Question about New SSH Option in Omada Hardware Controller
Question about New SSH Option in Omada Hardware Controller
Tags:
#Firmware Update
#Controller
Hi TP-Link Omada Team,
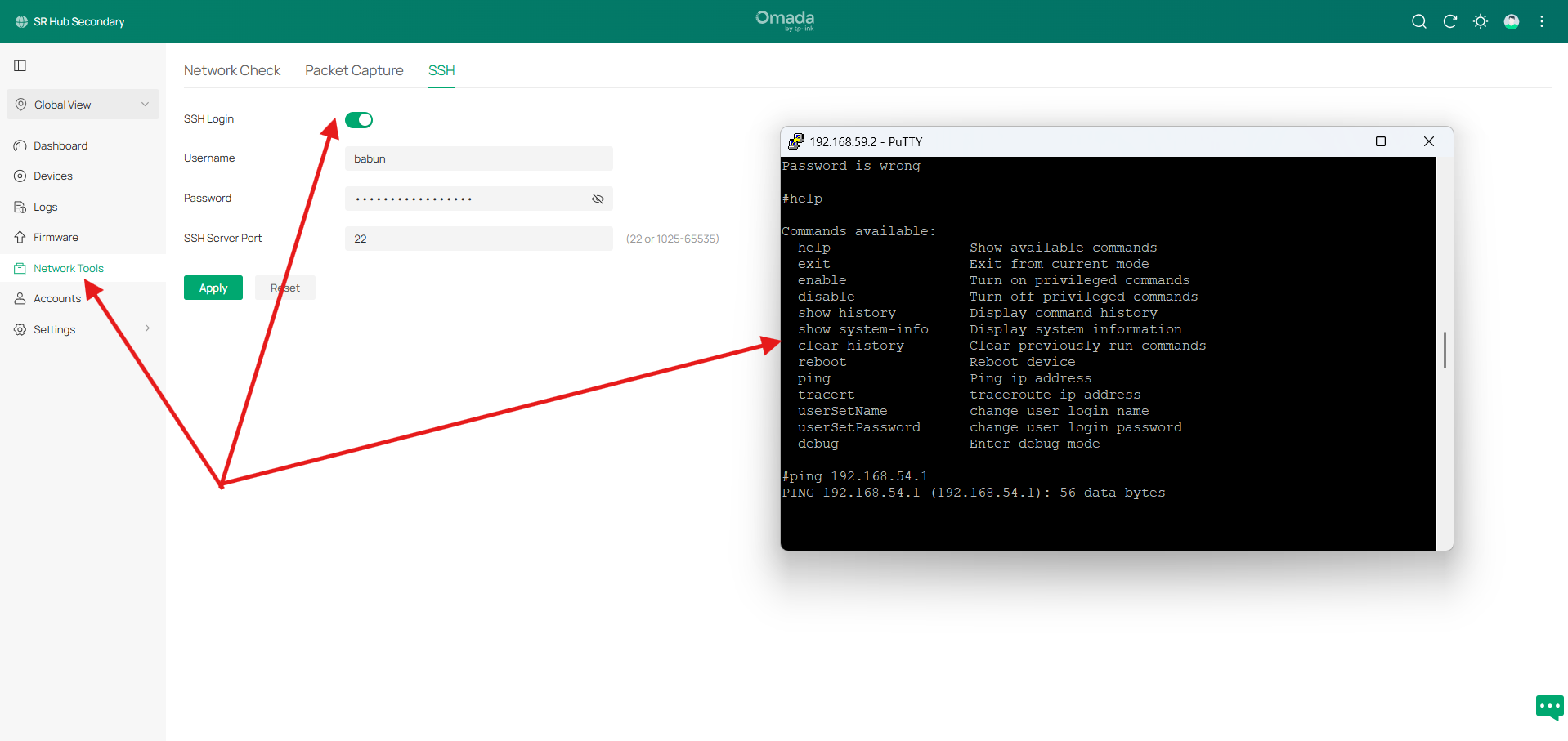
I noticed that the Omada Hardware Controller now shows a new SSH option under the Network Tools section (screenshot attached). Could you please provide a brief explanation of this feature? Specifically:
-
What is the intended use of this SSH option?
-
Are there any security considerations we should be aware of?
-
How does it differ from the regular device management options?
Thank you for your guidance!
Omada & VIGI | Using at 4 Locations | Controller: V6.1.0.10 (Linux) | GW: ER7206 | SW: SG2428P & SG2210P | APs: 2 × EAP610 | WAN: Jio&Airtel | NVR2016H.
1 Accepted Solution
