Problems with mDNS across VLANs
Problems with mDNS across VLANs
I'm using gateway ER8411 v1.0 (firmware 1.3.1) on software controller v5.15.20.20.
I have three separated VLANs:
- VLAN1: home devices (192.168.1.0/24)
- VLAN2: shared devices (e.g. printers) (192.168.2.0/24)
- VLAN3: work devices (192.168.3.0/24)
I would like the printers on VLAN2 to be discoverable on the other two VLANs and have setup mDNS accordingly on the controller. I can see with Wireshark that the mDNS requests and answers are transferred between VLANs, but as already stated here, the process seems to corrupt the packets so that the clients won't be able to discover the printers (discovery by a client works only if the client is on VLAN2).
Here is a mDNS answer I see in Wireshark from a printer I want to add when the client is on VLAN2 (the printer is correctly discovered by Windows 11):
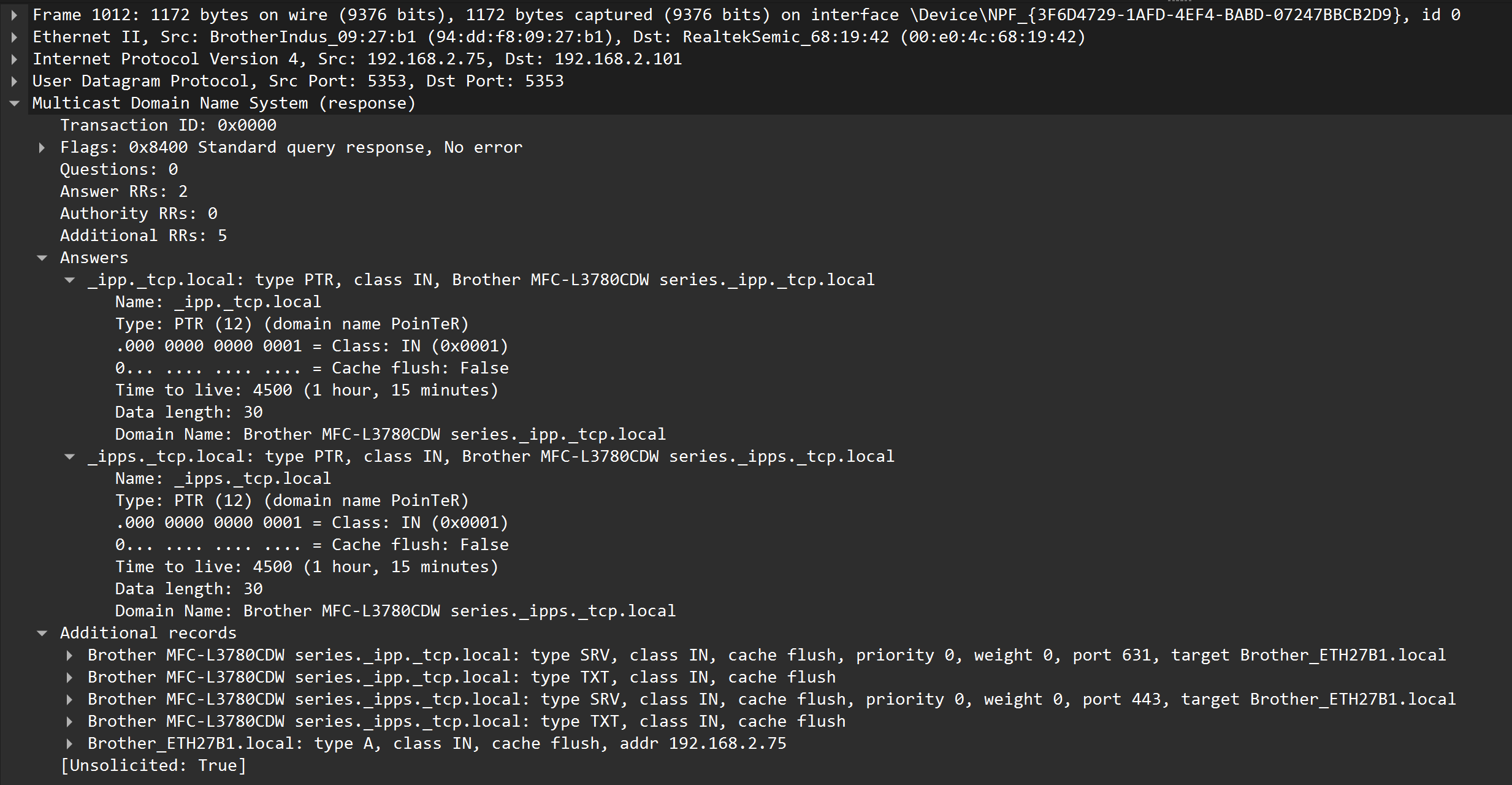
And here is what I get if I am on VLAN1 with the mDNS repeater enabled (the printer is not discovered by Windows 11):
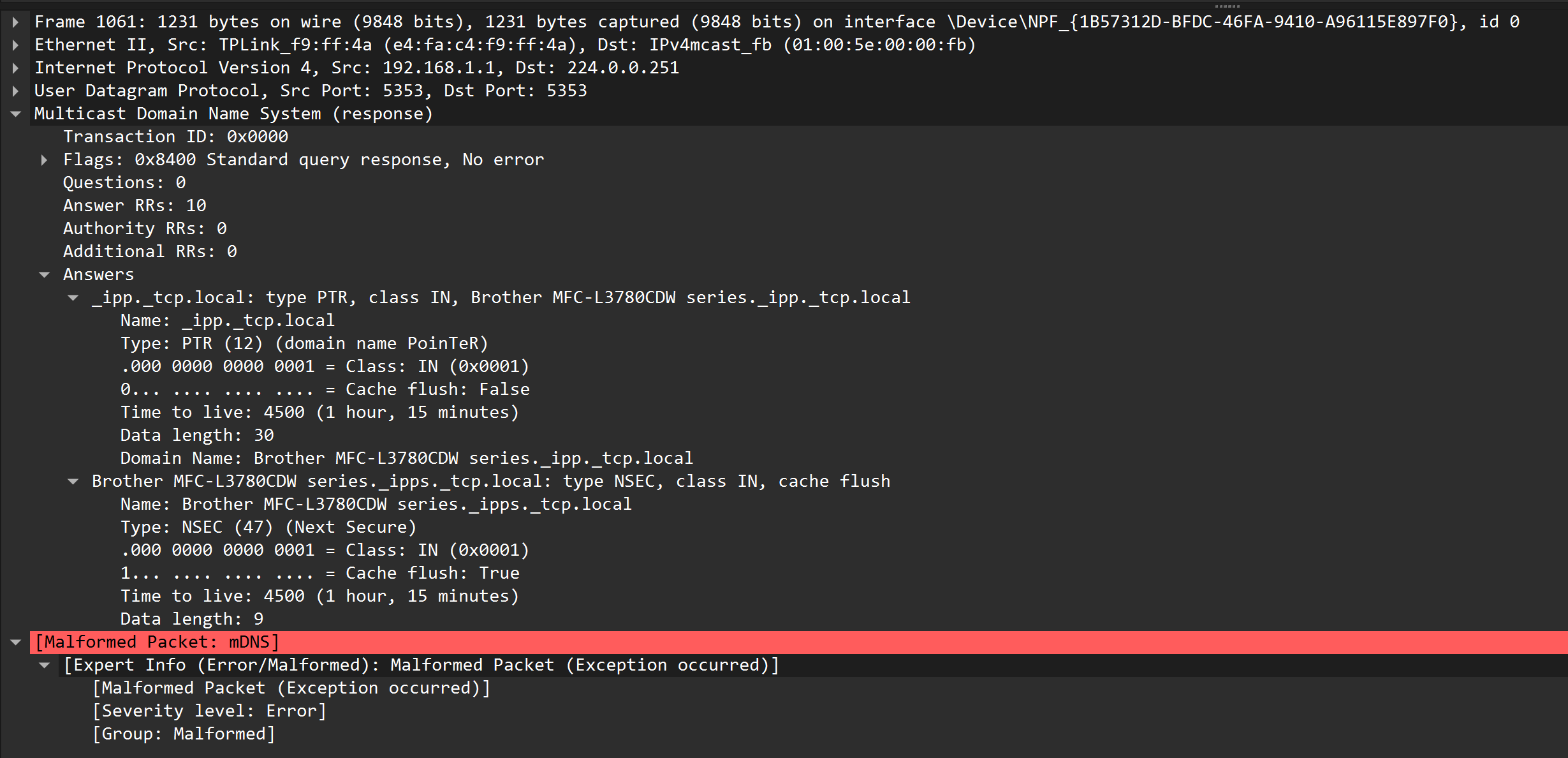
Notably, we are missing the "Additional records" where the IP address of the printer can be found.
Is any fix for this issue coming up...?
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
@Clive_A OK, so I managed to patch avahi-app-0.8 on my pfSense (v2.8.0) with this workaround suggested here and it worked: now my printers are correctly seen on all my VLANs! ![]()
After a ton of tcpdump/iperf/nc investigations, it is well apparent to me that the ER8411 is using avahi 0.8 (or earlier) for mDNS forwarding because I could see the exact same NSEC record packet malformations using either the ER8411 with firmware v1.3.1 or pfSense with avahi-app-0.8. It is important to mention that tose malformations occur only for NSEC records, so yes mDNS forwarding on the ER8411 with firmware v1.3.1 will work for mDNS-published services that don't use NSEC.
So TP-Link could probably fix this specific problem by using the same patch as me, but I guess the reasonable choice for them would rather be to wait for the official avahi 0.9.1 milestone (the one scheduled to include a fix), which has no due date yet...
I don't know all the exact repercussions of disabling NSEC forwarding with the patch, but from what I gather they seem quite mild. We can see from this commit from another project that an option for disabling this workaround is possible, so that could be another way to go for TP-Link (i.e., patching with the workaround but include an option in the mDNS settings for enabling or disabling this workaround).
- Copy Link
- Report Inappropriate Content
I also had the idea to setup a CUPS server on VLAN2 and add my printers to it: there are no NSEC records published by CUPS, so mDNS forwarding is working flawlessly and it's much less hassle than patching Avahi with a work-around.
- Copy Link
- Report Inappropriate Content
Have you run the troubleshooting and checked if there is anything wrong?
What are the results of each step in the guide?
From the screenshots, it looks like you simply did not configure the protocols but simply "enabled" them and expect it to work.
The mDNS is not plug-and-play. For other protocols not included, you gotta manually config.
- Copy Link
- Report Inappropriate Content
@Clive_A Yes, I saw and have read this guide before posting and, to the contrary, we can see from my screenshots that the desired protocols have been configured, the mere proof being that the desired mDNS broadcasts *are* repeated and forwarded by the gateway between VLANs, but the screenshots also show that those broadcasts seem to be somehow broken by the router. I have no firewall ACLs and VLANs can ping each other.
- Copy Link
- Report Inappropriate Content
shrodi wrote
@Clive_A Yes, I saw and have read this guide before posting and, to the contrary, we can see from my screenshots that the desired protocols have been configured, the mere proof being that the desired mDNS broadcasts *are* repeated and forwarded by the gateway between VLANs, but the screenshots also show that those broadcasts seem to be somehow broken by the router. I have no firewall ACLs and VLANs can ping each other.
A diagram with IP specified.
Protocols have been set for the mDNS.
Is that possible for a remote desktop or your backup, so we can import and investigate? Might need your assistance to reproduce this issue.
- Copy Link
- Report Inappropriate Content
@Clive_A I would be pleased to help in anyway I can.
I've tried to send you a link in private to an online folder containing a controller .cfg backup file and some screenshots with a Readme.md file with some explanations, but the system told me you needed to follow me first for me to be able to message you.
- Copy Link
- Report Inappropriate Content
@Clive_A Here's an update. I wanted to create a live demo of what happens to the packets from source vlan to destination vlan, and what I observed is that sometimes they are forwarded correctly, without being malformed, and are then picked up by the client. However, strangely, I have two printers and 1) only one of them gets its packets malformed and 2) the second one seems to always have good packets forwarded, but is not discovered. I will continue to investigate and update.
- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
shrodi wrote
@Clive_A I would be pleased to help in anyway I can.
I've tried to send you a link in private to an online folder containing a controller .cfg backup file and some screenshots with a Readme.md file with some explanations, but the system told me you needed to follow me first for me to be able to message you.
You can send it now.
- Copy Link
- Report Inappropriate Content
shrodi wrote
I do not have this information. And if I have, I am not able to share any information regarding the system components.
- Copy Link
- Report Inappropriate Content
@Clive_A OK, so I managed to patch avahi-app-0.8 on my pfSense (v2.8.0) with this workaround suggested here and it worked: now my printers are correctly seen on all my VLANs! ![]()
After a ton of tcpdump/iperf/nc investigations, it is well apparent to me that the ER8411 is using avahi 0.8 (or earlier) for mDNS forwarding because I could see the exact same NSEC record packet malformations using either the ER8411 with firmware v1.3.1 or pfSense with avahi-app-0.8. It is important to mention that tose malformations occur only for NSEC records, so yes mDNS forwarding on the ER8411 with firmware v1.3.1 will work for mDNS-published services that don't use NSEC.
So TP-Link could probably fix this specific problem by using the same patch as me, but I guess the reasonable choice for them would rather be to wait for the official avahi 0.9.1 milestone (the one scheduled to include a fix), which has no due date yet...
I don't know all the exact repercussions of disabling NSEC forwarding with the patch, but from what I gather they seem quite mild. We can see from this commit from another project that an option for disabling this workaround is possible, so that could be another way to go for TP-Link (i.e., patching with the workaround but include an option in the mDNS settings for enabling or disabling this workaround).
- Copy Link
- Report Inappropriate Content
shrodi wrote
@Clive_A OK, so I managed to patch avahi-app-0.8 on my pfSense (v2.8.0) with this workaround suggested here and it worked: now my printers are correctly seen on all my VLANs!
After a ton of tcpdump/iperf/nc investigations, it is well apparent to me that the ER8411 is using avahi 0.8 (or earlier) for mDNS forwarding because I could see the exact same NSEC record packet malformations using either the ER8411 with firmware v1.3.1 or pfSense with avahi-app-0.8. It is important to mention that tose malformations occur only for NSEC records, so yes mDNS forwarding on the ER8411 with firmware v1.3.1 will work for mDNS-published services that don't use NSEC.
So TP-Link could probably fix this specific problem by using the same patch as me, but I guess the reasonable choice for them would rather be to wait for the official avahi 0.9.1 milestone (the one scheduled to include a fix), which has no due date yet...
I don't know all the exact repercussions of disabling NSEC forwarding with the patch, but from what I gather they seem quite mild. We can see from this commit from another project that an option for disabling this workaround is possible, so that could be another way to go for TP-Link (i.e., patching with the workaround but include an option in the mDNS settings for enabling or disabling this workaround).
Wonderful to know.
As the dev has noticed your reply and information. We will look into it.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 2246
Replies: 17
Voters 0
No one has voted for it yet.
