Detailed Technical Analysis (For Engineers/Power Users)
Wireshark Packet Analysis
Target: ls-prod-account-saves.s3.amazonaws.com (Amazon S3, port 443)
File: 15.2MB BG3 cloud save
Session: 17.65 seconds before timeout
Transferred: 328KB (2.1% completion)
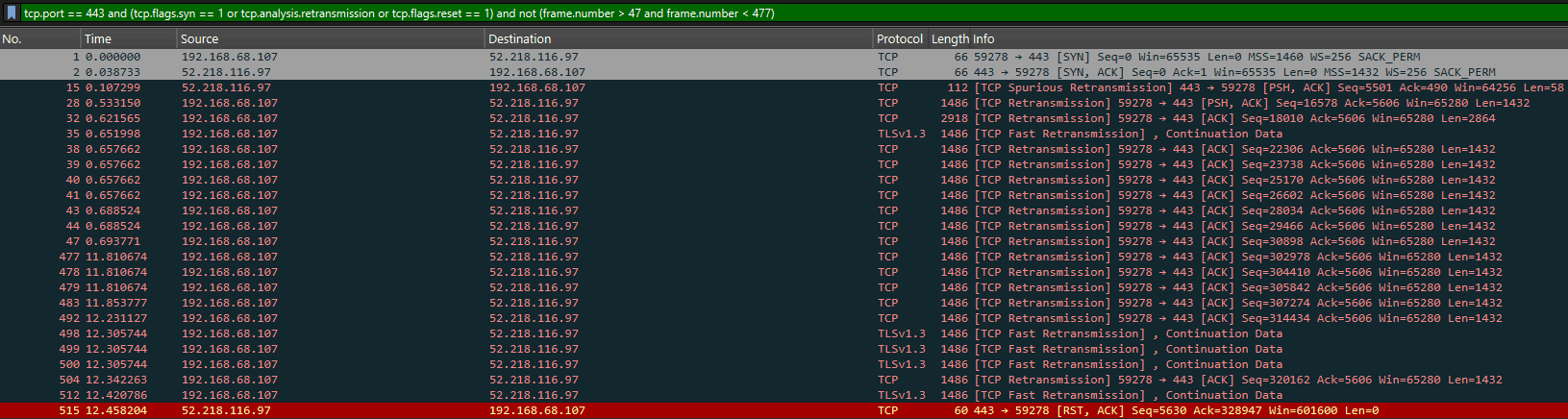
Key Timeline:
- Packets 1-2 (0.00s): TCP handshake successful
- Packet 15 (0.11s): First spurious retransmission from server
- Packet 28 (0.53s): First client retransmission - problem begins
- Packets 32-47 (0.6s): Retransmission flood starts
- Packets 477-512 (11.8s): Continuous retransmissions
- Packet 515 (12.46s): Server sends RST, connection dead
Performance Matrix
| Connection Method |
Speed |
Success |
Notes |
| XE75 Pro Direct |
<1 Mbps |
0% |
TCP retransmission cascade |
| XE75 Pro + VPN |
5.8 Mbps |
100% |
Same hardware, traffic obfuscated |
| Smartphone Hotspot |
6.5 Mbps |
100% |
Bypassing XE75 Pro entirely |
| Old Router |
6.2 Mbps |
100% |
Same ISP, different router |
| XE75 Pro + Other Services |
6+ Mbps |
100% |
Google Drive, Dropbox work fine |
Comprehensive Testing Performed
Firmware & Hardware:
- Factory reset (multiple times)
- Firmware 1.2.14 and 1.2.10 tested
- 3-pack XE75 Pro, tested single unit mode
Network Configuration Testing:
- QoS: Disabled
- Mesh: Completely disabled (single unit)
- Fast Roaming: Disabled
- Beamforming: Disabled
- SIP ALG: Disabled
- UPnP: Disabled + manual port forwarding
- IPv6: Disabled
- DNS: Set to 8.8.8.8 (bypassing local Pi-hole)
- Access Point mode: Same failure
- Wired vs WiFi: Both fail identically
- Guest network: Same failure
- Static IP assignment: No change
- MTU: Reduced to 1410, no improvement
Network Isolation:
- Bypassed personal server entirely
- Minimal setup: PC → XE75 Pro → ISP only
- Multiple devices tested
- DNS/basic connectivity: All normal
- TLS handshake: Completes successfully
- Failure: Only during sustained upload transfer
ISP Elimination:
- Same fiber ISP, different results based purely on router
- Other users on same ISP: No problems
- Original ISP router: Works perfectly (both bridge/router modes)
- Direct ONT connection requested for testing
Critical Evidence Points
-
Traffic Pattern Recognition: Retransmissions start within 200ms, suggesting immediate classification and throttling of gaming traffic patterns
-
Hardware Capability Proven: VPN success through same router proves hardware can handle bandwidth and latency requirements
-
Service-Specific Targeting: Router allows identical file sizes to other cloud services but blocks gaming uploads specifically
-
Zero Diagnostic Correlation: Router logs completely silent during failure windows (cross-referenced with Wireshark timestamps)
-
Consistent Cross-Device Failure: Problem persists across different devices, confirming router-level issue
Router Log Analysis
HomeShield provides minimal diagnostics beyond basic parental controls. Standard router logs show zero correlation with TCP failure events. Even informational logs are silent during exact failure windows when cross-referenced with packet capture timestamps.
TCP Stack Behavior Analysis
The router's TCP implementation appears to:
- Successfully complete handshakes
- Allow initial small data transfers
- Identify gaming traffic patterns during sustained upload
- Apply throttling/interference causing retransmission cascades
- Eventually trigger server-side connection reset (RST)
VPN obfuscation prevents this pattern recognition, allowing normal TCP behavior.
Conclusion
This is a firmware-level defect in traffic classification logic, not a configuration issue. The router incorrectly identifies gaming upload patterns as problematic and applies throttling at the hardware level. Engineering fix or hardware replacement required.
Additional testing suggestions welcome - happy to provide more diagnostic data if helpful.

