WAN access stops working once I connect via WireGuard
WAN access stops working once I connect via WireGuard
Hello Everyone,
I have an issue with Wireguard. It's similar case (or at least seems so) as in this topic: https://community.tp-link.com/en/business/forum/topic/610050
however I do not know what's the actual solution and if the OP actually had the same exact problem as I did.
The idea is that I want any and all traffic to pass through the VPN, as if I've been connecting from (say) home.
Once I connect, I have no trouble reaching local hardware. But when I try to browse the net, it doesn't work at all.
Moreover - if I connect to a jumphost (be it Windows or Linux based, doesn't matter), the jumphost itself has now trouble reaching the outside world.
I can't open any network site, ping times out, and if I try to use my local DNS, even the name resolution fails, as the DNS itself can't reach outside world (I don't have and don't want to cache entries for hours or days, that's not the point here and it still won't fix anything besides the name resolution).
I thought that when I set the allowed IPs to 0.0.0.0/0, then everything will work as planned but it clearly doesn't.
It is as if the whole traffic is being routed back to WG subnet instead of going where it's supposed to (WAN in that case), but that's just a wild guess.
Can anyone help me out? Am I doing something wrong or it's like that by design (and if so, why?).
ps. congratulations on the regexp words filtering - if one sentence in post ends in " T " and the next begins with " IT'S " it's interpreted as female feeding organs. Flabbergasting.
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
Based on the configuration you provided, we noticed that you have set 0.0.0.0/0 as the AllowedIPs on both the WireGuard server and the client. This setup prevents the client from accessing the Internet through the tunnel.
Please configure 0.0.0.0/0 only on the client, and on the server set the peer’s AllowedIPs to the client’s WireGuard interface IP (see the attached example). After this change, the client will be able to browse the Internet through the VPN.
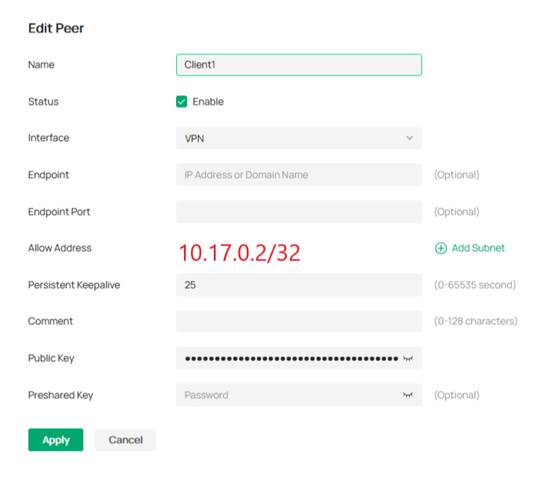
- Copy Link
- Report Inappropriate Content
Thank you for your post.
Could you please share screenshots of your current WireGuard VPN configuration on the gateway and of the VPN-client settings? While configuring, make sure the IP range you assign does not overlap or conflict with the subnet already used on your LAN.
When you say that local hardware remains reachable after the VPN connects, do you mean the VPN client can successfully ping devices on the gateway’s LAN, and only Internet access is failing?
- Copy Link
- Report Inappropriate Content
Here you go:
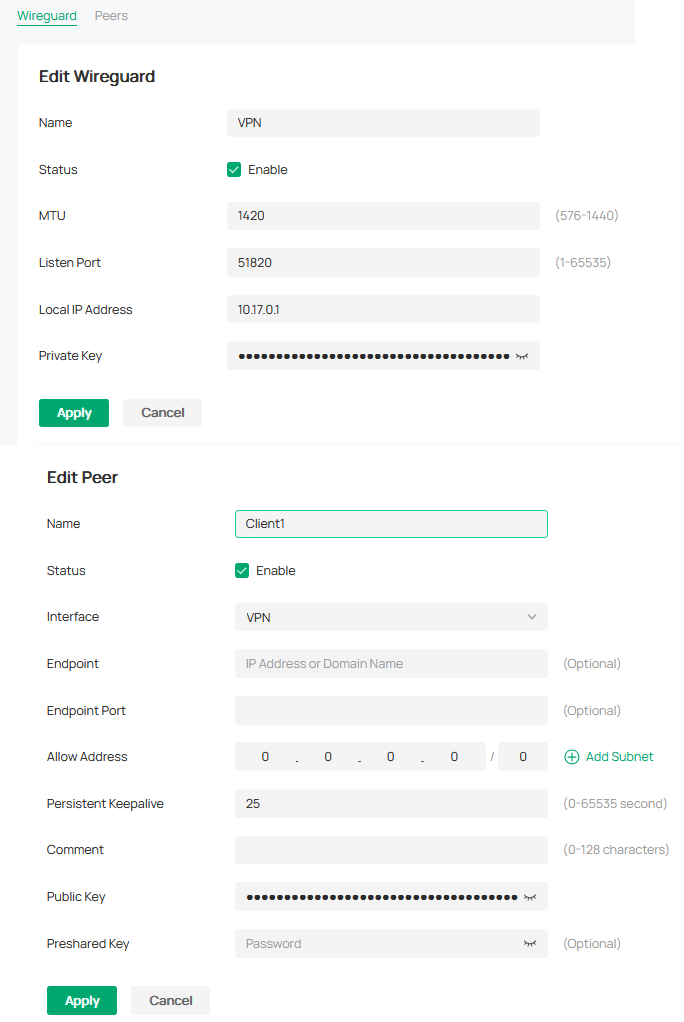
As for the question - correct. Once connected, local devices can be pinged, RDP'd or SSH'd to. Can't say the same about the WAN.
Also, if I connect (say SSH) into a server that's reachable and try to reach WAN that way, it also doesn't work.
- Copy Link
- Report Inappropriate Content
What about your VPN-client settings—how did you configure them?
Also, what does the LAN-side setup look like on your local devices?
- Copy Link
- Report Inappropriate Content
Here's a screencap from phone's WG app.
Going from the top:
Name / Pubkey / Address / DNS servers / MTU
//
Pubkey / Allowed IPs / Endpoint / Connection keepalive
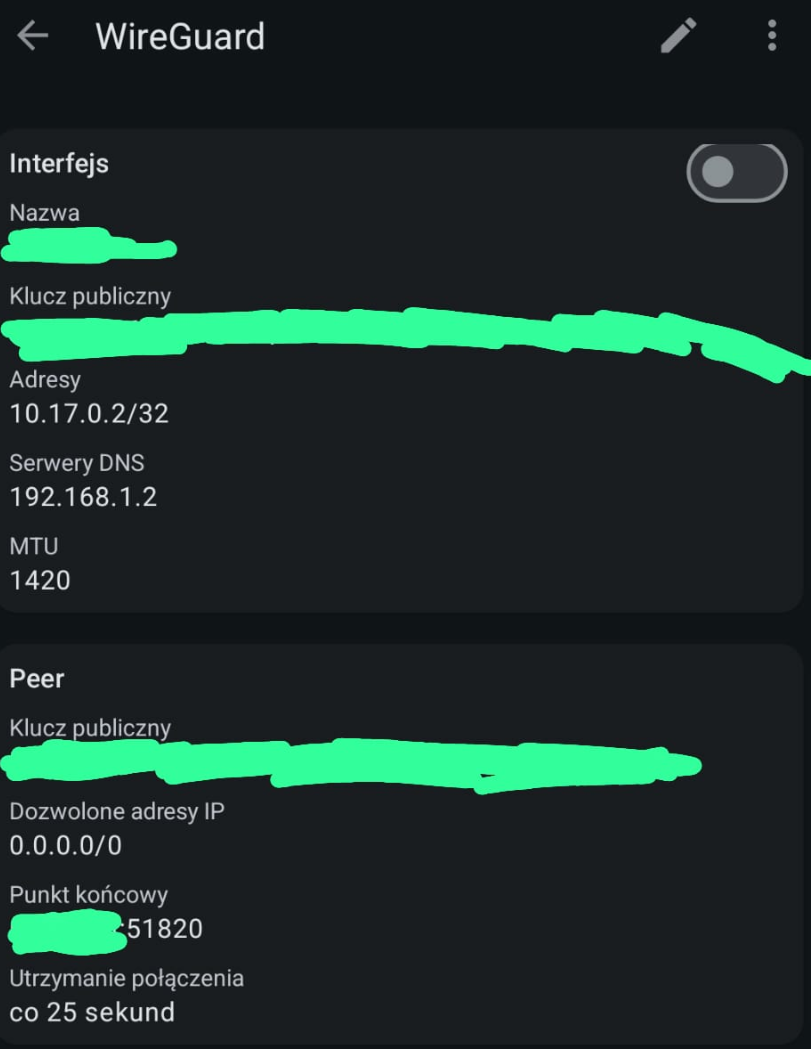
As for the LAN devices, I'm not sure what kind of information would you like to get. Overall most things are present in 192.168.1.0/24 subnet, have 24 mask set, use default gateway & two local DNS servers. Nothing fancy. Unless this is about something else, then please clarify, so I may provide the information you need.
- Copy Link
- Report Inappropriate Content
You can change the DNS settings in the client configuration so that it no longer sits in the same subnet as the server-side LAN.
It’s also recommended to assign the client IP range to a subnet different from the server’s virtual-IP pool.
Feel free to test with various client devices to see whether the VPN can connect successfully.
- Copy Link
- Report Inappropriate Content
I'm afraid that the DNS settings don't really matter. Whether I set the local DNS server, some widely available one, like 8.8.8.8 or anything similar or just leave the entry empty, it doesn't work. It's not a DNS problem in itself, as I can query different servers about a particular domain (e.g.: nslookup somedomain[dot]com 8.8.8.8). It's that the ping doesn't work and, as a whole, if I try to open a website in browser, I get timeout - both locally and on the jumphosts. And if I try to connect to some site via IP, I don't get the usual "cert problem" (because I've used IP instead of domain name) - I get a timeout. Once I drop out from the VPN, everything goes back to normal.
The subnet that the WG is assigned to has nothing to do with the subnet pools that I use on my network.
I've tested that on both an Android-based device as well as a laptop (Windows-based). Same result.
- Copy Link
- Report Inappropriate Content
Thank you so much for taking the time to post the issue on the TP-Link community!
To better assist you, I've created a support ticket via your registered email address and escalated it to our support engineer to look into the issue. The ticket ID is TKID251062761 please check your email box and ensure the support email is well received. Thanks!
Once the issue is addressed or resolved, welcome to update this topic thread with your solution to help others who may encounter the same issue as you did.
Many thanks for your great cooperation and patience!
- Copy Link
- Report Inappropriate Content
Based on the configuration you provided, we noticed that you have set 0.0.0.0/0 as the AllowedIPs on both the WireGuard server and the client. This setup prevents the client from accessing the Internet through the tunnel.
Please configure 0.0.0.0/0 only on the client, and on the server set the peer’s AllowedIPs to the client’s WireGuard interface IP (see the attached example). After this change, the client will be able to browse the Internet through the VPN.

- Copy Link
- Report Inappropriate Content
Indeed, I can confirm that setting it up that way makes things work. Thank you for your help.
Now, thing is, I'd like to understand *why* it has to be configured that way?
If I put 0.0.0.0/0 then I can reach everything on the LAN but no WAN.
If I put only the client IP (here: 10.17.0.2), I can reach both LAN and WAN.
So what does that option actually do, I wonder? If nothing would work with the first pool and then everything would with just the IP, I'd guess there's some reverse logic applied, but that's clearly not the case here. The configuration on the client seems to be irrelevant (or at least should be, somewhat), because having some kind of limited access to e.g. LAN should not be circumvented if I set up 0.0.0.0/0 on the client.
What if:
A) I wanted to set up it that way, so a client could use just WAN that way but have no way of reaching the devices on the LAN?
B) I needed to give access to WAN and 2 subnets (say: 10.0.45.0/24 & 192.168.72.0/24)?
C) I had to set up a specific range of external IPs (connect to a location and then be able to reach certain, known IPs from there but nothing else)?
D) I wished for the client to use the local DNS (e.g. 10.0.0.30) and have access to the WAN but nothing else?
And how does the client configuration (that's clearly not hardcoded and can be changed at any point in time) affect what I can actually get access to?
Does the option to "exclude private IPs" block LAN access? If so, shouldn't that be done server-side, so that client couldn't reach local devices if we don't want that to happen?
I'm showering you with questions here, but I'd really like to understand how this works.
- Copy Link
- Report Inappropriate Content
The meaning of this configuration item on the device side is:
when the destination IP of a packet passing through the device falls inside the specified range, the packet will be forwarded through the WireGuard tunnel—in other words, it will follow the WireGuard tunnel route.
-
When the device is set to 0.0.0.0/0, every destination IP (i.e., all traffic) is sent through the WG tunnel.
As soon as the WireGuard tunnel comes up, the device itself can no longer reach the Internet, because its own traffic is also forced into the tunnel. The same applies to WireGuard clients.
WG clients can still reach the LAN because the LAN route has a higher priority than the WG-tunnel route, so packets are directed to the LAN first. -
When the device is set to 10.17.0.2/32, only packets whose destination IP is exactly 10.17.0.2 are forwarded through the WG tunnel.
Consequently, both the device’s own Internet traffic and the WG client’s Internet traffic continue to use the WAN route, while LAN-bound traffic uses the LAN route as usual.
If you need to achieve requirements A and B, the current firmware cannot do it through WireGuard configuration alone; we will consider this use-case in a future release.
We’re not clear on the exact requirement for issue C.
For issue D, simply configure the desired DNS server on the client side
The meaning of this configuration item on the device side is:
when the destination IP of a packet passing through the device falls inside the specified range, the packet will be forwarded through the WireGuard tunnel—in other words, it will follow the WireGuard tunnel route.
-
When the device is set to 0.0.0.0/0, every destination IP (i.e., all traffic) is sent through the WG tunnel.
As soon as the WireGuard tunnel comes up, the device itself can no longer reach the Internet, because its own traffic is also forced into the tunnel. The same applies to WireGuard clients.
WG clients can still reach the LAN because the LAN route has a higher priority than the WG-tunnel route, so packets are directed to the LAN first. -
When the device is set to 10.17.0.2/32, only packets whose destination IP is exactly 10.17.0.2 are forwarded through the WG tunnel.
Consequently, both the device’s own Internet traffic and the WG client’s Internet traffic continue to use the WAN route, while LAN-bound traffic uses the LAN route as usual.
If you need to achieve requirements A and B, the current firmware cannot do it through WireGuard configuration alone; we will consider this use-case in a future release.
We’re not clear on the exact requirement for issue C.
For issue D, simply configure the desired DNS server on the client side
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 1046
Replies: 12
Voters 0
No one has voted for it yet.
