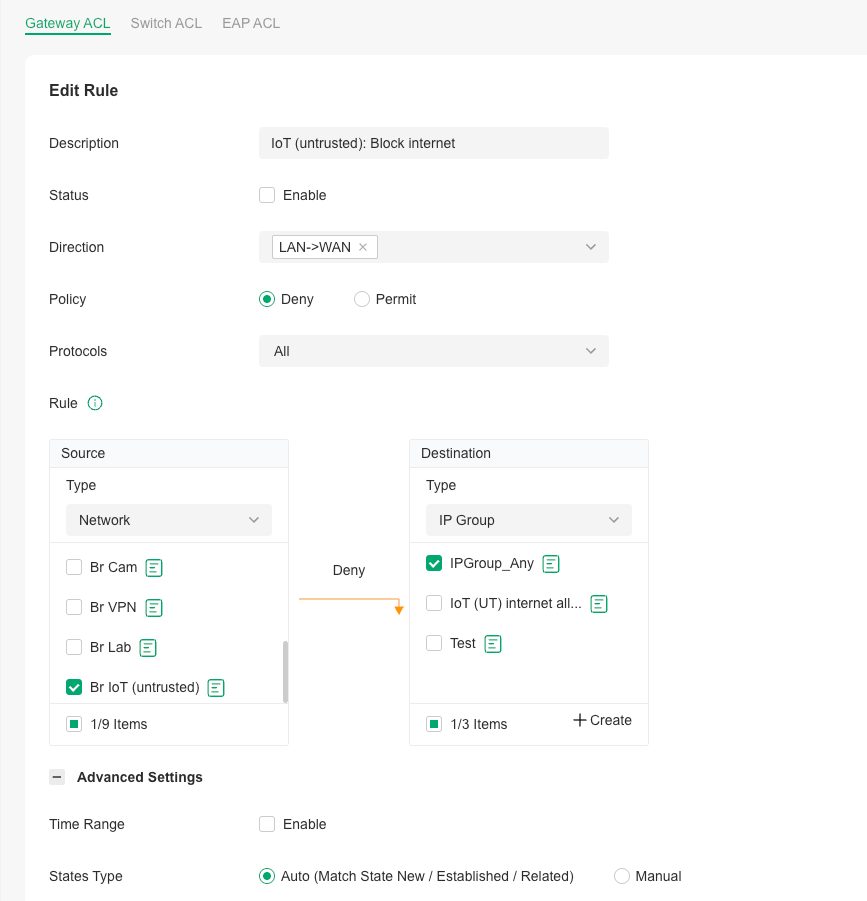
Gateway ACL rule block internet for all VLANs instead of only for VLAN IoT
Dear community,
I thought it would be something simple to set up very basic gateway ACL rules, however I cannot make it work although I followed various guides.
Here is my setup:
- Router ER7206 connected to internet modem
- Switch SG2210P (1) connected to router ER7206, profile is set to “All”
- Two further switches SG2210P (2) and SG2218P (3) connected to switch SG2210P (1), profiles are set to “All”
- AP EAP650 connected to switch 3, profiles are set to “All”
- AP EAP683 connected to switch 1, profiles are set to “All”
I have three LANs:
- Management VLAN 31, all LAN interfaces
- Main VLAN 42, LAN interface WAN/LAN1
- IoT VLAN 73, LAN interface WAN/LAN1; for this one I also have created a corresponding Wifi
Profiles on the switches are either set to “All” (in case of uplink port or AP port, or to the specific VLAN). Example: If an IoT device is connected via wire, the switch port would show profile “IoT”.
Here is my very simple requirement:
- Let IoT VLAN not talk to the internet
- Let IoT VLAN not reach the other VLANs, but let the other VLANs reach the IoT VLAN
What I did as a starter: Create an ACL gateway rule LAN->WAN, Deny, All protocols, source network IoT, destination IP Group:IPGroup_Any. When activating this rule, however internet access is blocked for ALL VLANs and all clients in the VLANs – and this is what I do not understand.
Is there anything completely wrong with my configuration? What am I missing?
Thanks for any input!