IPsec VPN remote client can't access local network
I've set up an IPsec VPN for a laptop as remote client. The connection can be established but I can access only the internal IP address of the ER7406 gateway from my laptop - not any IP address in the local LAN.
The setting of the VPN: Local Network Type = Network, Local Networks: LAN
The local network LAN is bound the internal IP address of the gateway - an address in a 192.168.128.0/24 network used as local internal network.
The Routing settings/Routing Table show: Destination IP = 192.168.128.0, Subnet Mask = 255.255.255.0, Next Hop = 0.0.0.0, Interface = LAN (the internal IP address of the gateway).
Therefore I was assuming I can address any IP address in the 192.168.128.0-network from my laptop connected via VPN - but it doesn't.
Any hint how to solve this limitation?
- Copy Link
- Subscribe
- Bookmark
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
- Copy Link
- Report Inappropriate Content
Accessing a Windows PC in my local network is not the issue. I want to access Linux servers including a NAS.
This was possible with my previous router, it died a few months ago and was replaced by a TP-Link ER7406.
Therefore I assume a missing or wrong setting of the ER7406 is the reason for not being able to access any other IP address in my local network than the internal IP address of the ER7406.
To add: my remote VPN client is a Windows computer and I ran "tracert 192.128.0.10" addressing a Linux server. tracert showed the internal IP address of the ER7406 - so far the routing went well but not beyond.
- Copy Link
- Report Inappropriate Content
I found an open issue of the routing to IPsec VPN clients:
- pinging the internal IP address (192.168.0.250) of the ER7406 from my remote client (192.168.129.10) shows a response - the ER7406 knows responses must go thru a specific IPsec tunnel.
- pinging/tracert-ing a server in my local network (e.g. 192.168.0.25) from my remote client does not show a response: the server sends the response to 192.168.0.250 (= ER7406) as the gateway of the local 192.168.0.0 network - does ER7406 know how to route it?
- I pinged my remote client (192.168.129.10) from a computer in my local network (e.g. 192.168.0.120): no response.
- I pinged my remote client (192.168.129.10) from ER7406 by System Tools -> Diagnostics: no response
Does the ER7406 know how to route a packet to 192.168.129.10?
- Its Routing Table doesn't show a route for 192.168.129.0.
- The settings of the IPsec VPN include "Mode: Client-to-LAN" and "IP Address Pool: 192.168.129.0/24" - is this sufficient for the routing from the local network to the remote network?
- (I added a static routing to 192.168.129.0 to the Routing Table but this did not help.)
- Copy Link
- Report Inappropriate Content
Capricorn61 wrote
I found an open issue of the routing to IPsec VPN clients:
- pinging the internal IP address (192.168.0.250) of the ER7406 from my remote client (192.168.129.10) shows a response - the ER7406 knows responses must go thru a specific IPsec tunnel.
- pinging/tracert-ing a server in my local network (e.g. 192.168.0.25) from my remote client does not show a response: the server sends the response to 192.168.0.250 (= ER7406) as the gateway of the local 192.168.0.0 network - does ER7406 know how to route it?
- I pinged my remote client (192.168.129.10) from a computer in my local network (e.g. 192.168.0.120): no response.
- I pinged my remote client (192.168.129.10) from ER7406 by System Tools -> Diagnostics: no response
Does the ER7406 know how to route a packet to 192.168.129.10?
- Its Routing Table doesn't show a route for 192.168.129.0.
- The settings of the IPsec VPN include "Mode: Client-to-LAN" and "IP Address Pool: 192.168.129.0/24" - is this sufficient for the routing from the local network to the remote network?
- (I added a static routing to 192.168.129.0 to the Routing Table but this did not help.)
IPsec never needs manual routing.
I cannot comment on this without a diagram of your network with IP specified on it.
Pinging the gateway, and it works, which means the inter-site IPsec works properly. When it reaches the peer site but does not reach the other clients on that site, that's a problem with your local config problem.
For the regular Omada setup, two Omada IPsec, I do not see this behavior.
- Copy Link
- Report Inappropriate Content
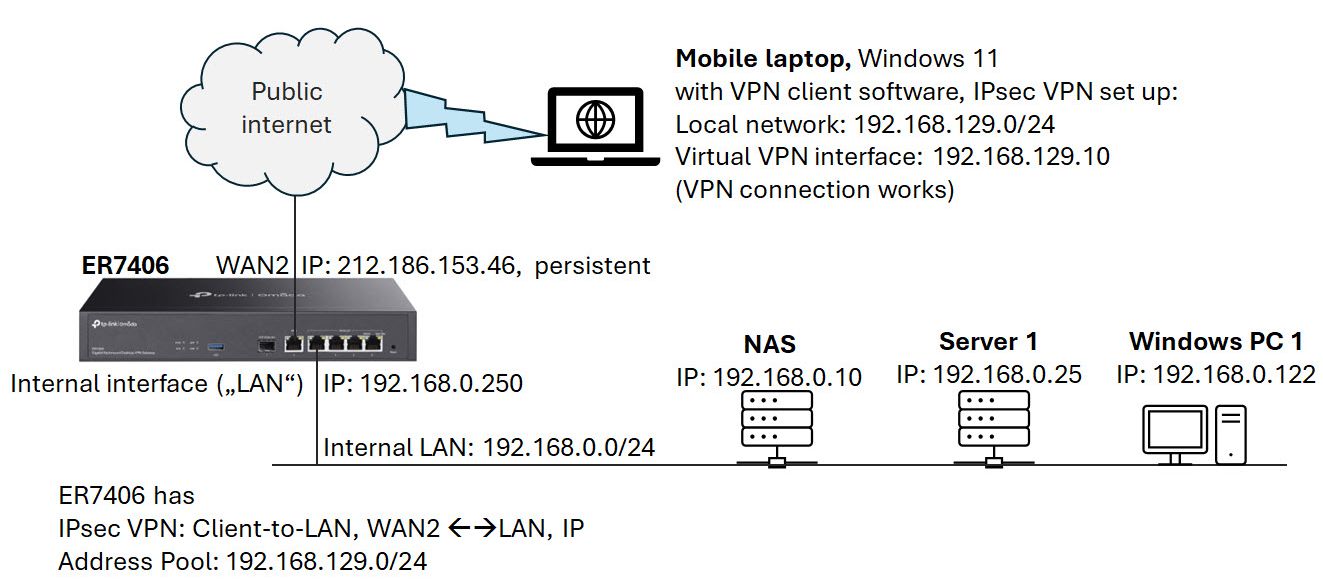
This is a sketch of my network, all devices mentioned in my posting are shown with their IP address.
The goal is to access NAS or Server 1 from the mobile laptop.
- Copy Link
- Report Inappropriate Content
Capricorn61 wrote
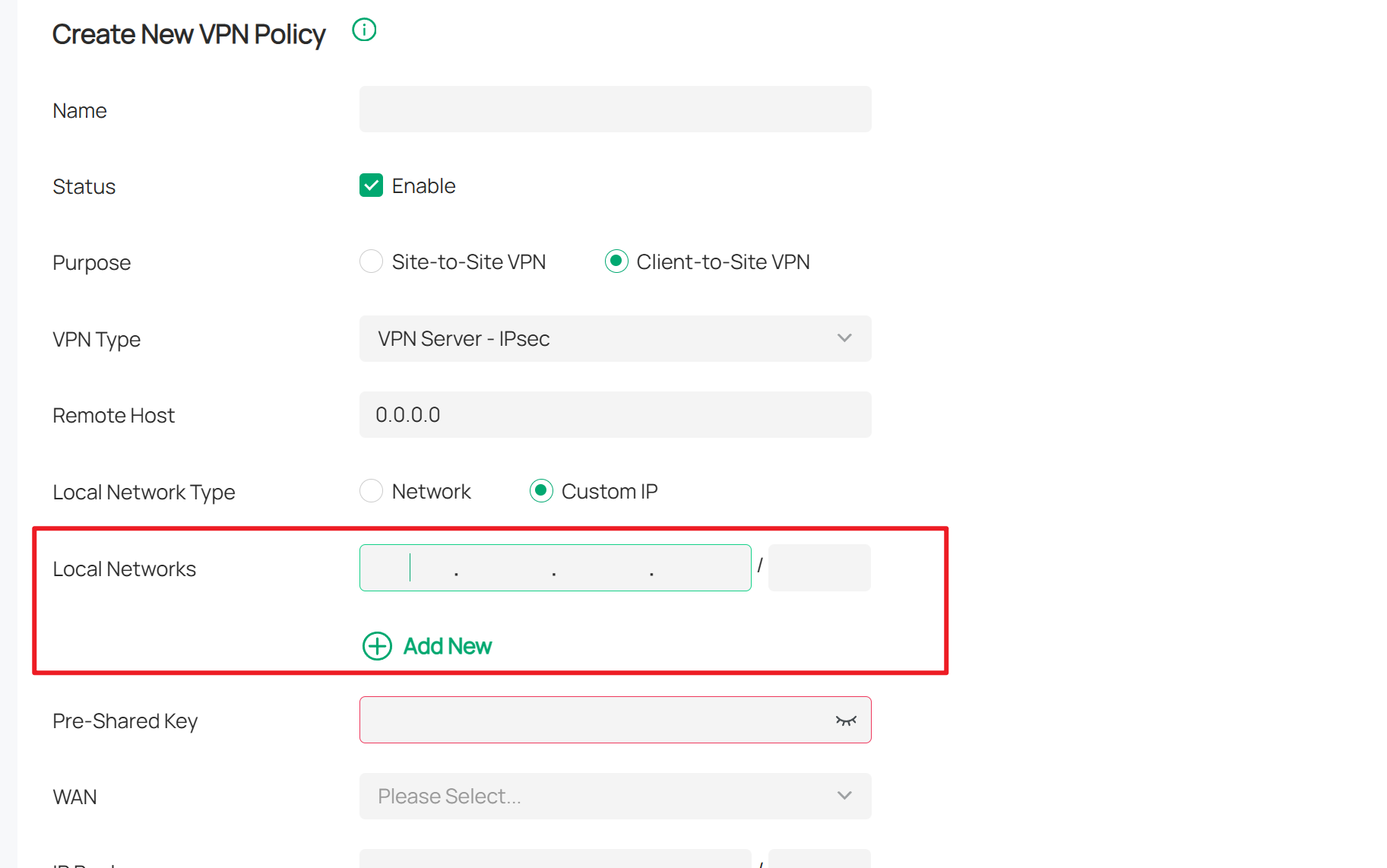
This is a sketch of my network, all devices mentioned in my posting are shown with their IP address.
The goal is to access NAS or Server 1 from the mobile laptop.
The VPN local network should be 192.168.0.0/24.
- Copy Link
- Report Inappropriate Content
Unfortunately it does not help: I've set Local Network Type to Custom IP and the single entry of Local Networks is 192.128.0.0/24
And the IP Address Pool of the VPN is set to 192.168.129.0/24.
Trying to access devices in this local network from the remote client shows the same as before:
- pinging 192.128.0.250 works
- pinging or trying to access any server does not work
While having an active VPN I checked the VPN -> IPSec / IPsec SA table of the ER7406: it shows the correct name of the IPsec Policy with "in" and "out" direction and the data flow is 192.168.0.0/24 <-- 192.168.129.10/32 and vice versa. This looks ok.
Based on that I changed the IP Address Pool of the VPN to 192.168.129.10/32 - but it did not help.
- Copy Link
- Report Inappropriate Content
Information
Helpful: 0
Views: 471
Replies: 7
Voters 0
No one has voted for it yet.
