ER605 v2 - OpenVPN - No access to network resources after firmware update to 2.3.0
ER605 v2 - OpenVPN - No access to network resources after firmware update to 2.3.0
Hello,
I applied the latest update 2.3.0 Build 20250428 Rel.18967 as soon as it was released. After the update, my OpenVPN connects just like before, but I have absolutely no access to any network resources (SMB, VNC... nothing). I generated a new OpenVPN configuration file, but that didn’t help either. I also tested the following solution:
https://community.tp-link.com/en/business/forum/topic/653224
I kindly ask for your help in resolving this issue — I have already tried everything that came to mind, including creating new ACL rules and disabling Attack Defense...
Before the update, everything was working perfectly.
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
The issue has been clarified. Access to network resources via OpenVPN is being blocked by rule 6, which blocks all ports from WAN to LAN. I've always had this rule, and it wasn’t a problem with the previous firmware. I created a test rule allowing WAN > LAN on the OpenVPN port, but unfortunately, that doesn't help. I have no idea how to solve the problem while keeping my ALL rule.
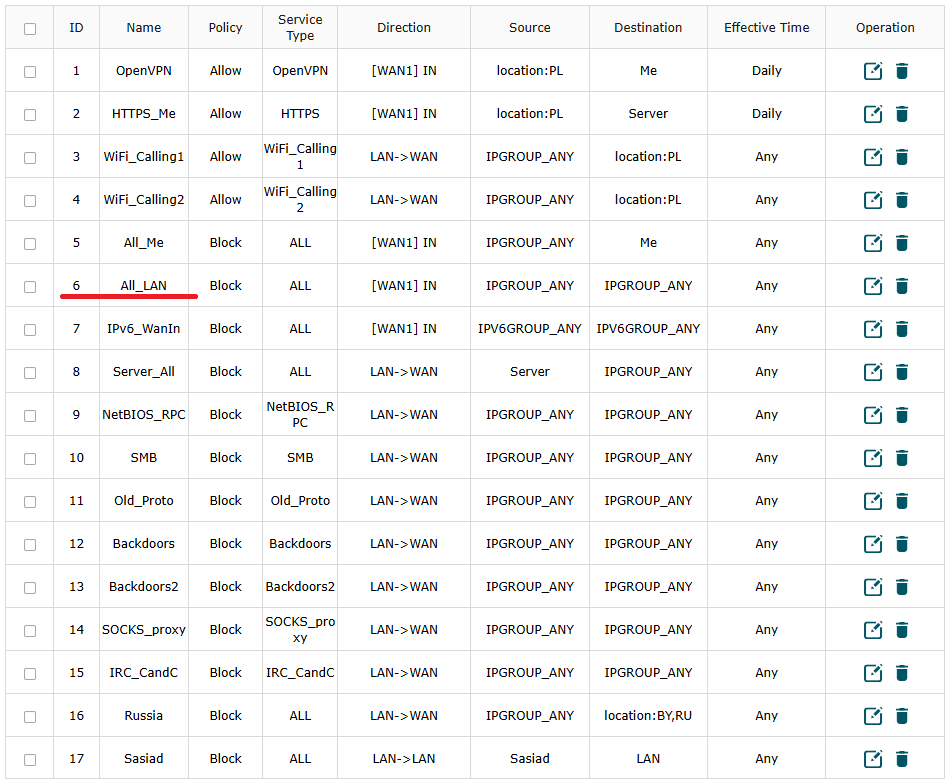
- Copy Link
- Report Inappropriate Content
I see you have some ACL rules, I'm almost 100% sure that's what the problem is. You've blocked some from lan/wan, it's possible that it's blocking responding back to OpenVPN. So my suggestion is to disable all ACL rules, or create some new ACL rules that you put at the very top of your ACL list that allow all traffic from OpenVPN in and out
two new rules one WAN/In and one LAN/WAN that allows all traffic both ways in the OpenVPN IP Pool
- Copy Link
- Report Inappropriate Content
I managed to solve it!
First, I created an IP Group named OpenVPN_LAN with an address pool matching my OpenVPN subnet. Then, I added a rule allowing WAN IN ➜ LAN traffic for the OpenVPN_LAN group.
It works perfectly now, but I’m wondering if this rule might have slightly weakened my network’s security.
To me, it now seems like there was a mistake before — because OpenVPN was working even though there was a rule blocking all WAN to LAN traffic.
What do you think about this?
IP Group:

ACL:

- Copy Link
- Report Inappropriate Content
Good thing you got it working then :-) I don't really have any idea why it worked before, I'm not that familiar with how to configure in stand alone, but as I mentioned earlier, ACL can really trick you so that's why I disable ACL if I get into a situation where things don't work. I've spent hours troubleshooting and it turns out that ACL is messing it up :-)
- Copy Link
- Report Inappropriate Content
A basic test for VPN is to ping the gateway. If the gateway is pingable, that means the tunnel is effective. Just FYI.
There are no other reports about the OVPN issue like this.
ACL can be super tricky when you have so many rules there already. It would spend hours or days to fine tune them.
I do not receive messages unless I find it necessary for privacy when it comes to public IP and MAC address. Otherwise, any case will be openly discussed.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 3077
Replies: 17
Voters 0
No one has voted for it yet.
