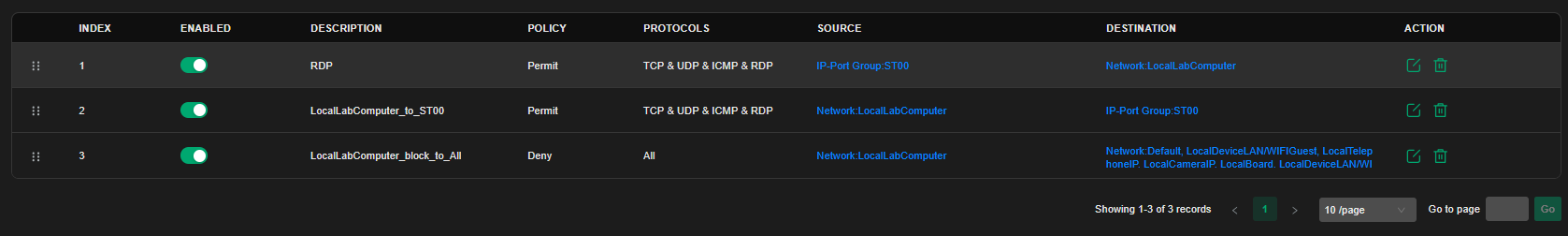
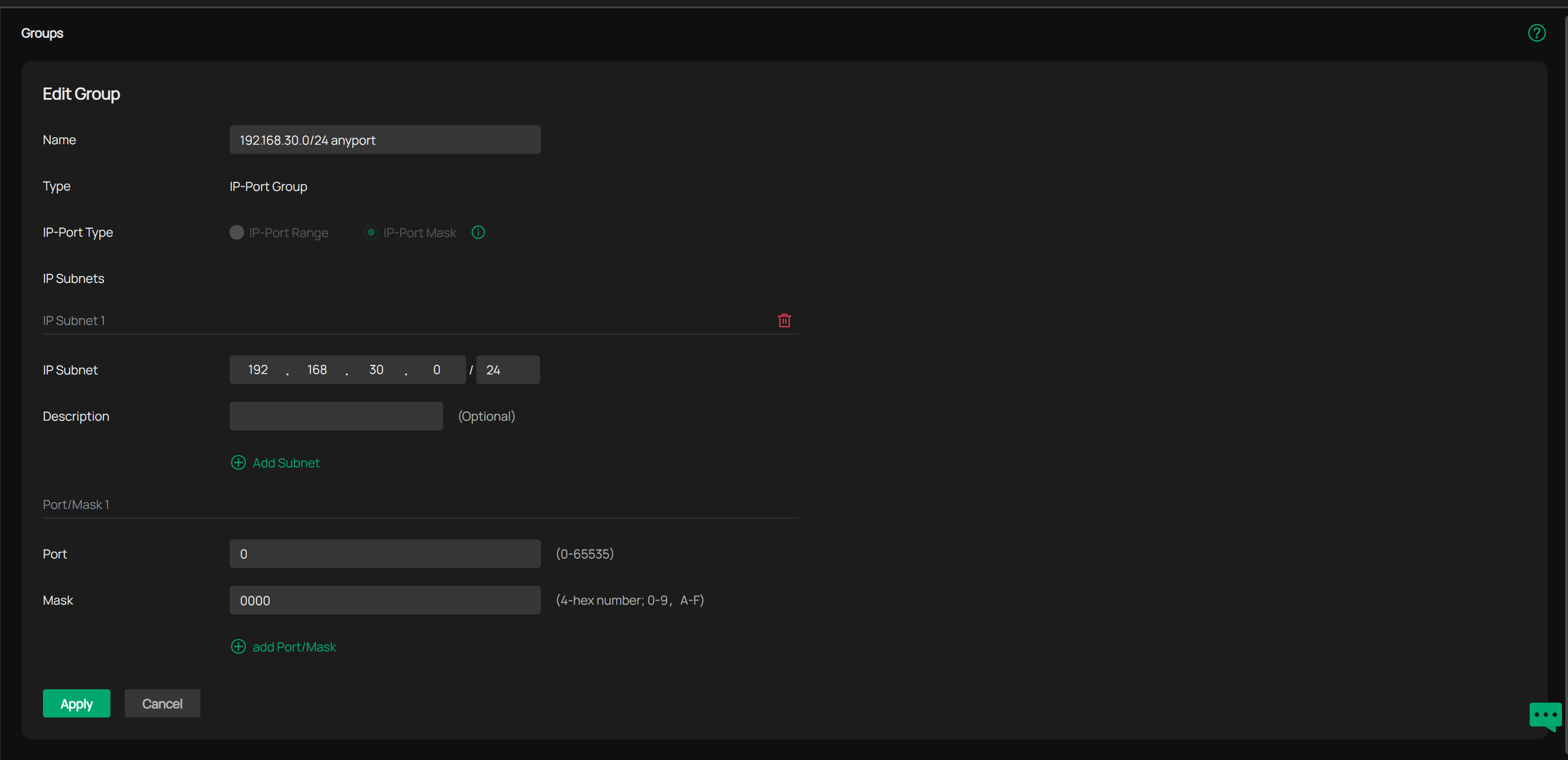
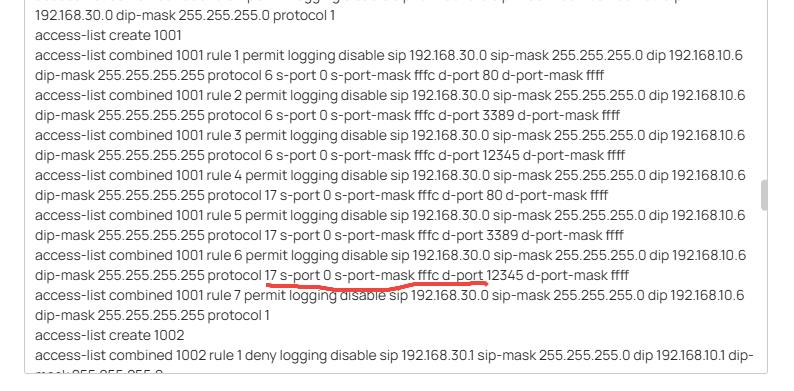
I have configured 3 ACL rules (in order):
-
Rule 1:
-
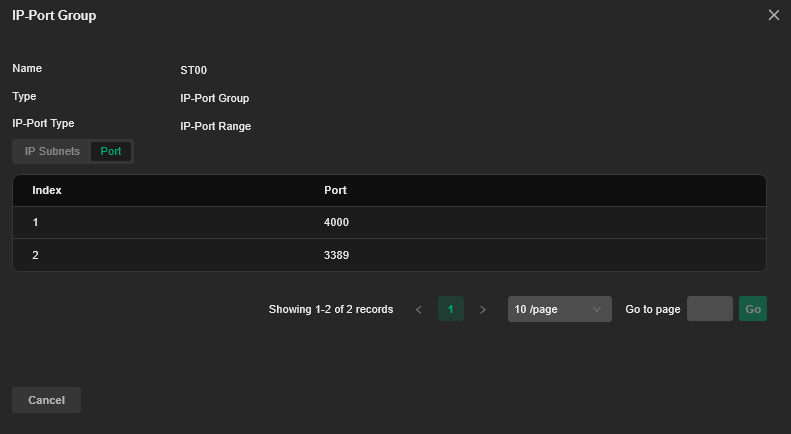
Source: IP-Port Group
ST00(the server) -
Destination:
Network: LocalLabComputer -
Permit: TCP, UDP, ICMP, RDP
-
-
Rule 2:
-
Source:
Network: LocalLabComputer -
Destination:
IP-Port Group: ST00 -
Permit: TCP, UDP, ICMP, RDP
-
-
Rule 3 (last one):
-
Source:
Network: LocalLabComputer -
Destination:
Network: Default -
Deny: All protocols
-
Problem:
-
From the
LocalLabComputernetwork, RDP and port 4000 connections to theDefaultVLAN are still working — even though they should be blocked. -
But from the
DefaultVLAN, RDP toLocalLabComputerdoesn't work — even though it should be allowed.
I'm wondering what I might have done wrong. Can someone point out where the mistake could be?
I forgot to add that these are rules made on Switch ACL