Ok, im stuck on this! Direct Side-Network VPN injection flakey....
This is complex, so bear with me
For maximum security, and to pass audit, i want to completely limit the ability of VPN connected client to access things - even gateway GUIs, which, post 5.15 firmwares - as confirmed by clive - are no longer blocked for IPsec clients regardless of gateway ACL entries.
My solution was to implement a side-network "direct injection" VPN
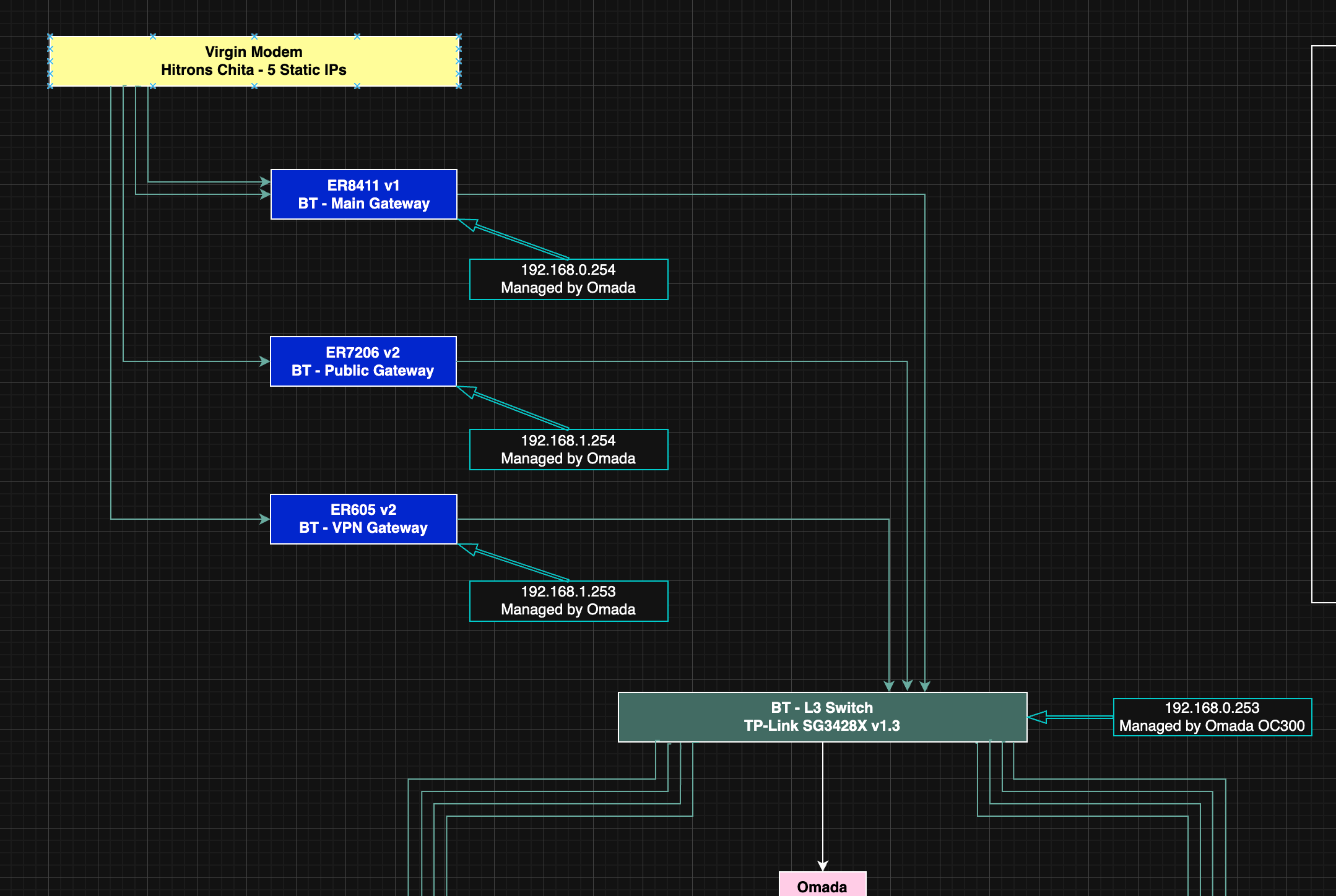
How this works
Main network - ER8411 > SG3428X > Stuff. All vlans are switch routed and hosted by SVIs on the 3428X. Works perfect
Networks to be accessible to VPN - 192.168.0.0/20
VPN Network - ER605 (obtained new running 2.2.6). Has an interface matching main network management vlan. VPNs set up - Local networks 192.168.0.0/20, Remotes 172.16.0.0/12
Gateway Static route 192.168.0.0/20 > Main network Management interface on SG3428X
SG3428X static route 172.16.0.0/12 > ER605 hosting the VPNs
ER605 has WAN>IN and LAN>WAN ACLs to control what i want allowed between remote and local vlans, and blocking IP_Port_Groups to various network devices and Gateway GUIs on the main networks.
Basic Topology diagram
All of this works great. I can connect to the VPNs on the ER605 v2, access main network resources, everything i want is blocked etc etc
Now - the problem is - the VPN sometimes seems to go "dead" for up to a minute at a time. No traffic to/from the main switch SG3428X. When its "dead" i can still access the GUI of the ER605 so i know the VPN tunnel is still active. Im fairly sure its not the route from the switch to the ER605 as other routes it has always work without issues.
Why is the VPN route from the ER605 v2 to the Switch sometimes going dead for up to a minute at a time but the VPN tunnel to the 605 remains active?
Other things i have tested
- Swapped the 605 running 2.2.6 for one with 2.3.0 - same issue
- Changed the switch the gateway route points to for another and reconfigured internal main routing to match - same issue
- Added VLAN interfaces on the ER605 to match each one accessible on the main network and set routing for each subnet to point to the direct SVI of the switch for the matching subnet - same issue
- Tried this with a ER7206 v2 running 2.2.3 - same issue
- Hosting the VPNs directly on the ER8411 of the main site - never an issue, but cant apply the same granular ACLs as i need any more as its on 1.3.2

