Gateway ACL LAN to LAN feature is not working
I have configured VLANs 10, 20, 30, 100, and 200. The IPs are 192.168.x.0/24 (x being the VLAN ID).
VLAN 100 and 200 are applied on a SSID broadcast by my APs. I want to block access of VLAN 100 and 200 to all other VLANs. The VLANs are created with the purpose as interface, so routing is done on the gateway.
Gateway ACLs proven to be useless as I can still ping other VLANs when Im in both VLAN 100 and 200. A change the Switch ACL fixed the problem. What is the issue here and why does Gateway ACL not work?
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
I just finished testing the use of an ACL rule to deny access to the gateway from selected VLANs. Here is the rule I used:
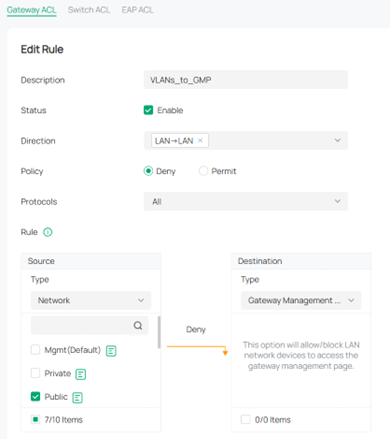
For testing I used an HP laptop and a Windows PC. Here are the results:
Test 1
- ACL configured to deny all protocols
- PC connected to the controller via the Mgmt VLAN (wired)
- Laptop connected to the Public VLAN via Wi-Fi
- Laptop is unable to connect to the gateway GUI
- Laptop unable to ping the gateway
- Laptop CAN connect to the internet and navigate without any issues
Test 2
- Laptop connected to a different (IoT) VLAN via Wi-Fi
- Connection/ping results same as in Test 1
Test 3
- Laptop connected to controller via Mgmt VLAN Wi-Fi
- SG2008 switch port for the PC changed to the VLAN profile “Public”
- PC rebooted to obtain a new IP address on the Public VLAN
- PC is unable to connect to the gateway GUI
- PC unable to ping the gateway
- PC can connect to the internet and navigate without any issues
Conclusion: Because other forum members have reported issues with different gateway models, it appears that the issue of no internet access when using all protocols in the ACL rule is a problem that does not affect all gateways.
Related links:
1. https://community.tp-link.com/en/business/forum/topic/841238
2. https://community.tp-link.com/en/business/forum/topic/642230
3. https://www.reddit.com/r/TPLink_Omada/comments/196s5gu/block_gateway_management_page_also_block_internet/
- Copy Link
- Report Inappropriate Content
Generally gateway ACLs still allow all the gatewai IPs of all vlans hosted on the gateway to be pingable. Why? who knows, just how it is.
In all other ways gateway lan<>lan ACLs work fine
- Copy Link
- Report Inappropriate Content
Thank you for your post. They should indeed work. How did you configure the ACL? Two ACL entries are required here, or you should enable bidirectional ACL blocking when configuring—once enabled, two ACL entries will be created automatically.
- Copy Link
- Report Inappropriate Content
I just came across this thread so I may be late in commenting here. In my network, the gateway ACLs work fine in preventing VLANs from reaching each other EXCEPT for the VLAN interfaces on the gateway. I can still ping the VLAN gateway address and navigate to the VLAN gateway's GUI. Just yesterday, I discovered that by creating an additional gateway rule to deny access for certain VLANs to the destination "Gateway Management Page", those VLANs can no longer access the gateway GUI. Setting the protocols to "All" also prevents the VLAN devices from pinging the gateway. In my case, I sometimes use a laptop on a particular VLAN for maintenance and testing. I changed the new gateway ACL to only deny the TCP protocol and this allows me to ping the gateway when needed.
- Copy Link
- Report Inappropriate Content
Be careful setting a lan<>lan ACL to the gateway page with "ALL" protocols - this will totally kill internet access for the vlans in the rule. (what actually kills it is having the ICMP protocol selected either on its own or with others / all). Selecting TCP is enough to prevent GMP GUI access
- Copy Link
- Report Inappropriate Content
I suspect that this may be gateway dependent or perhaps a flaw in the firmware. On my gateway, setting the protocols to "All" did not kill internet access for the VLANs involved.
- Copy Link
- Report Inappropriate Content
Interesting, it certainly does on the 605 v2, 8411 and 7206 v2 i have on different sites! (all on the latest too)
It didnt used to - maybe a year or so ago something changed, even clive confirmed it in some random post i saw of his on a thread ages ago
- Copy Link
- Report Inappropriate Content
I am going to look into this a little further. I only briefly tested everything when I added the new rule and everything was working OK. Later I will post the results here.
- Copy Link
- Report Inappropriate Content
Yeah, worth looking at since you have a different router model
As far as i can tell, the "Gateway Management Page" isnt just the web gui, but the entire WAN Side / Internal side of "The Router Itself" as by using a location group WAN IN > GMP block you can also prevent geographic VPN login attempts as well, works the same for a IP_Group too
- Copy Link
- Report Inappropriate Content
I just finished testing the use of an ACL rule to deny access to the gateway from selected VLANs. Here is the rule I used:

For testing I used an HP laptop and a Windows PC. Here are the results:
Test 1
- ACL configured to deny all protocols
- PC connected to the controller via the Mgmt VLAN (wired)
- Laptop connected to the Public VLAN via Wi-Fi
- Laptop is unable to connect to the gateway GUI
- Laptop unable to ping the gateway
- Laptop CAN connect to the internet and navigate without any issues
Test 2
- Laptop connected to a different (IoT) VLAN via Wi-Fi
- Connection/ping results same as in Test 1
Test 3
- Laptop connected to controller via Mgmt VLAN Wi-Fi
- SG2008 switch port for the PC changed to the VLAN profile “Public”
- PC rebooted to obtain a new IP address on the Public VLAN
- PC is unable to connect to the gateway GUI
- PC unable to ping the gateway
- PC can connect to the internet and navigate without any issues
Conclusion: Because other forum members have reported issues with different gateway models, it appears that the issue of no internet access when using all protocols in the ACL rule is a problem that does not affect all gateways.
Related links:
1. https://community.tp-link.com/en/business/forum/topic/841238
2. https://community.tp-link.com/en/business/forum/topic/642230
3. https://www.reddit.com/r/TPLink_Omada/comments/196s5gu/block_gateway_management_page_also_block_internet/
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 508
Replies: 9
Voters 0
No one has voted for it yet.
