De-Auth for external verification portal
Hi, in our omada setup, we use the hardware controller: OC300. We have an external auth portal setup for our clients and employees.
we want to limit one employee or client to one device. we are storing mac and other details from last login in our database. can you please inform us any possible ways to de-authenticate a certain device (mac) from the network using any api or anything else
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
Thanks for the explanation. It's clear now.
Please see my answer below:
1. Is there a way to de-authenticate a previously authorized client via the Hotspot API or some other backend method?
>>Yes, you can do that via OpenAPI. Below is the document:
https://localhost:8043/doc.html#/00%20All/Authorized%20Client/cancelAuthClient
And you will find the related guide on page Cancel authentication the given client :
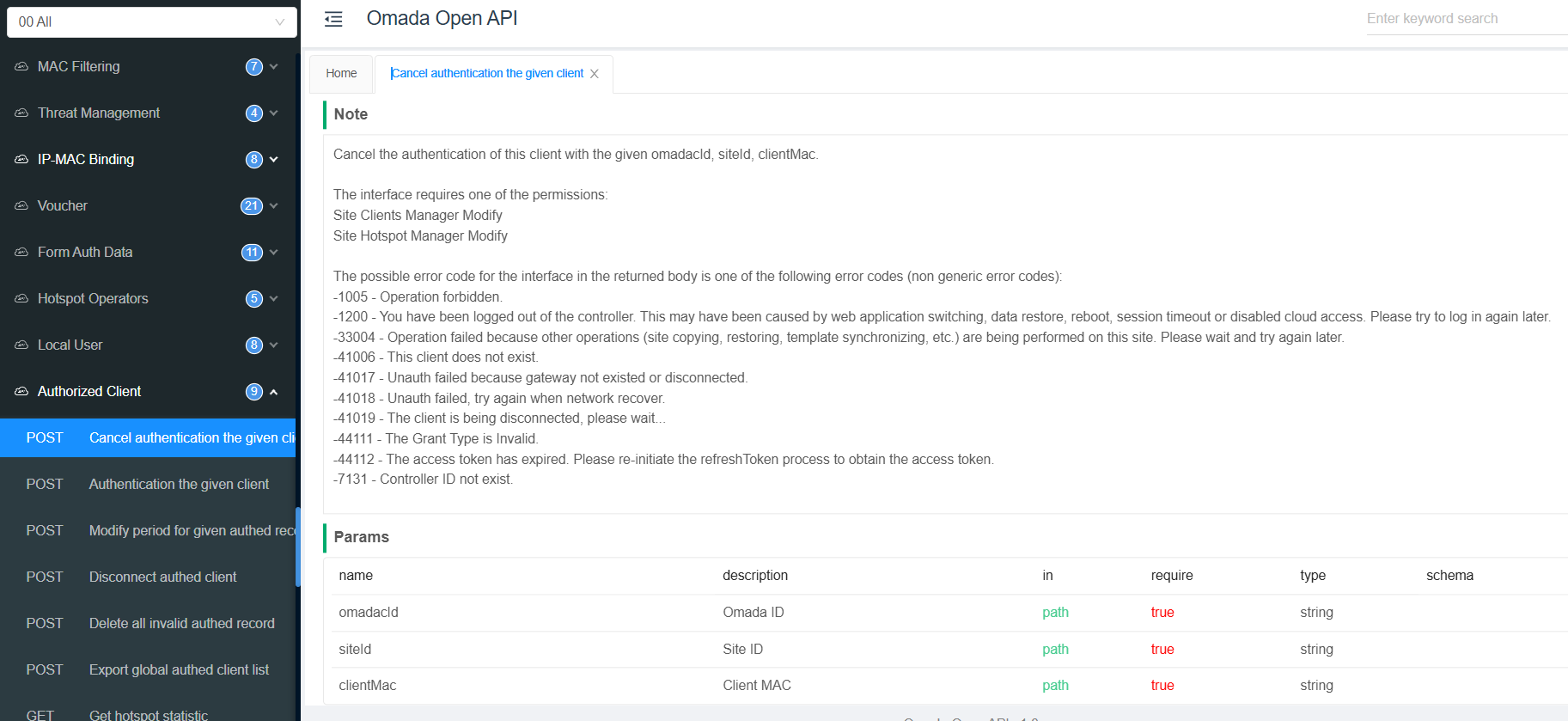
2. Or any known method to force a disconnect (session termination) from the backend, when duplicate login is detected?
>> You can also consider use the Local User hotspot portal via Omada controller, and limit only 1 users connecting for each user account.
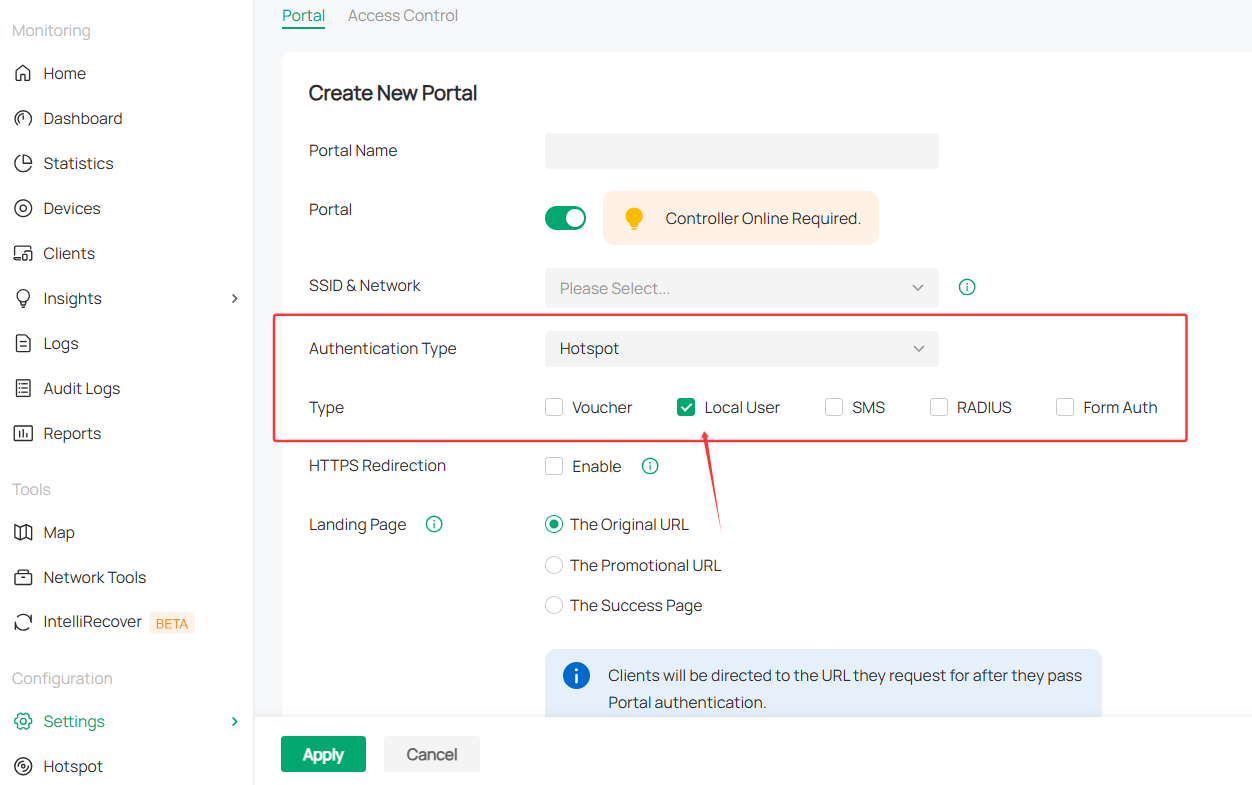
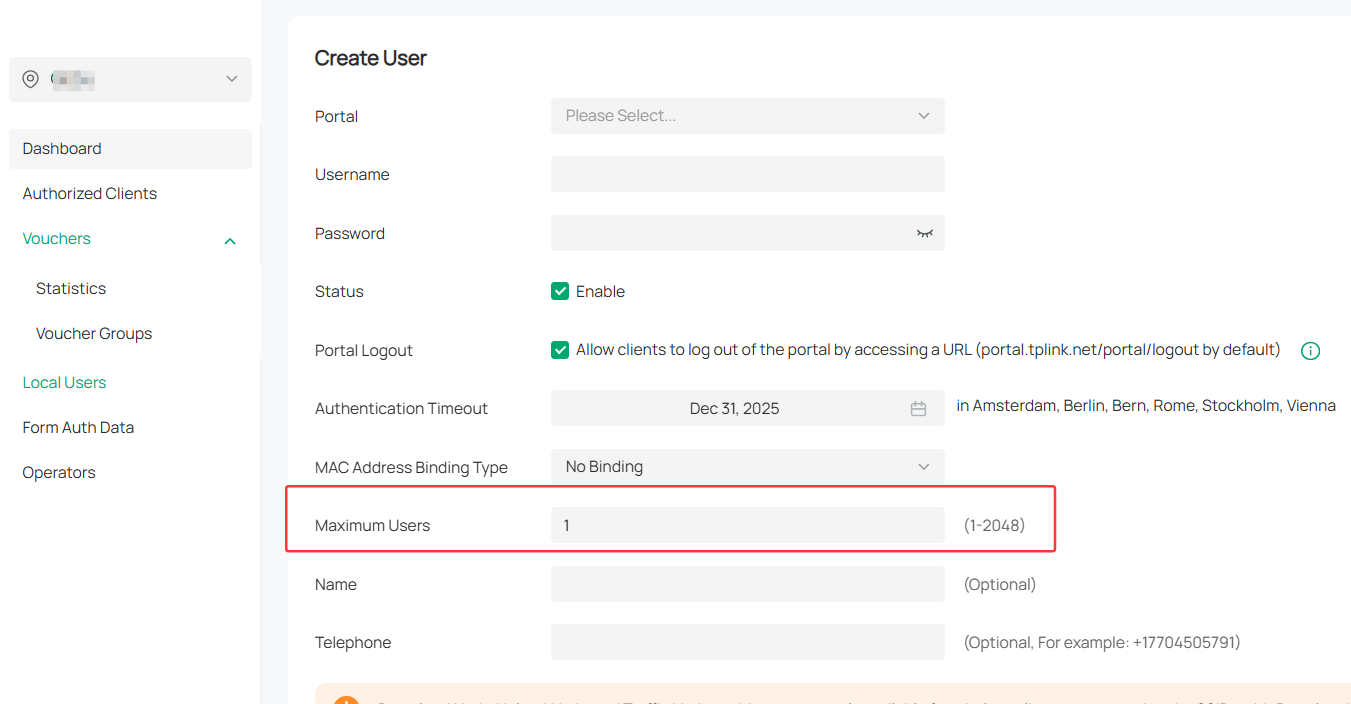
With this config, the local database is not needed.
- Copy Link
- Report Inappropriate Content
You can go to the Client list and Block those MAC addresses.
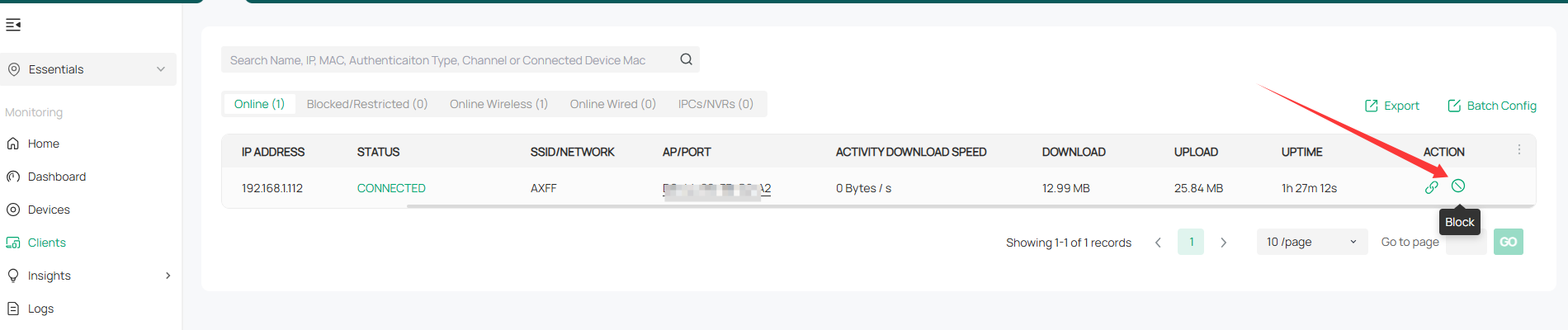
If that's not what you want, please give us more details, such as the model number of the SDN devices you are using, what do you want to de-auth exactly.
- Copy Link
- Report Inappropriate Content
Hi Vincent,
Thanks for the reply.
Just to clarify, we’re not looking to de-authenticate clients from the Omada controller interface directly.
We’re using an external portal with TP-Link’s Hotspot API, where authentication is handled entirely by our backend via the Auth API (not by the controller). The Omada SDN simply redirects users to our custom login page. After that, the Auth API is used to authorize or deny access based on our internal logic.
In our case, all employee credentials and sessions are managed in a local database, and we’re trying to enforce a “one device per login ID” policy. That means:
If an employee logs in from a second device using the same credentials,
The first device should be de-authenticated or disconnected,
So only one active session exists per employee at any given time.
We’re already tracking MAC addresses and session data per user in our backend, but we need a method to de-auth a client via the Hotspot API or any other backend method, not just block them permanently from the controller UI.
So the key questions are:
1. Is there a way to de-authenticate a previously authorized client via the Hotspot API or some other backend method?
2. Or any known method to force a disconnect (session termination) from the backend, when duplicate login is detected?
My Current Setup
1. Controller
TP-Link Omada OC300 (Hardware Controller)
2. Switches
TP-Link TL-SG2428P (PoE+ Managed Switch)
3. Access Points
TP-Link EAP225
TP-Link EAP610
4. Gateway / Router
TP-Link ER8411 (Enterprise Router)
5. Captive Portal & Backend
Custom External Captive Portal (Hosted on local server)
Handles login UI and user interaction
Verifies credentials with internal systems
Authentication via TP-Link Hotspot API
Using the auth API to authorize clients programmatically
Not relying on the Omada controller for authentication logic
6. Database & Session Logic
Local Database for employee credentials & session tracking
Tracks MAC address, login ID, timestamp
Credentials are the same as those used internally by employees
Enforces a “one-device-per-user” policy
On duplicate login, previous session should be de-authenticated or disconnected from backend
Looking forward to your suggestions.
Thanks again,
- Copy Link
- Report Inappropriate Content
Thanks for the explanation. It's clear now.
Please see my answer below:
1. Is there a way to de-authenticate a previously authorized client via the Hotspot API or some other backend method?
>>Yes, you can do that via OpenAPI. Below is the document:
https://localhost:8043/doc.html#/00%20All/Authorized%20Client/cancelAuthClient
And you will find the related guide on page Cancel authentication the given client :

2. Or any known method to force a disconnect (session termination) from the backend, when duplicate login is detected?
>> You can also consider use the Local User hotspot portal via Omada controller, and limit only 1 users connecting for each user account.


With this config, the local database is not needed.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 316
Replies: 3
Voters 0
No one has voted for it yet.
