IDS/IPS Feature, Actual Functional Behavior Questions
Hello,
Configuration is Windows Software Controller 5.15.20.21 and gateway is ER8411
The questions are about the actual behavior and functionality of the IDS/IPS feature. It is not at all clear in the documentation. BTW, the lack of feature functional-behavior is not available generally in the documentation.
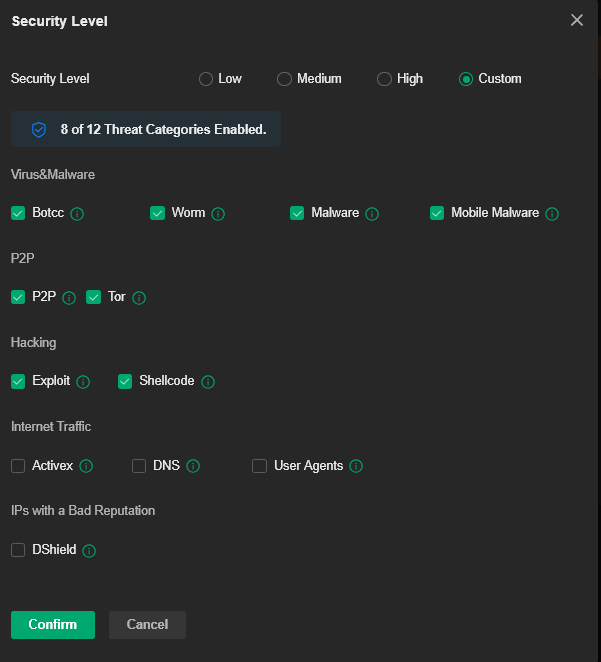
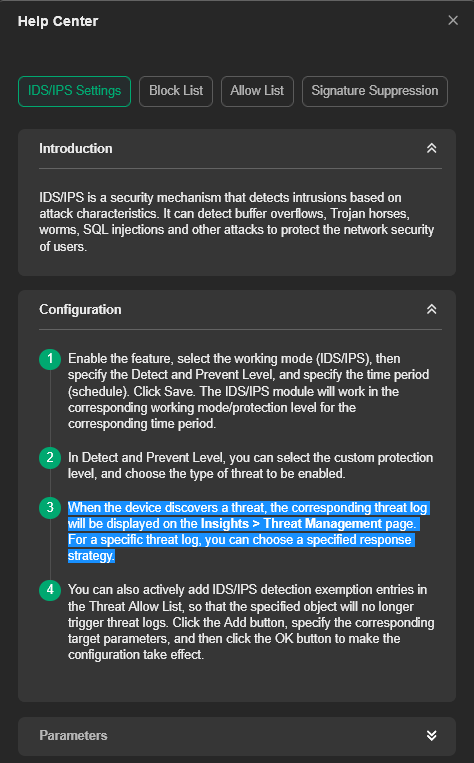
Go to > Settings > IDS/IPS Settings > Intrusion Detection/Prevention, button is ON > Security Level > check box for P2P is ON > Detect and Prevent (IPS) button is ON
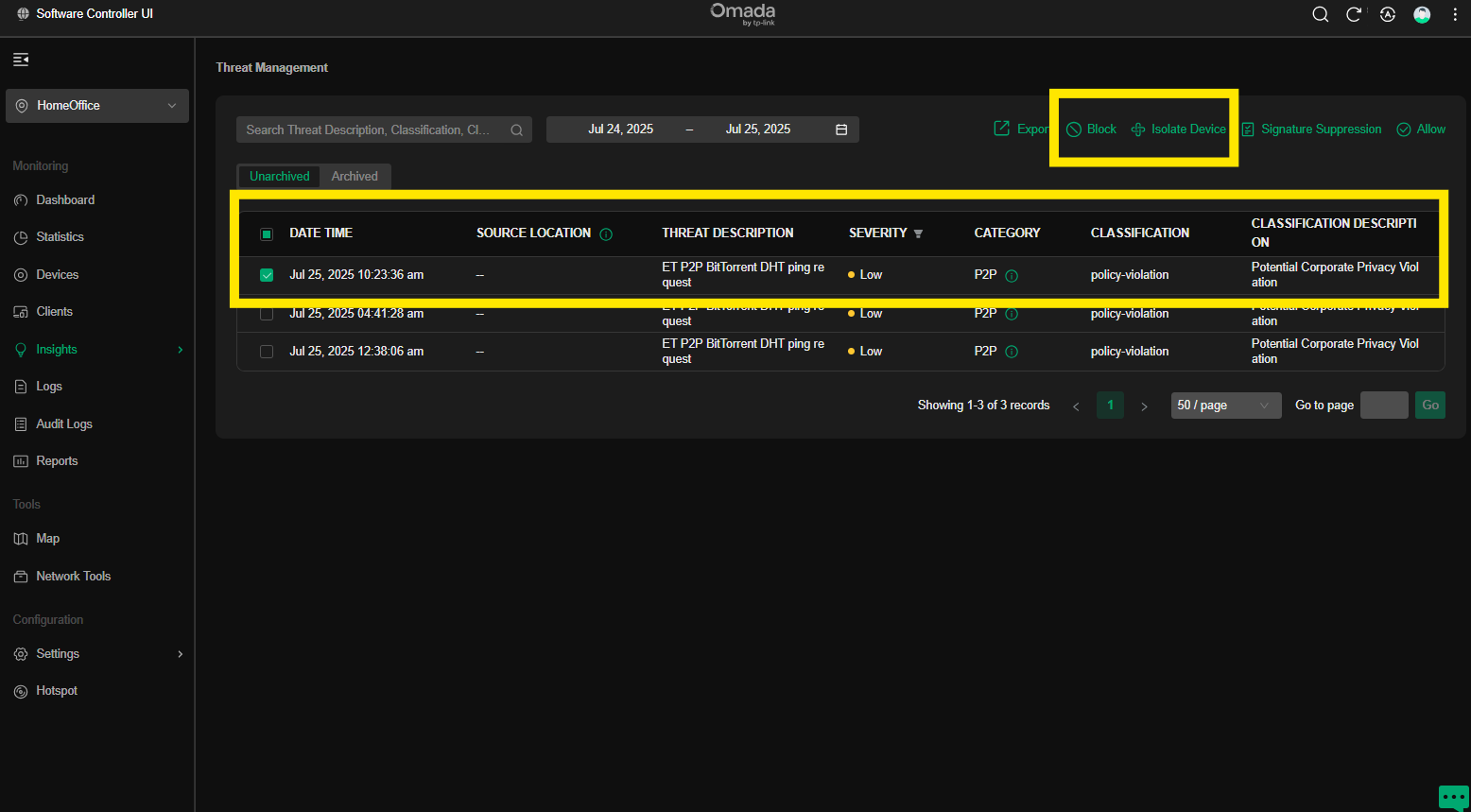
Next go to > Insights > Threat Management
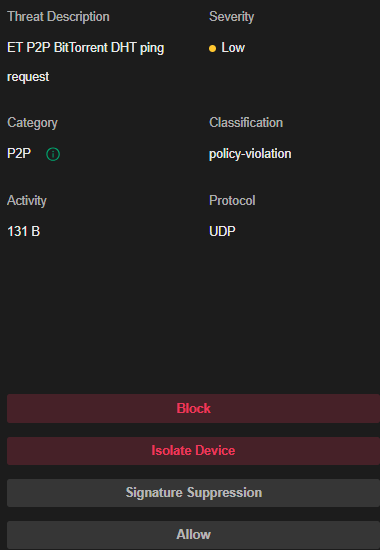
There I find Policy Violations, ET P2P BitTorrent DHT ping.
See attached screenshot.
Questions:
What is the behavior of this IDS/IPS feature?
1) With "Detect and Prevent (IPS)" ON - is this ping packet automatically prevented from going out to the WAN or to the destination lP address or what?
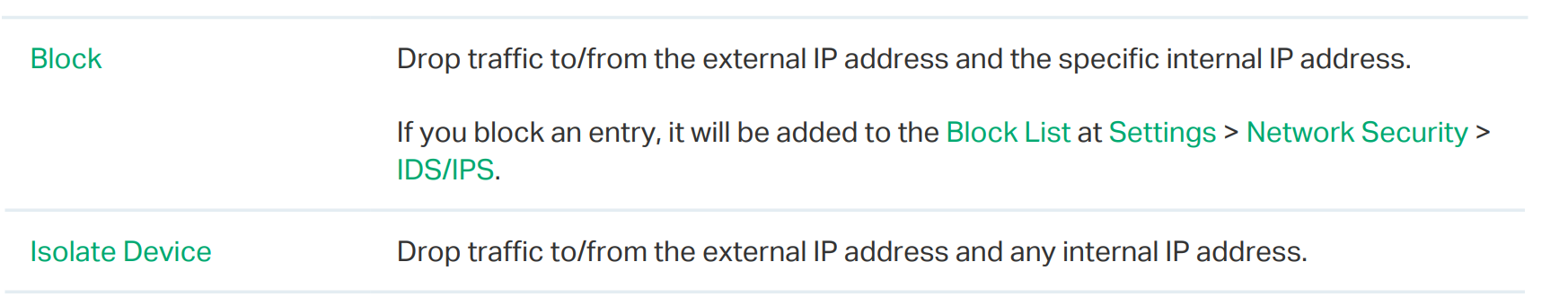
2) If this line item is selected and "Block" is applied, what is the behavior - is the source IP blocked from the WAN, or the LAN or destination IP or what?
3) if the line item is selected and "Isolate Device" is applied, what is the behavior - is the source IP or MAC of the device blocked from the WAN or LAN or what?
Thanks
Michael Downs
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
1. Inbound and outbound as long as it fits the signature and pattern.
2. Destination, the external server.
3. See the controller interface, which contains the explanation.
- Copy Link
- Report Inappropriate Content
MDowns wrote
Yeah, that is exactly what I mean by a lack of behavior specifics in the documentation and sorry, your explanation is unclear.
What is meant by "Block" from what to what? Inbound from the offending IP address or Outbound to the offending outbound IP address or what?
What is meant by "Isolate Device" from what to what? From EVERYTHING? The Source Device is Isolated and can no longer communicate on the LAN or WAN or what?
Also,
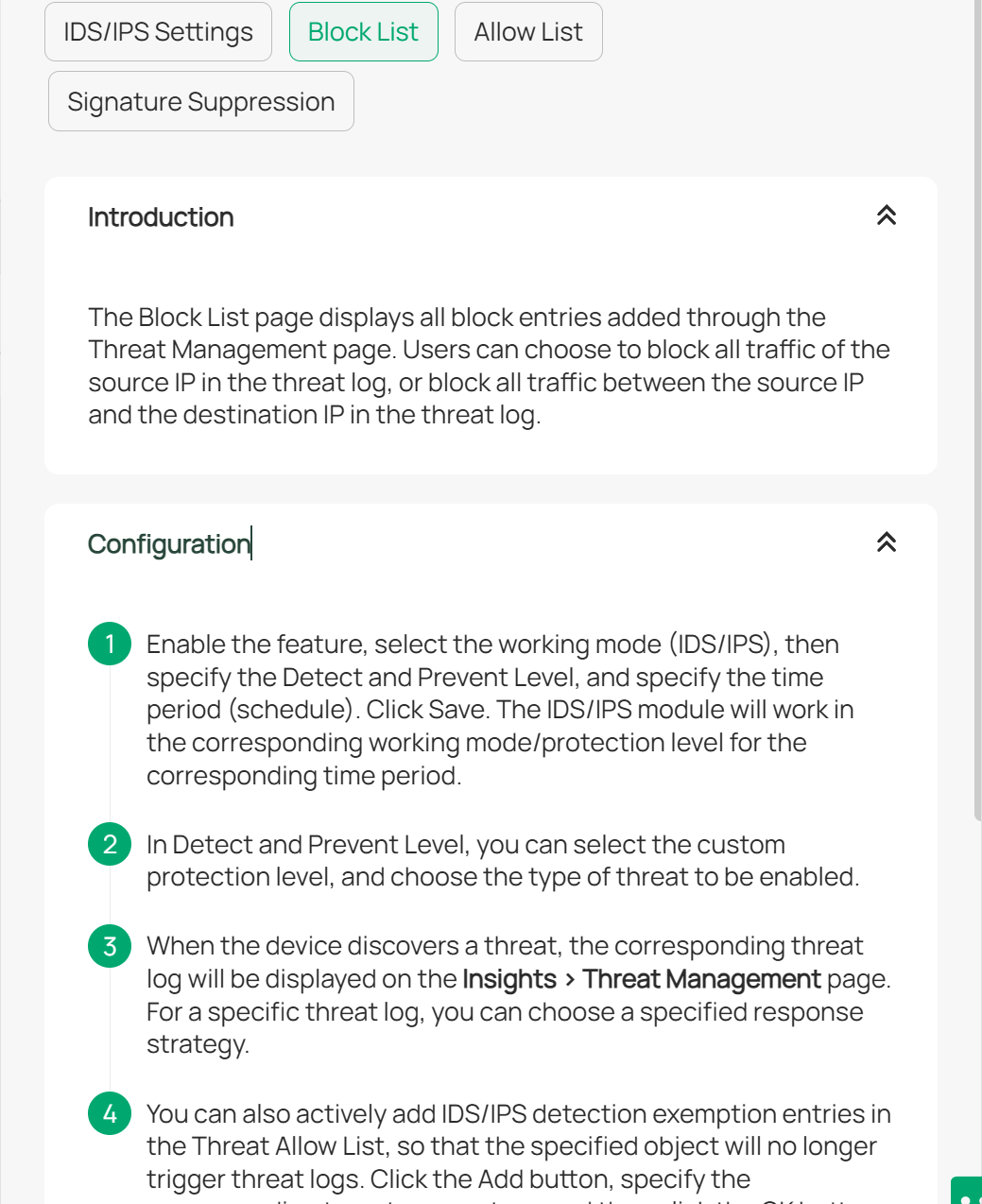
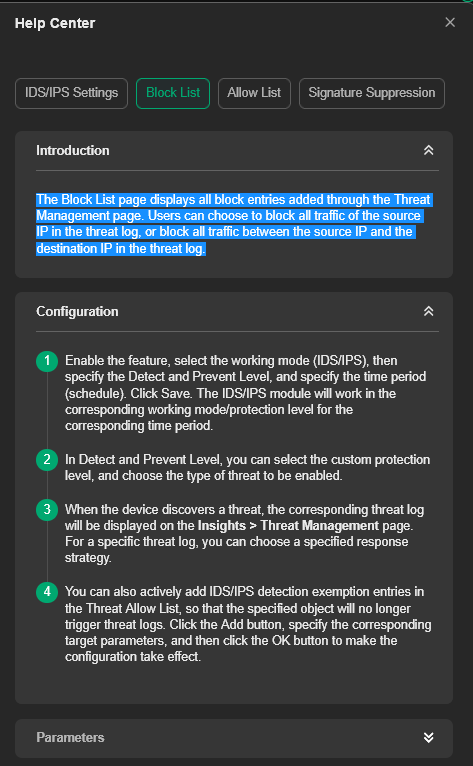
In the screen shots, the explanation says "Users can choose to block all traffic of the source IP in the threat log, or block all traffic between the source IP and the destination IP in the threat log."
Does that mean that if the source IP is a device on the LAN and has in this case, Outbound traffic, "block all traffic" means all traffic, In and Out is blocked for that device on the LAN? It cannot communicate at all? Or does it mean just the traffic between the Source (LAN) and Destination (WAN)?
Does that mean that if the source IP is a device on the LAN and has in this case, Outbound traffic, "block all traffic between the source IP and the destination IP" means just the traffic between the two Source/Desination IPs are blocked, or is all traffic for both In and Out are blocked for both IPs?
In the threat log, if none of the threat items are selected, then are the matching packets automatically blocked in IPS mode, or must a specific threat response be selected?
In the Threat Reponse item selection, what specifically is done by "Block" and what specifically is done by "Isolate Device"?
That is really what this message thread is about. Can you be more specific?
Thanks!
1. Blocking the device in the LAN that fits the signature pattern does not mean blocking the device from normal network access.
It's like the DPI that monitors the session and signature in every connection. And it blocks the traffic regardless of the direction as long as that fits the signature. The system contains a database that contains the common behavior and signature.
2. If A, a device, B, a server, and their connection contain a pattern like P2P, the traffic will be blocked if you use the block. This is to prevent the possible P2P connection or threat in the IDS list. It might contain a false alarm if the database is not updated. So, this requires an allow list if a false alarm is triggered and a device is blocked from accessing server B. We only monitor the pattern and signature.
3. IDS is enabled, and it is working to stop and prevent. Anything in the Insight tab only provides the informational style details without ability to config. However, threat Management is slightly different, as the literal meaning says, it displays the triggered events and offers you more options to fine-tune or allow if there is a mistake or false alarm.
4. Block means that as long as the source and destination, both directions, match the behavior and signature, it will be blocked.
Isolate Device means that as long as the destination matches the behavior and signature, it will be blocked. And its Internet access will be stopped because it triggers the protection system.
- Copy Link
- Report Inappropriate Content
1. Inbound and outbound as long as it fits the signature and pattern.
2. Destination, the external server.
3. See the controller interface, which contains the explanation.

- Copy Link
- Report Inappropriate Content
Yeah, that is exactly what I mean by a lack of behavior specifics in the documentation and sorry, your explanation is unclear.
What is meant by "Block" from what to what? Inbound from the offending IP address or Outbound to the offending outbound IP address or what?
What is meant by "Isolate Device" from what to what? From EVERYTHING? The Source Device is Isolated and can no longer communicate on the LAN or WAN or what?
Also,
In the screen shots, the explanation says "Users can choose to block all traffic of the source IP in the threat log, or block all traffic between the source IP and the destination IP in the threat log."
Does that mean that if the source IP is a device on the LAN and has in this case, Outbound traffic, "block all traffic" means all traffic, In and Out is blocked for that device on the LAN? It cannot communicate at all? Or does it mean just the traffic between the Source (LAN) and Destination (WAN)?
Does that mean that if the source IP is a device on the LAN and has in this case, Outbound traffic, "block all traffic between the source IP and the destination IP" means just the traffic between the two Source/Desination IPs are blocked, or is all traffic for both In and Out are blocked for both IPs?
In the threat log, if none of the threat items are selected, then are the matching packets automatically blocked in IPS mode, or must a specific threat response be selected?
In the Threat Reponse item selection, what specifically is done by "Block" and what specifically is done by "Isolate Device"?
That is really what this message thread is about. Can you be more specific?
Thanks!
- Copy Link
- Report Inappropriate Content
MDowns wrote
Yeah, that is exactly what I mean by a lack of behavior specifics in the documentation and sorry, your explanation is unclear.
What is meant by "Block" from what to what? Inbound from the offending IP address or Outbound to the offending outbound IP address or what?
What is meant by "Isolate Device" from what to what? From EVERYTHING? The Source Device is Isolated and can no longer communicate on the LAN or WAN or what?
Also,
In the screen shots, the explanation says "Users can choose to block all traffic of the source IP in the threat log, or block all traffic between the source IP and the destination IP in the threat log."
Does that mean that if the source IP is a device on the LAN and has in this case, Outbound traffic, "block all traffic" means all traffic, In and Out is blocked for that device on the LAN? It cannot communicate at all? Or does it mean just the traffic between the Source (LAN) and Destination (WAN)?
Does that mean that if the source IP is a device on the LAN and has in this case, Outbound traffic, "block all traffic between the source IP and the destination IP" means just the traffic between the two Source/Desination IPs are blocked, or is all traffic for both In and Out are blocked for both IPs?
In the threat log, if none of the threat items are selected, then are the matching packets automatically blocked in IPS mode, or must a specific threat response be selected?
In the Threat Reponse item selection, what specifically is done by "Block" and what specifically is done by "Isolate Device"?
That is really what this message thread is about. Can you be more specific?
Thanks!
1. Blocking the device in the LAN that fits the signature pattern does not mean blocking the device from normal network access.
It's like the DPI that monitors the session and signature in every connection. And it blocks the traffic regardless of the direction as long as that fits the signature. The system contains a database that contains the common behavior and signature.
2. If A, a device, B, a server, and their connection contain a pattern like P2P, the traffic will be blocked if you use the block. This is to prevent the possible P2P connection or threat in the IDS list. It might contain a false alarm if the database is not updated. So, this requires an allow list if a false alarm is triggered and a device is blocked from accessing server B. We only monitor the pattern and signature.
3. IDS is enabled, and it is working to stop and prevent. Anything in the Insight tab only provides the informational style details without ability to config. However, threat Management is slightly different, as the literal meaning says, it displays the triggered events and offers you more options to fine-tune or allow if there is a mistake or false alarm.
4. Block means that as long as the source and destination, both directions, match the behavior and signature, it will be blocked.
Isolate Device means that as long as the destination matches the behavior and signature, it will be blocked. And its Internet access will be stopped because it triggers the protection system.

- Copy Link
- Report Inappropriate Content
I have a question regarding IDS only.
After one year of now owning the ER8411, I finally decided ot give DPI and IDS/IPS a try again. To my surprise, DPI now actually works and able to determine applications passing through (never worked before when I first deployed it).
However, IDS still doesn't do anything for me. I expect that it would log something (anything). I have done test like downloading eicar dot org test files and doing "curl -A "BlackSun" www.google.com" but nothing seems to log. I rebooted the ER8411 several times and running the latest firmware (1.3.2 Build 20250610 Rel.85512) as well the latest Omada Controller (Ubuntu) (5.15.24.18).
Should I be seeing some kind of activity/log with just IDS enabled?
- Copy Link
- Report Inappropriate Content
Information
Helpful: 2
Views: 705
Replies: 4
Voters 0
No one has voted for it yet.
