ER8411 FW 1.3.3 & 1.3.6 - ER605v2 FW 2.3.1 - VPN Passthrough on Windows / macOS not working
ER8411 Firmware 1.3.3, 1.3.5 and 1.3.6 & ER605 v2 Firmware 2.3.1 – VPN Passthrough issues
Testing began on a completely factory reset ER8411 running 1.3.6 – no configs. Not even the initial login user/password set, standalone mode.
Identical testing on ER605 v2 running 2.3.1 with the exact same results. Documenting ER8411 here.
Topology:
Modem <WAN 4> ER8411 <LAN 11> PC
No other devices on network
From the factory reset state.
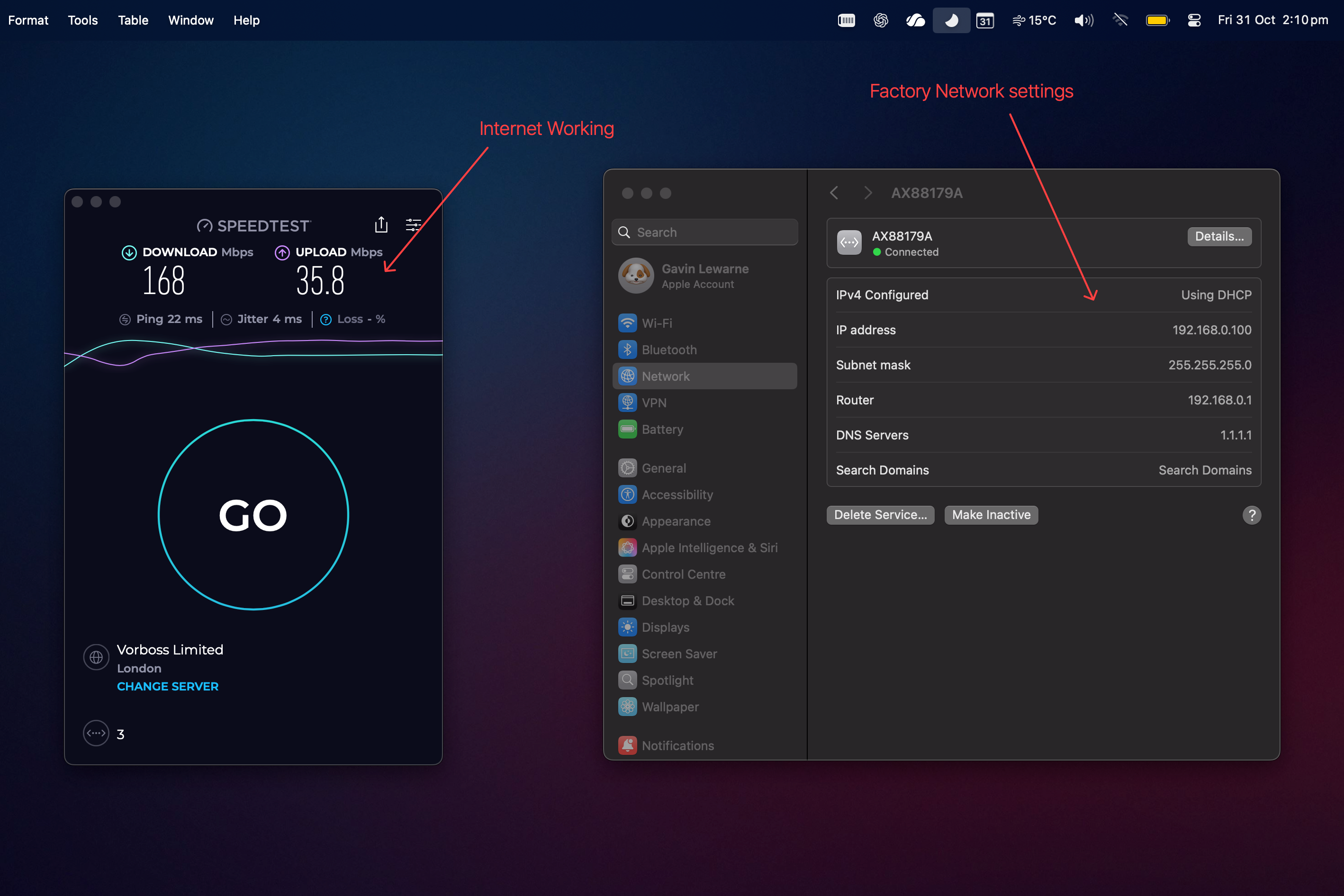
IPSec Client to Site VPN connected successfully – Connected to VPN server on ER7206 at independant location - not an omada site, Client-To-Site mode, Target IP range 192.168.1.X
--- Success – can ping and access remote devices and GUIs ---
Now, Gateway will have its default LAN changed to match my omada site management vlan and adopted to controller with its proper IP
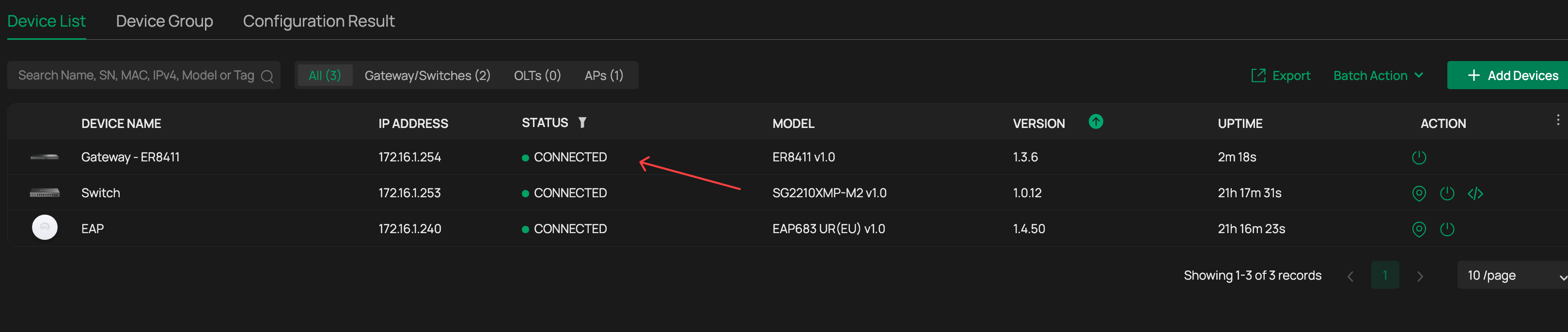
VPN is now reconnected – Remote range still 192.168.1.X
Ping to the remote gateway 192.168.1.1 is successful
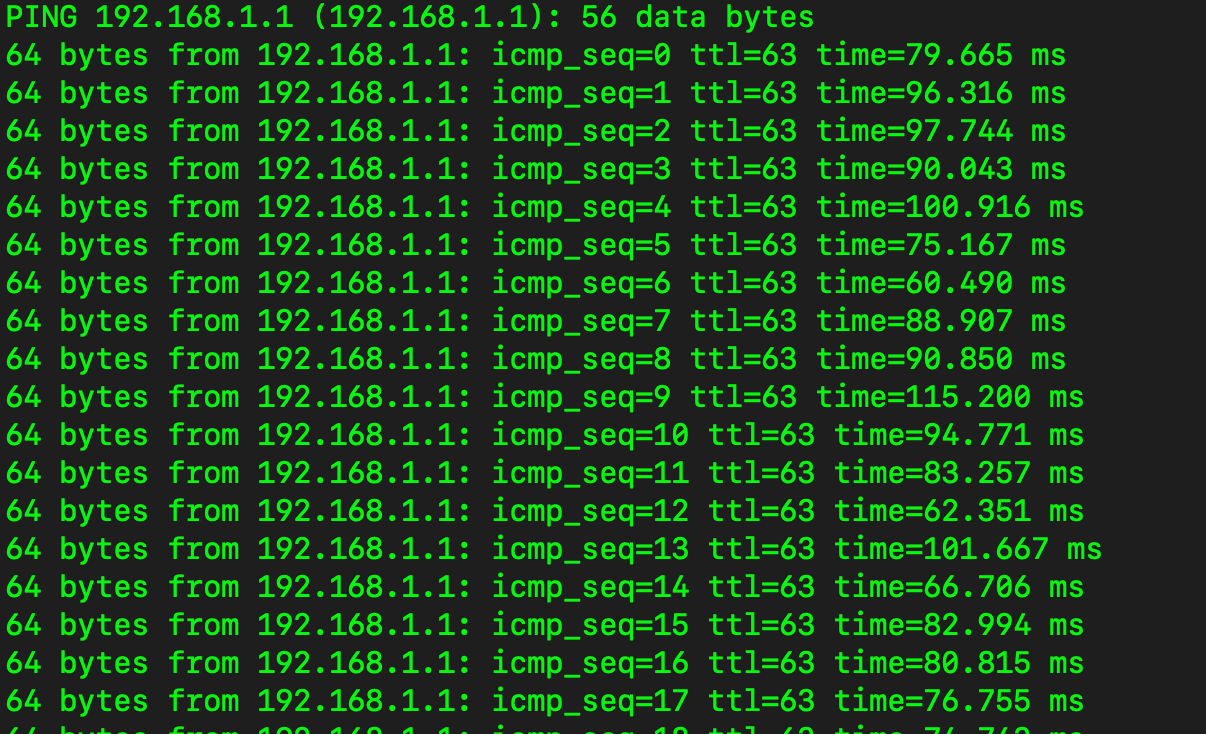
CANNOT load the GUI for it, or for anything else on that network

All ACLs are disabled, there are no NAT rules
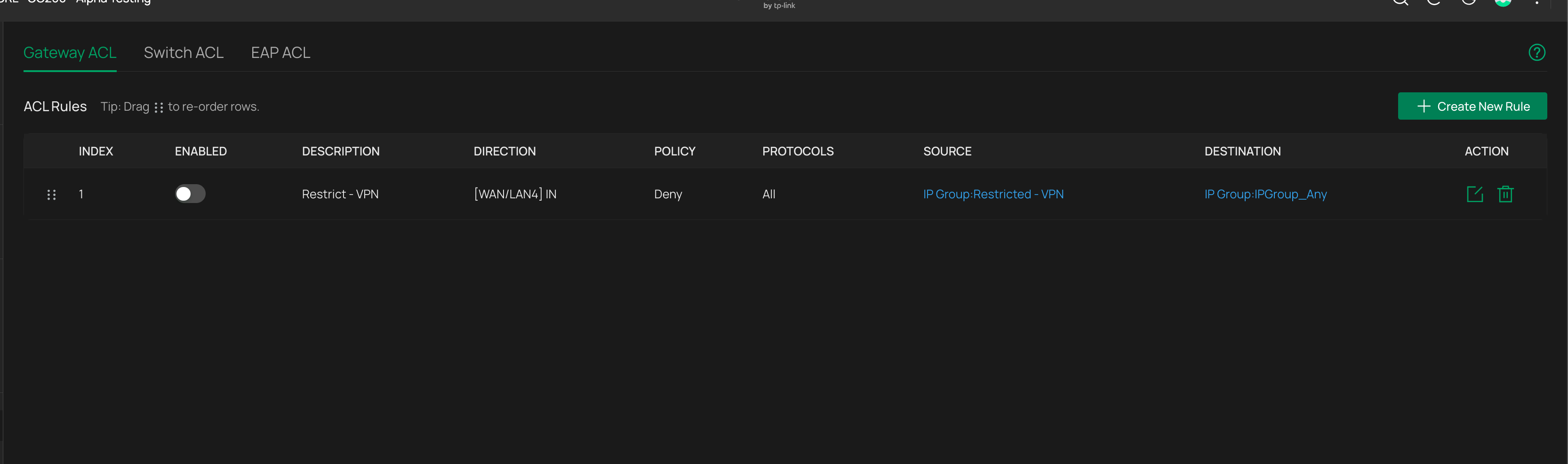
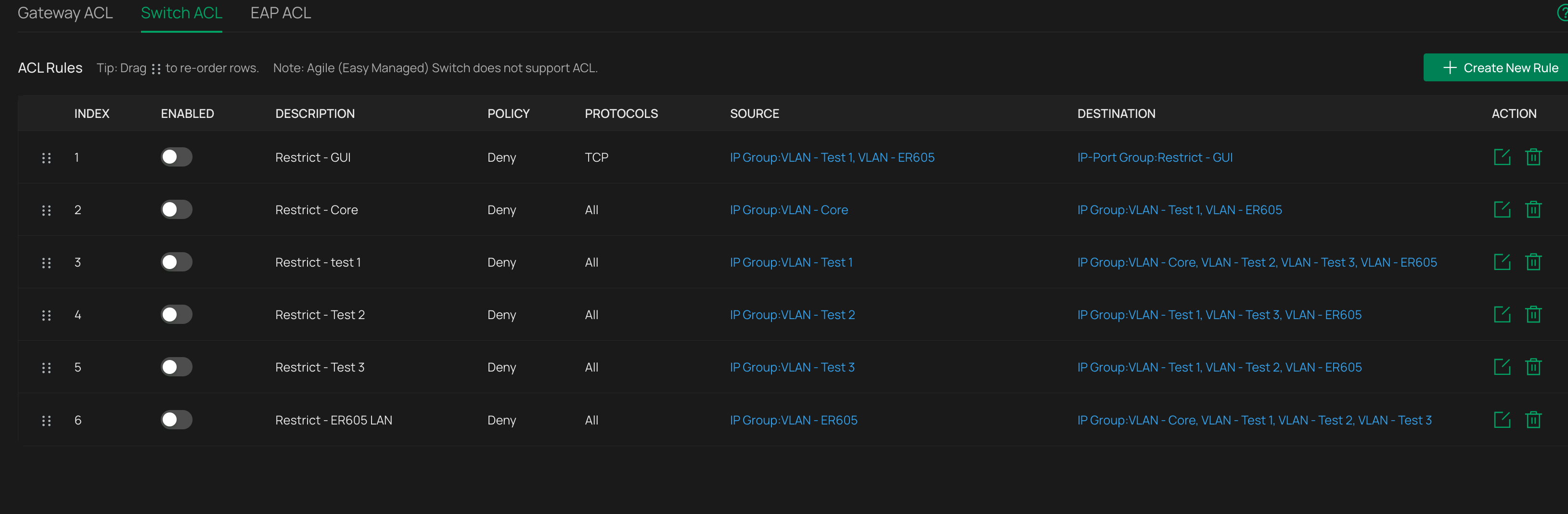
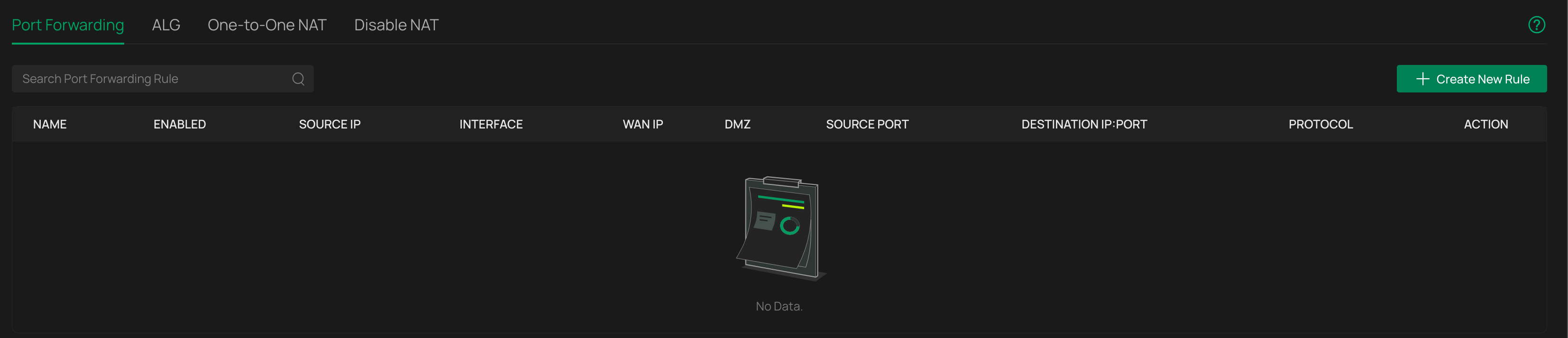
Disabling IDS/IPS – no change
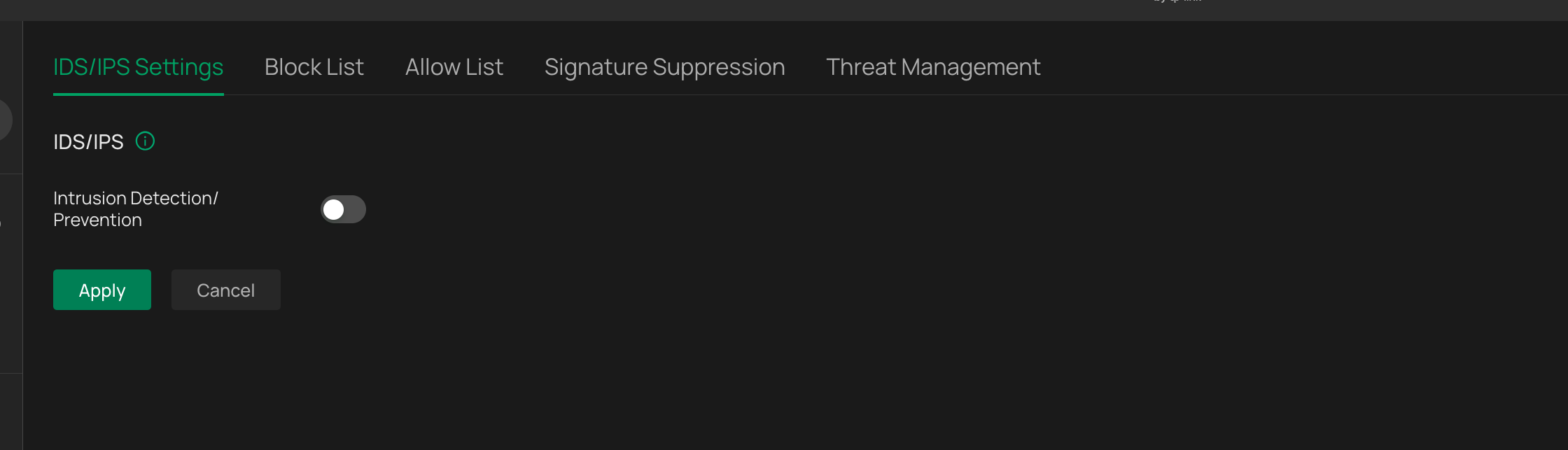
Disabling All ER8411 VPNs – no change
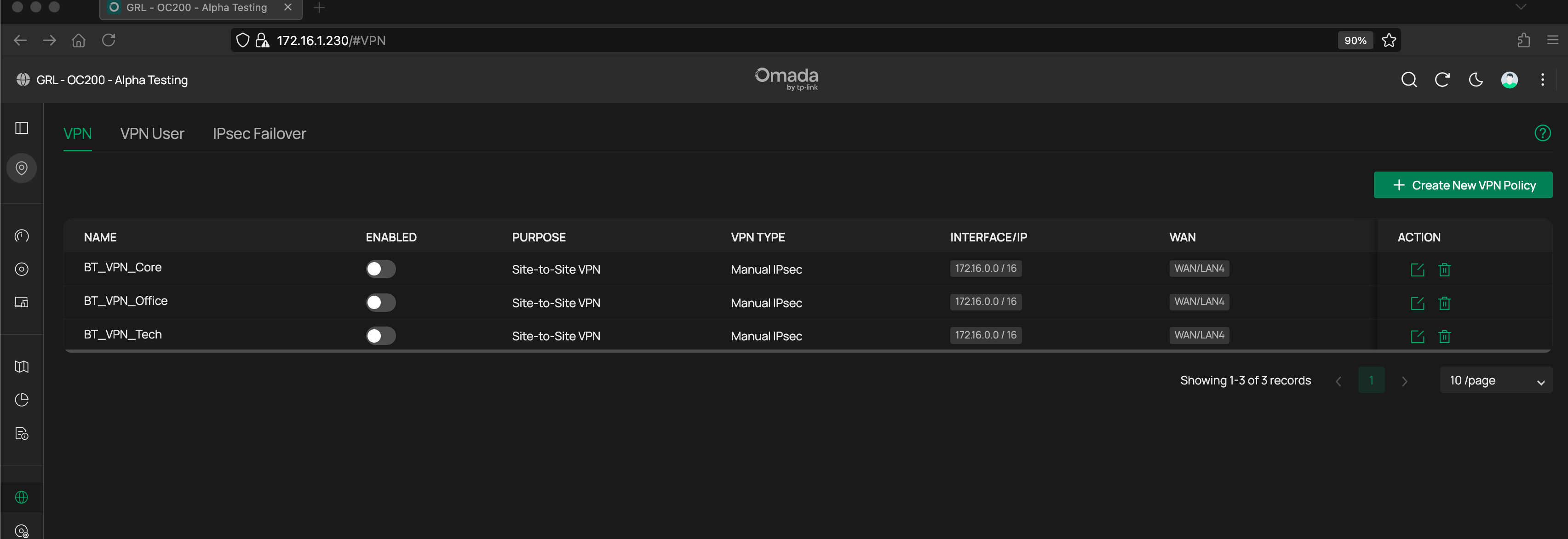
I have attached a wireshark capturing VPN connection and then attempting to load web GUIs of devices over the VPN
Results replicated on ER605v2 FW 2.3.1 as well in an identical scenario
-ST
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
I have finished my testing, rebuilding everything from scratch, and made the discovery of what is breaking VPNs, on my system at least
Things i did, in sequence
Factory reset Gateway, Switch, EAP pin-hole method
Forgot devices and deleted site on controller
Created new, unedited site on controller, set gateway as ER8411 only - no other changes
Adopted Factory reset Gateway
Adopted Factory reset switch
Adopted Factory reset EAP
Set Default LAN to 172.16.1.X Gateway 254, Switch 253, EAP 252
Set Default LAN DHCP gateway to switch SVI for Switch Routing
Set Gateway Static Route hopping traffic to Switch SVI
Enabled IDS/IPS Full
Enabled DNS Proxy and DNS Cache
Enabled DPI with logging
Disabled IGMP Proxy
Added my usual Site-to-site IPsec VPN to office
Enabled Second 1gig WAN port (WAN/LAN5) with gateway auto-reboot when enabled
Connect WAN5 to another network with DHCP
Enable policy routing to force all internet traffic over WAN4
Add a second Network, and enable Switch Interface for it, add it to gateway static route hopping traffic to switch
Enabled flow control on ER8411 WAN ports and SFP+ WAN/LAN 2 to switch
Set up switch ports profiles / spanning tree and apply to switch ports
Add reboot schedule for gateway and switch
Add a third network - switch only, set up switch interface and DHCP, add to gateway static route hopping traffic to switch
Configured custom gateway Echo Server and “Remember this Device”
Configured Site settings - DST, Mesh and Fast Roaming disable, Airtime Fairness
-----VPNs still working at this point-----
Now, i wanted to re-verify what my maximum MTU size was over my ISP at home (5G) - result - packet size of 1324 does not fragment
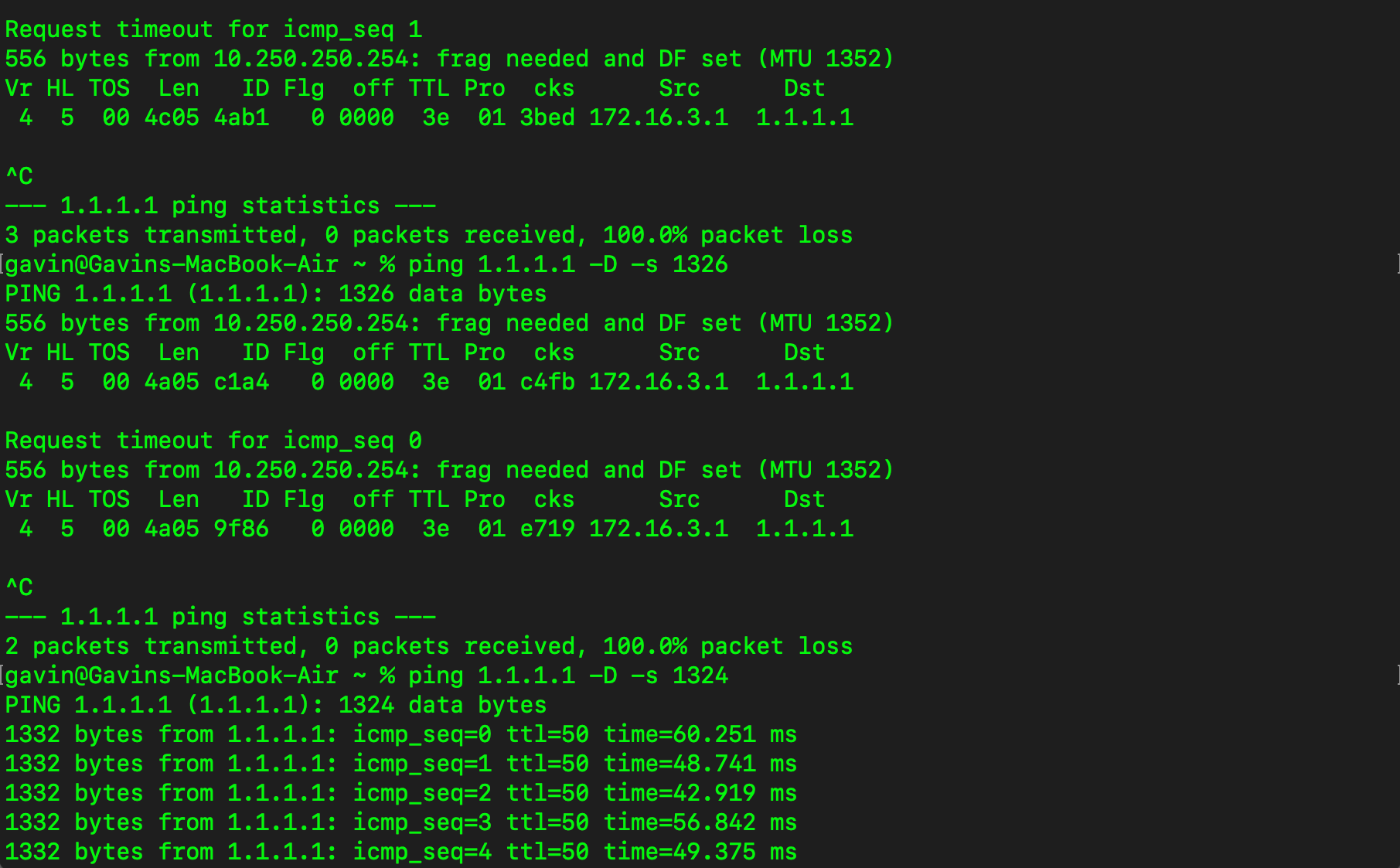
Setting MTU to 1352 (1324+header bytes) - VPNs Broken - BINGO
Setting MTU to 1378 - VPNs working
Setting MTU to 1500 - VPNs Working
Anything less than 1378 - Not Working
- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
Nope, no difference
I have also confirmed the other posters thread that L2TP isnt passing through either
- Copy Link
- Report Inappropriate Content
yes I saw that post, I've tested a bit here, I have an L2TP/IPsec client on a Windows 11 pc that connects to a Mikrotik router, it connects just fine and everything works as it should from LAN on ER8411 and ER605, It is a full VPN so all traffic goes through the L2TP server.
no difference if I disable ipsec ALG works anyway, I can't test against ipsec server from the windows pc so I don't know if it would work.
- Copy Link
- Report Inappropriate Content
I have also tried:
Disable DPI
Disable ALGs
Disable DNS Cache
Disable DNS Proxy
Disable all firewall attack defense settings
I have a bunch of colleagues who cannot usilise our second site client-to-site L2TP or IPSec VPNs now (hosted on a Draytek router), they are all on standalone ER605 v2s on 2.3.1 as well which havent had any other changes
- Copy Link
- Report Inappropriate Content
strange stuff, I'm going to set up an L2TP server on an ER605 that is remote to test a little more. I'll give you feedback :-)
- Copy Link
- Report Inappropriate Content
ok, this was even weirder, I set up L2TP/Ipsec on an ER605v2, my pc connects fine to this router when I'm behind an ER707-M2 or ER706W. , but when I'm behind an ER8411 or ER605v2 it doesn't work. but L2TP to the Mikrotik router works from all Omada routers.
- Copy Link
- Report Inappropriate Content
Yep, weird, but thanks for confirming the issue
All my omada gateway and 1 draytek gateway hosted client-to-site VPNs dont work behind the ER8411 or ER605 v2
I set up a test vpn on a friends gateway (asus home router) and that works fine
Also, my mobile banking app - which i think sets up a secure tunnel - doesnt work now, i have to go on 4/5G on my phone for it to work now
- Copy Link
- Report Inappropriate Content
yes it seems like something is wrong, I tested my bank app on my phone and it worked for me :-) ok, then we'll have to wait for feedback from the Omada team..
- Copy Link
- Report Inappropriate Content
I have finished my testing, rebuilding everything from scratch, and made the discovery of what is breaking VPNs, on my system at least
Things i did, in sequence
Factory reset Gateway, Switch, EAP pin-hole method
Forgot devices and deleted site on controller
Created new, unedited site on controller, set gateway as ER8411 only - no other changes
Adopted Factory reset Gateway
Adopted Factory reset switch
Adopted Factory reset EAP
Set Default LAN to 172.16.1.X Gateway 254, Switch 253, EAP 252
Set Default LAN DHCP gateway to switch SVI for Switch Routing
Set Gateway Static Route hopping traffic to Switch SVI
Enabled IDS/IPS Full
Enabled DNS Proxy and DNS Cache
Enabled DPI with logging
Disabled IGMP Proxy
Added my usual Site-to-site IPsec VPN to office
Enabled Second 1gig WAN port (WAN/LAN5) with gateway auto-reboot when enabled
Connect WAN5 to another network with DHCP
Enable policy routing to force all internet traffic over WAN4
Add a second Network, and enable Switch Interface for it, add it to gateway static route hopping traffic to switch
Enabled flow control on ER8411 WAN ports and SFP+ WAN/LAN 2 to switch
Set up switch ports profiles / spanning tree and apply to switch ports
Add reboot schedule for gateway and switch
Add a third network - switch only, set up switch interface and DHCP, add to gateway static route hopping traffic to switch
Configured custom gateway Echo Server and “Remember this Device”
Configured Site settings - DST, Mesh and Fast Roaming disable, Airtime Fairness
-----VPNs still working at this point-----
Now, i wanted to re-verify what my maximum MTU size was over my ISP at home (5G) - result - packet size of 1324 does not fragment

Setting MTU to 1352 (1324+header bytes) - VPNs Broken - BINGO
Setting MTU to 1378 - VPNs working
Setting MTU to 1500 - VPNs Working
Anything less than 1378 - Not Working
- Copy Link
- Report Inappropriate Content
thanks you for investigating the problem and forwarding us a solution!
But, where did you get 1.3.6 for er8411? I only see 1.3.5 as latest RC
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 1747
Replies: 30
Voters 0
No one has voted for it yet.
