How to configure ACL to prevent inter VLAN communication
We're trying to block inter VLAN (across VLAN) communication.
We'd like to have VLAN 10 for one department and VLAN 20 for other department whereas they should not be able to communicate with each other.
We have the VLANs configured.
There's a DHCP server configured on the switch and a VLAN interface for each VLAN.
Users receive a proper IP.
ACL configuration does not seem to work across VLAN . In any configuration, the VLANs can talk to each other.
We have tried port binding, VLAN binding, IP ACL, VLAN ACL, etc.
We seem to be only able to block communication within each VLAN but not across VLANs.
Here's the config we'd like to get:
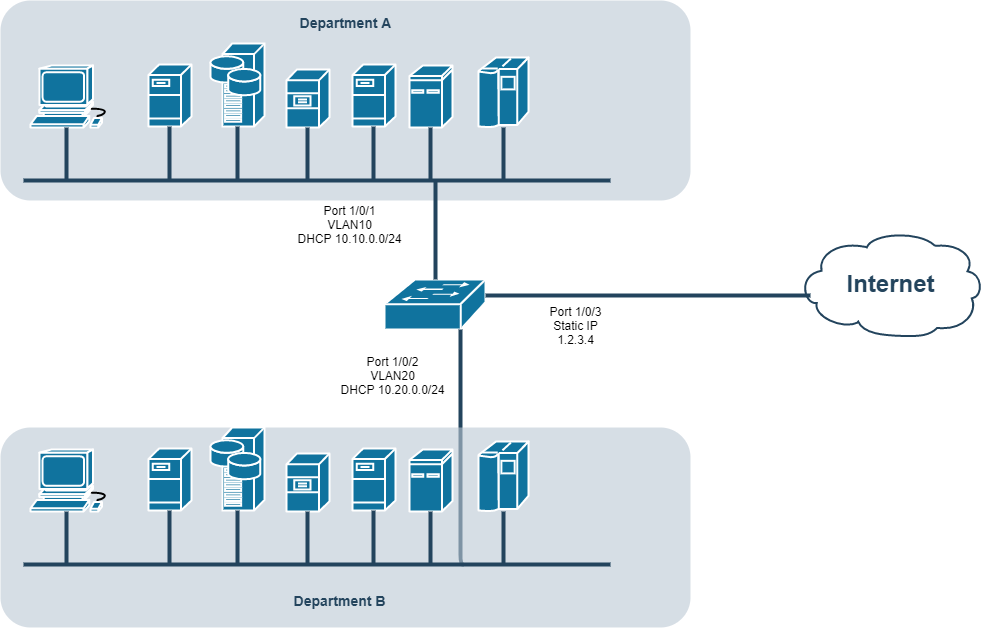
Requirements:
1. Department A and B can access internet
2. Department A can communicate within Department A
3. Department B can communicate within Department B
4. Departments A and B cannot communicate with each other
This seems to be a common use case - what's the proper way to configure blocking of communication across VLANs?
An interface per VLAN seems to be required - are we maybe missing anything?
