IKEv2 IpSec Site2Site with multiple Remote Subnets not working
Hi there,
I have setup a S2S to my LANCOM Gateway at Work. My Main Subnet ist working. I have added another Remotesubnet on my Controller for that tunnel. As i can see unter Insights->VPN Status, there is no other route added for the second Subnet. Communication through the Tunnel with the first is working properly but the second remote Subnet is still not reachable.
Anyone having the same issue or got some advise?
Greetings
Felix
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
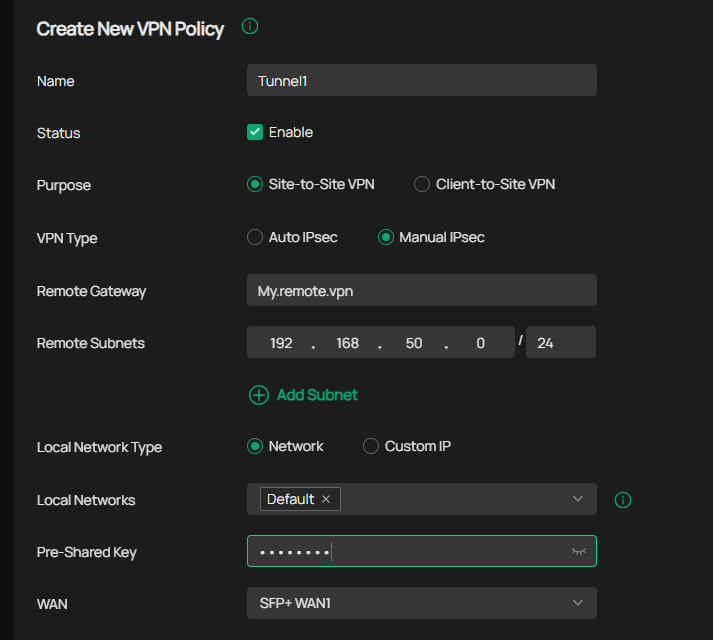
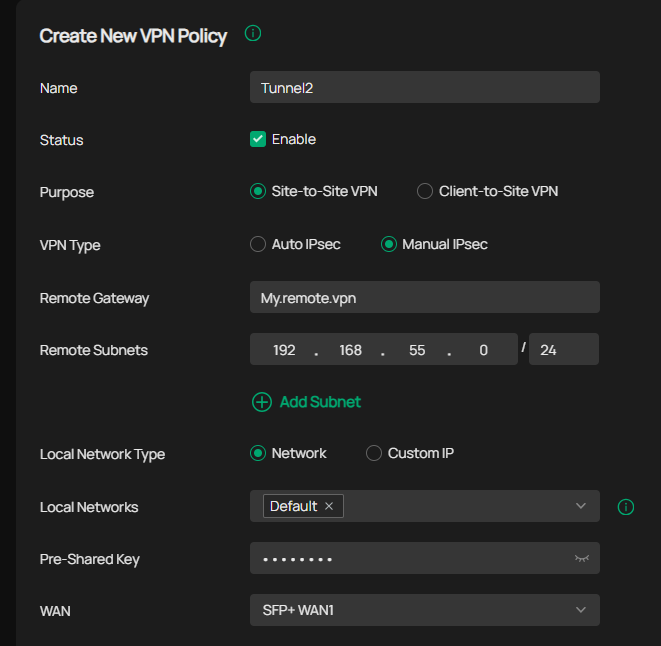
I have the same problem with Cisco firewalls, you have to create a tunnel for each network you are going to have in the VPN tunnel. So you have to create a new tunnel where everything is the same except for the remote network.
Like this
- Copy Link
- Report Inappropriate Content
I am not sure what you mean. If you can provide details, it would be better.
If the remote subnet is not accessible, you can consider pinging the remote gateway to verify if it is a problem with the VPN tunnel or your client.
You can refer to this:
- Copy Link
- Report Inappropriate Content
Thank you for your reply!
I'll attach some Screenshots to be more specific.
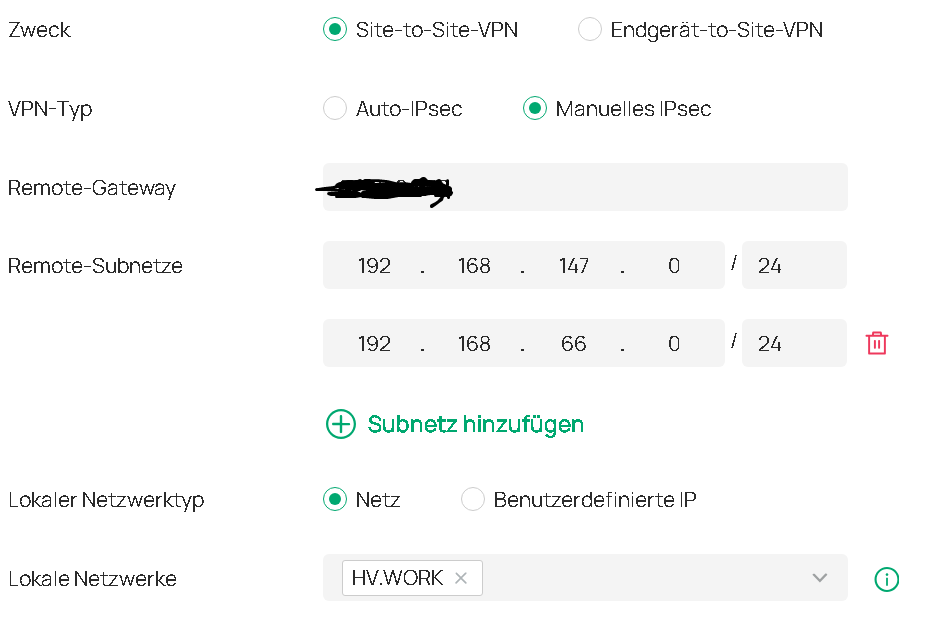 S2S Setup with two Remote Subnets
S2S Setup with two Remote Subnets
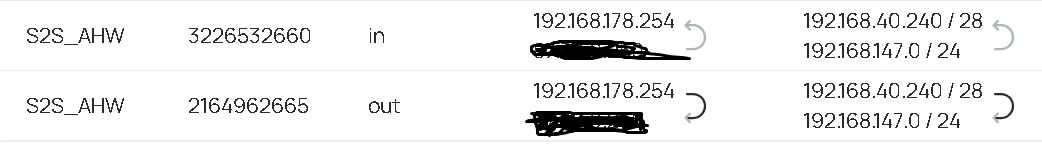 Insight Status is only showing the first Remote Subnet routed
Insight Status is only showing the first Remote Subnet routed
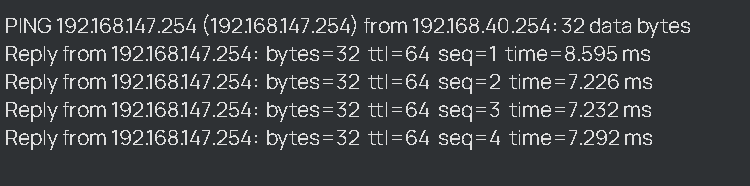 First Subnet ist Reachable via Ping from my ER605
First Subnet ist Reachable via Ping from my ER605
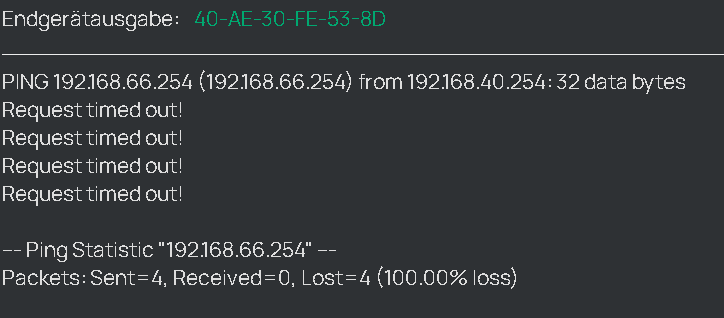 Second Subnet not Reachable
Second Subnet not Reachable
For testing purpose my Remote Side (Lancom Gateway) is accepting all adresses (0.0.0.0/0)
My local Network is 192.168.40.254 / 28
My ProviderGateway is 192.168.178.254
Remote Networks are 192.168.147.0/24 & 192.168.66.0/24
Hope this makes it more clear :)
- Copy Link
- Report Inappropriate Content
I have the same problem with Cisco firewalls, you have to create a tunnel for each network you are going to have in the VPN tunnel. So you have to create a new tunnel where everything is the same except for the remote network.
Like this


- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
YES I agree, I don't really know why that is like this, I see that on Unifi I can choose between router based and policy based VPN, Unifi against Unifi must use Router based, the same with Unifi against Omada, but Unifi against Cisco must use Policy Based, so it seems like there is a default on Omada which is Router Based VPN, I don't know :-)
![]()
- Copy Link
- Report Inappropriate Content
just curious, as i dont have a cisco to muck around with
On the cisco, do you have to add subnets to the VPN as a interface/vlan (like Omada "Networks") or can you add them by IP, and can you not supernet them into a larger IP range per single tunnel ?
- Copy Link
- Report Inappropriate Content
you don't add interface but ip or network objects , yes you can add supernet, groups with ip. there is a lot more choice than on Omada, but it is also more complicated. you can nat vpn tunnels all the way. so if you have the same ip net on two sites you can use nat in vpn to solve that problem. but i like working with different ip net on different sites. it makes things much easier :-)
but with Cisco you can create as many ip groups or port groups as you want, I've never been told that I can't create more groups because now you've used up the 16 you have available. so those aren't the problems I struggle with on Omada
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 442
Replies: 7
Voters 0
No one has voted for it yet.
