ACL Rules with OpenVPN
Hi,
I am hoping someone may provide some insight to what appears to be some strange behavior with ACL rules on ER7414-M2 v1.2 (fw 1.1.0). The following rules are defined -
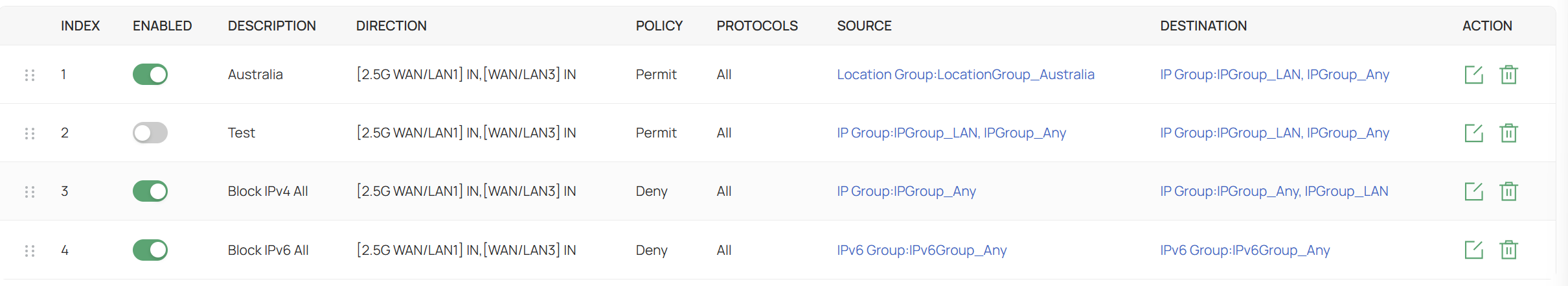
Using the rules as enabled above, when connecting via OpenVPN (on both an iPad or Windows 11 PC), the connection is established but it is not possible to access any local network devices. However if i disable the "Block IPv4 All" rule then I can access all the local devices, or if I enable the "Test" rule I can also access all the local devices.
I have also attempted to create other rules (e.g. ports) but none of those have worked either. It is as if only the IP Group rules are matched and others ignored.
Any suggestions or insights would be welcome.
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
That is not a particularly good solution to your problem - by adding a specific "allow" rule for an IP range, you open yourself up to IP spoofing attacks - basically anything masquerading as that IP will be allowed in.
For WAN In rules, its always best to avoid a specific allow rule
The better way to achieve what you want, is to change your deny all rule to a location group. Add every country except the ones you want to a new location group, and use that as the source for the WAN in deny. That allows the implicit "that came from a VPN i know is properly established" traffic flow for your VPN through the stateful firewall without specifically adding it
- Copy Link
- Report Inappropriate Content
What do you want to achieve by creating an ACL? You have just created a block of everything from the internet? Why do you have it?
Can you explain a little bit what end result you wan
- Copy Link
- Report Inappropriate Content
Thanks, to answer your question basically i deny everything and only allow the traffic I want on the network. Given that all LAN initiated internet traffic is fine I am ok with this setup.
Having said that I believe I have solved the problem, basically from thinking about your question!
I needed to add the LAN IP Subnet of OpenVPN to the rule - once I had done that it operates as expected. For some reason I thought that the traffic would hit the ACL with the WAN IP and not the private IP address of the OpenVPN client.
Cheers.
- Copy Link
- Report Inappropriate Content
That is not a particularly good solution to your problem - by adding a specific "allow" rule for an IP range, you open yourself up to IP spoofing attacks - basically anything masquerading as that IP will be allowed in.
For WAN In rules, its always best to avoid a specific allow rule
The better way to achieve what you want, is to change your deny all rule to a location group. Add every country except the ones you want to a new location group, and use that as the source for the WAN in deny. That allows the implicit "that came from a VPN i know is properly established" traffic flow for your VPN through the stateful firewall without specifically adding it
- Copy Link
- Report Inappropriate Content
Valid point and interesting suggestion.
I only need to enable the rule when I am traveling so depending on location (country) that could open up some exposure too.
Either way a consideration none the less.
- Copy Link
- Report Inappropriate Content
Not really, the stateful firewall doesnt work like that
Adding an explicit allow - bad idea in general
Not adding countries in a location list - traffic will still be dropped by the firewall form the countries you allow other than hosted services on the gateway like VPNs/ Stateful firewall track traffic patters, if the VPN is established to the gateway, it will allow it without you having to "allow it"
By default, everything is blocked incoming anyway
- Copy Link
- Report Inappropriate Content
Apologies, I was agreeing that the explicit IP Allow was a bad approach.
Thanks for the clarification on the preferred rule as I misunderstood the first time it was mentioned (been a long year for a tired old brain).
Appreciate the time to respond by both of you and have made the appropriate changes.
Cheers.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 349
Replies: 6
Voters 0
No one has voted for it yet.
