Kasa HS200 ARP poisoning
This pas week I spent 3 days troubling shooting why certain systems in my home network would either randomly drop off the internet or consistently fail to connect to the internet.
I went as far as to restore my firewall from backup and some of the VMs having consistent issues.
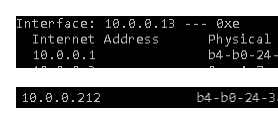
Finally after doing some digging, while looking at the ARP tables on one of the VMs having persitent connectivity issues... I noticed the MAC for my gateway on said VM was showing an odd MAC address in it's ARP table.
I did some more research to see just what MAC it was and what was causing the issue. After some network huning and reviewing of my documentation and DHCP reservation settings I was able to discover it was my second Hallway light switch, a TP-LINK KASA HS200. It's DHCP reservation ended in .212 and I am able to ping the device and control it via that IP address. But it was also broadcasting that it "Owns" .1 my Gateway IP and poisoning my ARP tables on random devices.
I've set static ARP entries on a few Windows VMs and the issue is fixed for those, but things like my 3D printer and other devices don't have such capabilities. But that isn't the biggest concern of mine.
I've seen where cheap IoT devices can do this while attempting to advertise themselves as a cloud gateway for other IoT devices on the network. Thus I'm not sure if this is the case here or if my device has been compromised.
I'm going to look into factory reseting the device / wiping it and reflashing the firmware (if possible). But I am also going to start down the correct path of isolating these troublesome devices into their own VLAN.
Has anyone else had this issue? Is this a firmware flaw or a compromised device? And if it's a firmware flaw, has anyone seen a fix?
Thank you