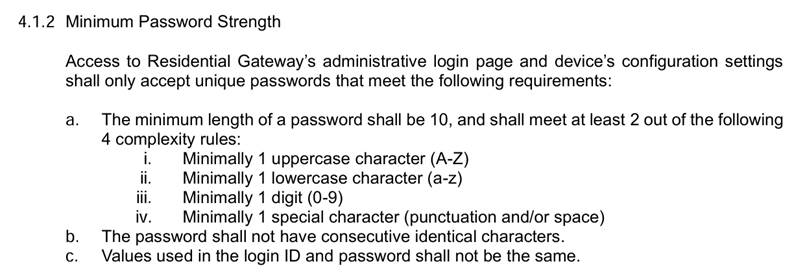
Device Account password requirments
Hello,
Setting up a new Omada software controller on Linux, version 5.15.24.17. This is our 6th or 7th controller we've set up over the last 2 years.
As part of the initial setup there is a section to enter the Device Account username and password. It appears that the password requirements have changed and are a bit ridiculous. Plus the error message is incorrect.
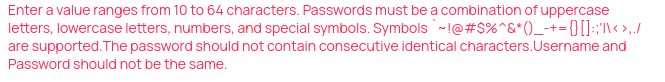
We have been using a very strong 20+ character password that meets all of the above requirements except that it has 2 consectutive characters. Failing a 20+ character password for this reason is silly.
And the error message is wrong. It reads "The password should not contain consectutive identical characters." The use of the word "should" implies that this is a recommendation and not a requirement. (The use of the word "must" implies requirement.) Unfortunately the set up page will not accept a password with two consectutive identical characters which means that this is a hard requirement.
The last time we set up a new controller a which was version 5.15.8.2 the no "consectutive identical characters" requirement was not present.
I totally understand the challenge of ensuring users create good passwords. Doing so is a good thing! However, arbitrary requirements is a bad thing.
A better approach would be to require a minimum amount bit entropy in the password and ensure that the entered password meets a minimum secure threshold.
Just my $0.02. But more than annoyed enough to write this up.