How to Setup Google Oauth portal Authentication in OC 200 Hardware Controller ?
Hey everyone,
I’m currently setting up an Google captive portal for my TP-Link Omada OC200 (v5.15.24.21) controller and ran into a problem configuring Google OAuth 2.0 for user authentication.
Here’s my setup:
-
Omada hardware controller (OC200) running locally
-
External portal server option enabled in Omada
-
My portal hosted locally (using local IP address)
-
Trying to integrate Google OAuth 2.0 login on the portal page
Issue:
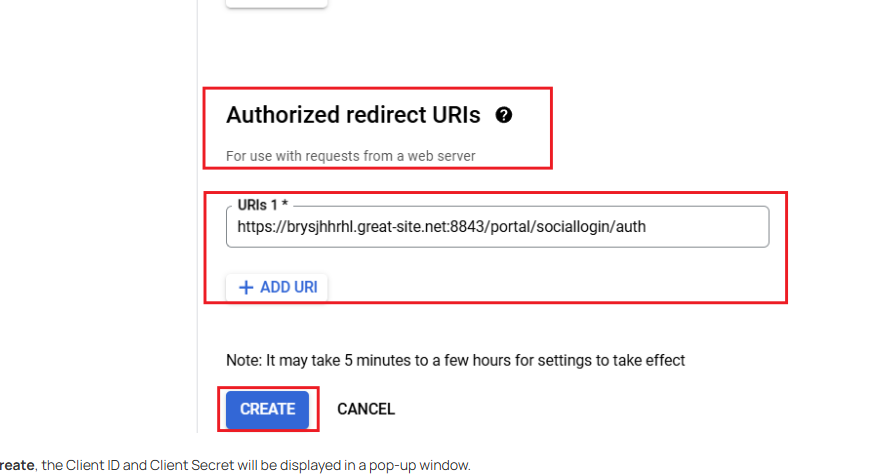
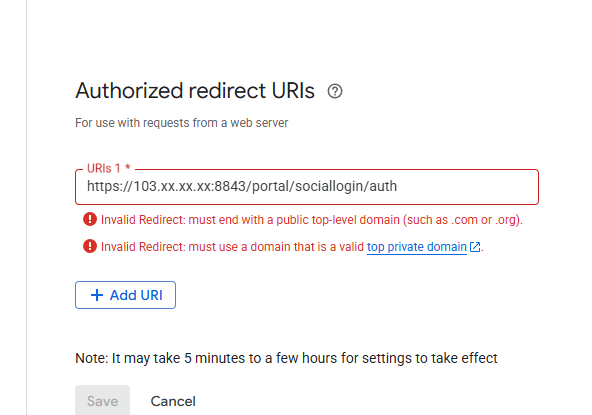
When configuring Google OAuth, it requires a callback/redirect URL. Since my Omada controller and portal are hosted locally (with a private IPv4 address), Google rejects the redirect URI because it’s not public (e.g., http://192.168.x.x/callback).
So I’m stuck:
-
If I use a local IP, Google refuses to authorize it.
-
If I use a public domain, Omada can’t route back locally without NAT setup or public hosting.
-
The Omada controller doesn’t expose a clear setting to define an external callback path or handle OAuth directly.
What I’m trying to achieve:
Let users connect to Wi-Fi, reach the captive portal, sign in using Google, and then get authenticated through Omada’s external portal integration — all without exposing my controller publicly.
Questions:
-
Is there any way to make Google OAuth 2.0 work with a locally hosted Omada external portal?
-
Do I need to set up a public domain with HTTPS (like via Cloudflare Tunnel or Ngrok) just for the OAuth redirect?
-
Has anyone successfully integrated Google OAuth 2.0 with Omada’s external portal flow (and if yes, how)?
Any suggestions or examples (especially redirect handling and callback integration with Omada’s API) would be really helpful.